Source: www.bleepingcomputer.com - Author: Bill Toulas A 28-year-old United Kingdom man from Fleetwood, Hertfordshire, has been...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Bleeping Computer
Source: www.bleepingcomputer.com - Author: Mayank Parmar Microsoft has released the Windows 11 22H2 'Moment 3' update,...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan ESET malware researchers found a new remote access trojan (RAT)...
Source: www.bleepingcomputer.com - Author: Bill Toulas The Cuba ransomware gang has claimed responsibility for this month's...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Google has launched the Mobile Vulnerability Rewards Program (Mobile VRP),...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Microsoft is investigating service issues preventing users from accessing their...
Source: www.bleepingcomputer.com - Author: Bill Toulas The ALPHV ransomware group (aka BlackCat) was observed employing signed...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Highly realistic AI-generated images depicting an explosion near the Pentagon...
Source: www.bleepingcomputer.com - Author: Bill Toulas A cryptocurrency phishing and scam service called 'Inferno Drainer' has...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Today, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) ordered...
Source: www.bleepingcomputer.com - Author: Bill Toulas The Irish Data Protection Commission (DPC) has announced a $1.3...
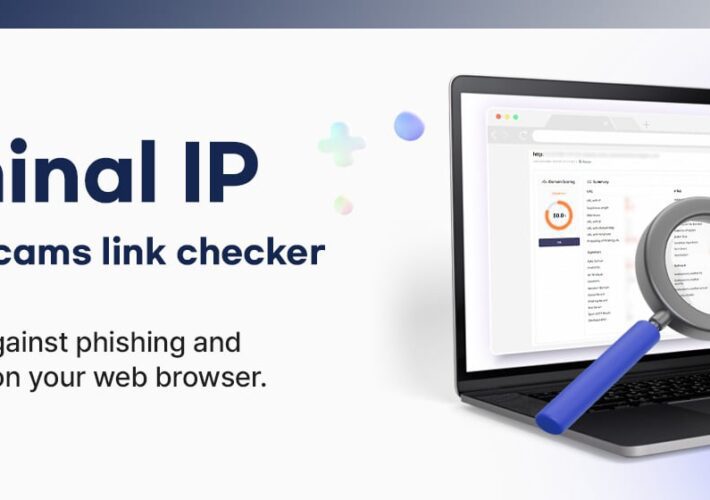
Source: www.bleepingcomputer.com - Author: Sponsored by Criminal IP The Anti-Phishing Council has reported an increase in...
Source: www.bleepingcomputer.com - Author: Mayank Parmar Microsoft is doubling its efforts to court the gaming community...
Source: www.bleepingcomputer.com - Author: Bill Toulas Google has updated its policy for personal accounts across its...
Source: www.bleepingcomputer.com - Author: Bill Toulas Researchers at Tencent Labs and Zhejiang University have presented a...
Source: www.bleepingcomputer.com - Author: Ax Sharma PyPI, the official third-party registry of open source Python packages...
Source: www.bleepingcomputer.com - Author: Bill Toulas A new malware distribution campaign is underway impersonating the CapCut...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan HP is working to address a bad firmware update that has...
Source: www.bleepingcomputer.com - Author: Ax Sharma Researchers have discovered multiple npm packages named after NodeJS libraries that...
Source: www.bleepingcomputer.com - Author: Lawrence Abrams In the ever-shifting ransomware landscape, we saw new ransomware gangs...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan CISA warned today of a security vulnerability affecting Samsung devices...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan A financially motivated cybercriminal group known as FIN7 resurfaced last...
Source: www.bleepingcomputer.com - Author: Bill Toulas ASUS has apologized to its customers for a server-side security...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Dish Network, an American television provider, most likely paid a...
Source: www.bleepingcomputer.com - Author: Bill Toulas Luxottica has confirmed one of its partners suffered a data...
Source: www.bleepingcomputer.com - Author: Bill Toulas A large cybercrime enterprise tracked as the "Lemon Group" has...
Source: www.bleepingcomputer.com - Author: Bill Toulas The popular KeePass password manager is vulnerable to extracting the...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Apple has addressed three new zero-day vulnerabilities exploited in attacks...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan Microsoft has decided to allow customers to choose when the...
Source: www.bleepingcomputer.com - Author: Sergiu Gatlan The Department of Justice revealed today that an 18-year-old man...