Recommendations of the National Institute of Standards and Technology Computer security incident response has become an...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
NIST
Purpose and Context: The CIRP establishes the necessary framework for responding to cybersecurity incidents, focusing on...
Generative Artificial Intelligence Profile The document "NIST AI 600-1, Artificial Intelligence Risk Management Framework: Generative Artificial...
Incident response is a critical part of cybersecurity risk management and should be integrated across organizational...
The Multi-State Information Sharing & Analysis Center (MS-ISAC) is offering this guide to participants of the...
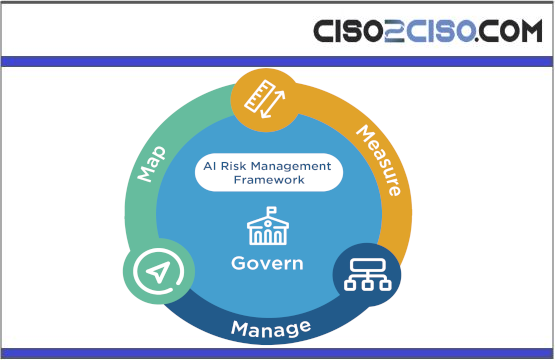
The Playbook provides suggested actions for achieving the outcomes laid out inthe AI Risk Management Framework...
This publication aims to help educate readers about the security standards included in the Health Insurance...
Recover “The development and implementation of plans, processes and procedures for recovery and full restoration in...
In our data-driven world, organizations must prioritize cybersecurity as part of their business risk management strategy....
Malware, also known as malicious code, refers to a program that is covertly inserted into another...
Phishing cyber threats impact private and public sectors both in the United States and internationally. Embedded...
Data classification is the process an organization uses to characterize its data assets using persistent labels...
During its investigations, ANSSI analyzed several attack mode 1 compromise chains used for espionage including purposes....
AI systems may be subject to specific applicable legal and regulatoryrequirements. Some legal requirements can mandate...
Through a series of direct engagements with higher education cybersecurity and research security communities, as well...
Operating system (OS) virtualization provides a separate virtualized view of the OS to each application, thereby...
1.1 PurposeThis publication serves as a starting-point for those new to information security as well as...
The CIA triad represents the three pillars of information security: confidentiality, integrity, and availability, as follows....
This publication provides guidance for federal agencies and organizations to develop and manage a lifecycle approach...
Nelson Mandela famously said, “Remember to celebrate milestones as you prepare for the road ahead.”This year,...
Cybersecurity risks are a fundamental type of risk for all organizations to manage. Potential impacts to...
The principles of zero trust, as described in NIST Special Publication (SP) 800-207, havebecome the guiding...
Reports on Computer Systems TechnologyThe Information Technology Laboratory (ITL) at the National Institute of Standards and...
The predominant application architecture for cloud-native applications consists of multiple microservices with a centralized application infrastructure,...
This document summarizes research performed by the members of the NIST Cloud Computing Forensic Science Working...
Guide_for_Developing_Security_Plans_1654263507Descarga
Guide_to_a_Secure_Enterprise_Network_Landscape_1660433425Descarga
Executive SummaryThe National Institute of Standards and Technology (NIST) has traditionally published secureconfiguration guides for Apple...
AbstractThis publication describes the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework (NICE Framework), a...