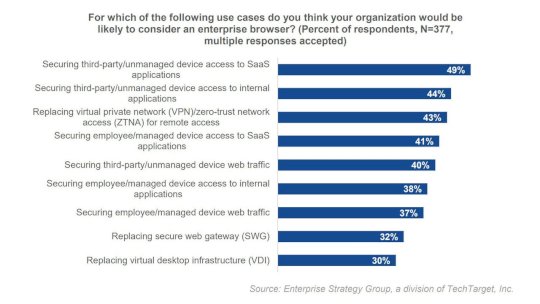
Source: www.darkreading.com - Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Dark Reading Security
Source: www.darkreading.com - Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Shimon Modi Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You...
Source: www.darkreading.com - Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Chad E. LeMaire Please enable cookies. Sorry, you have been blocked You...
Source: www.darkreading.com - Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you...
Source: www.darkreading.com - Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Brent Stackhouse Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you...
Source: www.darkreading.com - Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Sachin Suryawanshi Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You...
Source: www.darkreading.com - Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Tara Seals Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Please enable cookies. Sorry, you have been blocked You are unable to...
Source: www.darkreading.com - Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you...
Source: www.darkreading.com - Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You...
Source: www.darkreading.com - Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have...
Source: www.darkreading.com - Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked...
Source: www.darkreading.com - Author: Durgaprasad Balakrishnan Please enable cookies. Sorry, you have been blocked You are...
Source: www.darkreading.com - Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are...