Source: securityboulevard.com - Author: Gary Warner Earlier this month, Microsoft’s Digital Crimes Unit was featured in...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Rajan Sodhi As we wrap up 2023, let’s take a moment to...
Source: securityboulevard.com - Author: Michael Toback Understanding MFA: A Security Necessity for Small Businesses In an...
Source: securityboulevard.com - Author: Guest Expert Daniel Kelley Sponsorships Available Daniel Kelley is a security researcher...
Source: securityboulevard.com - Author: Marc Handelman Authors/Presenters: Shimaa Ahmed, Yash Wani, Ali Shahin Shamsabadi, Mohammad Yaghin,...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Marc Handelman Cloud Security, Governance and Skills in 2024 Step 1 of...
Source: securityboulevard.com - Author: Trail of Bits By Max Ammann Behind Ethereum’s powerful blockchain technology lies...
Source: securityboulevard.com - Author: Yuzuka As we close out 2023, we at Security Boulevard wanted to...
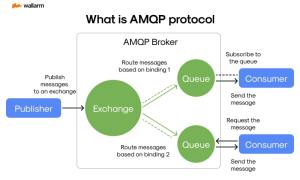
Source: securityboulevard.com - Author: Ivan Novikov The Initial Overview: Learning about MQTT & AMQP In the...
Source: securityboulevard.com - Author: Tim Walker Welcome to the TuxCare Weekly Blog Wrap-Up – your go-to...
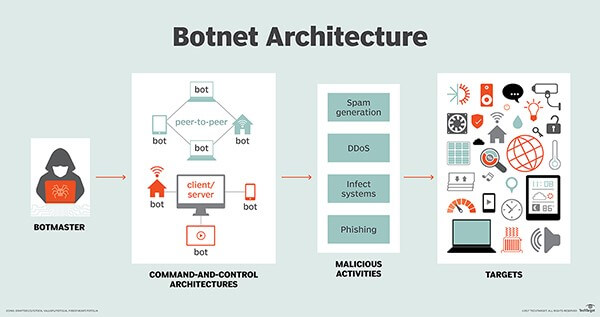
Source: securityboulevard.com - Author: Venkatesh Sundar If your device suddenly behaves like a re-animated zombie, you...
Source: securityboulevard.com - Author: Shikha Dhingra A recent study by Rubrik, a US-based data security firm,...
Source: securityboulevard.com - Author: Marc Handelman Cloud Security, Governance and Skills in 2024 Step 1 of...
Source: securityboulevard.com - Author: Sarah Hunter-Lascoskie While businesses must prevent a variety of fraud types, the...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Amy Luby, VP Ecosystems at Seceon As the curtains draw close on...
Source: securityboulevard.com - Author: Kaseya Woohoo! What an exciting year 2023 turned out to be. Right...
Source: securityboulevard.com - Author: Jenn Jeffers If you missed our recent webinar, “Foreseeing the Future Threatscape:...
Source: securityboulevard.com - Author: Marc Handelman Jonathan Prokos, Neil Fendley, Matthew Green, Roei Schuster, Eran Tromer,...
Source: securityboulevard.com - Author: Rob Burgundy Rob Burgundy Lead Anchor, WMMX Rob Burgundy, the much better-looking...
Source: securityboulevard.com - Author: Marc Handelman Authors/Presenters: Varun Gandhi, Sarbartha Banerjee, Aniket Agrawal, Adil Ahmad, Sangho...
Source: securityboulevard.com - Author: Richi Jennings Operation Triangulation research uncovers new details of fantastic attack chain.A...
Source: securityboulevard.com - Author: Maycie Belmore Welcome to the “Life in the Swimlane” blog series. Here...
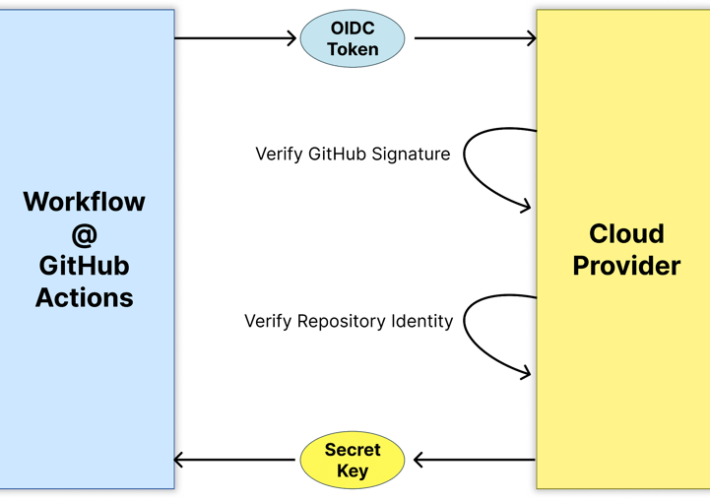
Source: securityboulevard.com - Author: Gal Ofri In part 2 of the series, we dived into the...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: Marc Handelman No one specifically Someone on our general security team A...
Source: securityboulevard.com - Author: bacohido By Byron V. Acohido Russia’s asymmetrical cyber-attacks have been a well-documented,...
Source: securityboulevard.com - Author: Votiro Team No matter which airport you travel through or how many...