Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: David Harley I have, at best, an uneasy relationship with Facebook. To...
Source: securityboulevard.com - Author: Marc Handelman Yazhou Tu, Liqun Shan, Md Imran Hossen, Sara Rampazzi, Kevin...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Ziad Ghalleb GitGuardian Secrets Detection More detectors = more secrets caught This...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
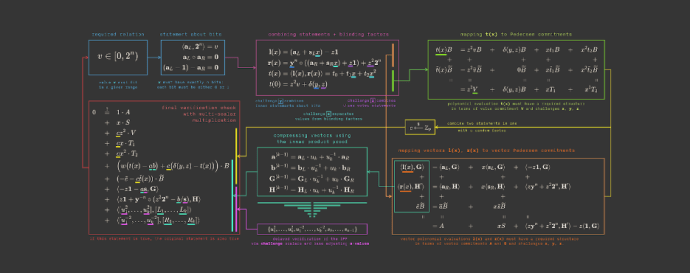
Source: securityboulevard.com - Author: Trail of Bits By Jim Miller We’ve updated ZKDocs with four new...
Source: securityboulevard.com - Author: Avast Blog No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Cyborg Security As we close out 2023, we at Security Boulevard wanted...
Source: securityboulevard.com - Author: Ahona Rudra You drafted an email, hit the ‘send’ button, but forgot...
Source: securityboulevard.com - Author: Rohan Timalsina In a groundbreaking revelation, researchers from Vrije Universiteit Amsterdam have...
Source: securityboulevard.com - Author: Joao Correia Multiple UEFI vulnerabilities can lead to Linux, Windows, and Mac...
Source: securityboulevard.com - Author: Matthew Rosenquist I have been an active volunteer as part of corporate...
Source: securityboulevard.com - Author: Michael Toback Understanding the Basic Concept of VLANs Virtual Local Area Networks,...
Why a Zero Trust Security Policy Matters and Steps to Implementation – Source: securityboulevard.com
Source: securityboulevard.com - Author: Michelle Ofir Geveye Understanding Zero Trust Traditionally, cybersecurity operated on a simple...
Source: securityboulevard.com - Author: Ahona Rudra Developers at Yahoo have been busy formulating guidelines for bulk...
Source: securityboulevard.com - Author: Rohan Timalsina Vim, a powerful and widely used text editor, has recently...
Source: securityboulevard.com - Author: TuxCare Team Sophisticated Internet of Things (IoT) technologies transformed the cybersecurity systems...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Wajahat Raja In light of recent GambleForce attacks, a new threat actor...
Source: securityboulevard.com - Author: Tom Eston In our last episode of the year, we replay our...
Source: securityboulevard.com - Author: Marc Handelman Full Presenters List: Rose Ceccio, Sophie Stephenson, Varun Chadha, Danny...
Source: securityboulevard.com - Author: hrbrmstr Ref AP News: https://apnews.com/article/iowa-summer-ebt-food-assistance-0e878c5c0fc9dd0dd55622cb22a82561. Iowa has decided not to participate in...
Source: securityboulevard.com - Author: David Harley Having found myself roped into assisting as co-administrator a couple...
Source: securityboulevard.com - Author: Michael Toback Imagine standing at the entrance to a vault where your...
Source: securityboulevard.com - Author: Marc Handelman Full Presenter List: Sophie Stephenson, Majed Almansoori, Pardis Emami-Naeini, Rahul...
Source: securityboulevard.com - Author: Riddika Grover Recent attacks have demonstrated a significant growth in Zero Days...
Source: securityboulevard.com - Author: Axio Cloud Security, Governance and Skills in 2024 Step 1 of 6...
Source: securityboulevard.com - Author: Cavelo Blog And the real-life challenges midsized enterprises are juggling as they...


![The (Face-)Book of Mammon [book review] – Source: securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2023/12/109252/the-face-book-of-mammon-book-review-source-securityboulevard-com.jpg)