Source: securityboulevard.com - Author: Gaurav Banga Here’s a scenario security teams increasingly face. A user—or an...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: Sofia Naer Introduction On July 16, 2025, Europol revealed the details of...
Source: securityboulevard.com - Author: Jeffrey Burt Five months after the future of the CVE program was...
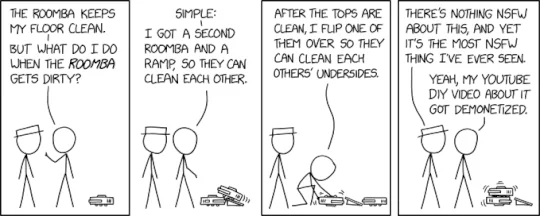
Source: securityboulevard.com - Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe,...
Source: securityboulevard.com - Author: Avast Blog DoorDash has become a staple for more than 40 million...
Source: securityboulevard.com - Author: Audian Paxson When a North Korean scammer asks Claude "what is a...
Source: securityboulevard.com - Author: Richi Jennings Roasting Redmond for Kerberoasting: “Like an arsonist selling firefighting services,”...
Source: securityboulevard.com - Author: Alan Shimel Artificial intelligence is no longer just another tool in the...
Source: securityboulevard.com - Author: Alan Shimel Fletcher Heisler, CEO of Authentik Security, covers the evolution of...
Source: securityboulevard.com - Author: Mark Allers For more than two decades, Comply-to-Connect (C2C) has been a...
Source: securityboulevard.com - Author: Steven J. Vaughan-Nichols Billions (No, that’s not a typo, Billions with a...
Source: securityboulevard.com - Author: Matthew Rosenquist Knowing when to hire a CISO is a challenging...
Source: securityboulevard.com - Author: Amrit Talapatra An in-depth analysis of common JSON Web Token (JWT) mistakes,...
Source: securityboulevard.com - Author: Marc Handelman via the geologic humor & dry-as-the-taiga wit of Randall Munroe,...
Source: securityboulevard.com - Author: Jeffrey Burt Security investigators from Google said UNC6395 hackers spent several months...
Source: securityboulevard.com - Author: Dragos Josanu In total, including third-party CVEs, in this Patch Tuesday edition,...
Source: securityboulevard.com - Author: Naomi Buckwalter Contrast customers get certainty in moments when everyone else is...
Source: securityboulevard.com - Author: Michael Vizard Cisco at its Splunk .conf conference today added a series...
Source: securityboulevard.com - Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe,...
Source: securityboulevard.com - Author: Jeffrey Burt The Chinese state-sponsored group APT41 is accused of using a...
Source: securityboulevard.com - Author: Michael Vizard UltraViolet Cyber has acquired the application security testing services arm...
Source: securityboulevard.com - Author: Michael Vizard Palo Alto Networks this week revealed it will update its...
Source: securityboulevard.com - Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe,...
Source: securityboulevard.com - Author: Roman Kadinsky, Cofounder, President & COO, HYPR Self-service password reset (SSPR) and...
Source: securityboulevard.com - Author: FireTail - AI and API Security Blog Sep 05, 2025 - Lina...
Source: securityboulevard.com - Author: Lauren Yacono As federal agencies accelerate Zero Trust adoption, maintaining system integrity...
Source: securityboulevard.com - Author: Gary Warner A new round of mobile phish is imitating the State...
Source: securityboulevard.com - Author: Mary Henry Scaling Kubernetes isn’t just about launching containers—it’s about choosing support...
Source: securityboulevard.com - Author: Jeffrey Burt Cloudflare, Palo Alto Networks, and Zscaler are the latest among...
Source: securityboulevard.com - Author: Michael Vizard A survey of 264 professionals that maintain websites based on...