Source: www.techrepublic.com – Author: Karl Greenberg

Spearphishing is a sliver of all email exploits, but the extent to which it succeeds is revealed in a new study from cybersecurity firm Barracuda Network, which analyzed 50 billion emails across 3.5 million mailboxes in 2022, unearthing around 30 million spearphishing emails. These findings are in the company’s new report about Spear-Phishing Trends.
While that proportion represents less than a tenth of a percent of all emails, half of the organizations the firm examined in the study, which includes findings from a survey of more than 1,000 companies, were victimized by spearphishing last year. A quarter had at least one email account compromised through an account takeover (Figure A).
Figure A

Jump to:
- Identity theft and brand impersonation lead spearphishing exploits
- Damage to machines, data exfiltration top consequences
- The higher the mix of remote workers, the greater the vulnerability
- Companies slow to identify and respond to email attacks
- Slow pace of response keeps door open to cybertheft
- Automation and AI accelerate response times
- The spearphishing trend to continue in 2023
- AI models can flag unusual email communication patterns
Identity theft and brand impersonation lead spearphishing exploits
Barracuda Networks’ study isolated the five most prevalent spearphishing exploits.
- Scamming: 47% of spearphishing attacks tricked victims into disclosing information in order to defraud them and/or steal their identity.
- Brand impersonation: 42% of spearphishing attacks mimicked a brand familiar to the victim to harvest credentials.
- Business email compromise: 8% of spearphishing exploits impersonated an employee, partner, vendor or another trusted person to compel victims to make wire transfers or provide information from finance departments.
- Extortion: 3% of spearphishing emails used threats of the revelation of personal material.
- Conversation hijacking: 0.3% of attacks involved the hijacking of existing conversations.
The company also found that Gmail users were more likely to be spearphishing victims than users of Microsoft 365 (57% versus 41%, respectively).
Damage to machines, data exfiltration top consequences
The report detailed the results of a Barracuda-commissioned survey conducted by the independent researcher Vanson Bourne, who polled 1,350 organizations with 100 to 2,500 employees across a range of industries in the U.S., EMEA and APAC countries.
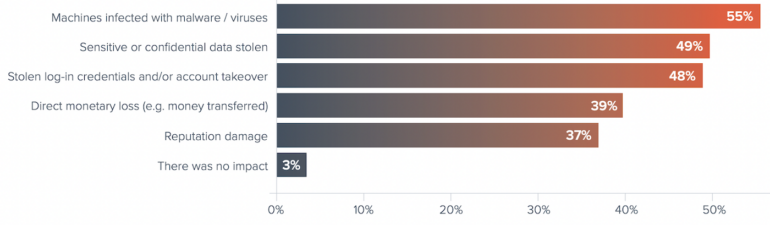
The survey queried companies about damages they experienced as a result of email attacks. Over half said machines were infected with malware, and roughly half reported theft of confidential information (Figure B).
Figure B
The higher the mix of remote workers, the greater the vulnerability
Remote work is increasing risks: Users at companies with more than a 50% remote workforce report higher levels of suspicious emails — 12 per day on average, compared to 9 per day for those with less than a 50% remote workforce. Companies favoring remote work also reported that it took longer to detect and respond to email security incidents — 55 hours to detect and 63 hours to respond and mitigate, compared to an average of 36 hours and 51 hours, respectively, for organizations with fewer remote workers.
On average, 10 suspicious emails were reported to IT on a typical workday, with users in India having reported the highest average number of suspicious daily emails — 15 per day, which is 50% above the global average. By contrast, the U.S. average was nine suspicious daily emails (Figure C).
Figure C
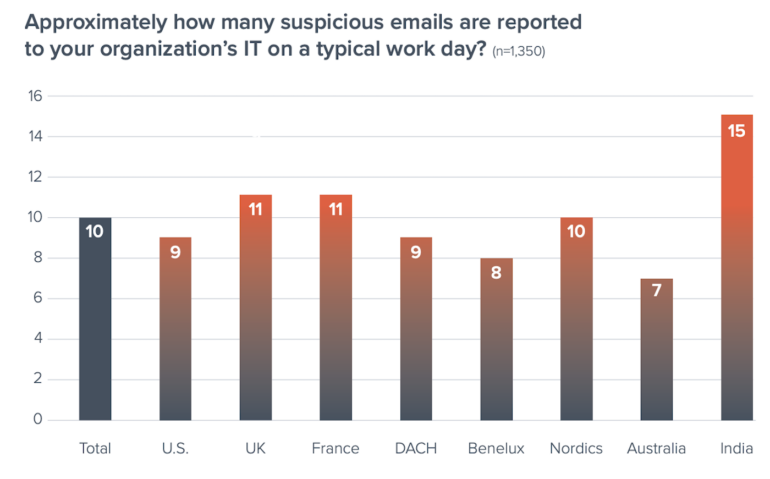
According to the report, the relatively high number of reported incidents in India may be evidence that organizations there are struggling to prevent email attacks or that organizations in India are placing higher focus on suspicious emails.
The average organization received approximately five emails per day that were identified as spearphishing exploits, and these attacks garnered an average 11% clickthrough rate, according to the report.
Companies slow to identify and respond to email attacks
From its survey of enterprises, Barracuda found that on average it takes nearly two days for organizations to detect an email security incident. On average, the enterprises polled by Barracuda took nearly 100 hours in total to identify, respond to and remediate an email exploit. They took 56 hours to respond and remediate after the attack was detected.
According to the report, from the respondents that experienced a spearphishing attack:
- 55% reported their machines were infected with malware or viruses.
- 49% reported having sensitive data stolen.
- 48% reported having stolen login credentials.
- 39% reported direct monetary loss.
Fleming Shi, the chief technology officer of Barracuda, said email is still very much the main attack vector used against enterprises, even small to medium-sized businesses, with threat actors who go after large companies often seeking prizes above and beyond what can be filched from a single hit.
Shi said, “They might be going after a person, a brand, data exfiltration or anything going beyond just the first ransom attack, getting to the point where they can hold an enterprise ransom for multiple years or multiple payouts,” he said. “At the end of the day, financially motivated attacks are still going to be numerous, but we also have to watch out for nation-state or politically-driven cyberattacks that try to influence or change opinion and maybe even impact the 2024 election. These are also possible because all they have to do is tweak the weapon to have a different impact.”
Slow pace of response keeps door open to cybertheft
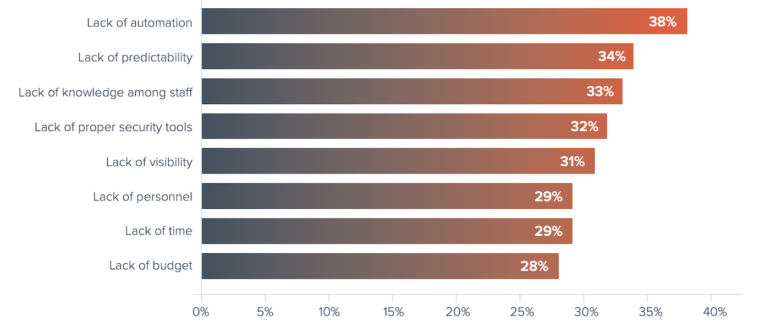
The survey found that for 20% of organizations, it takes longer than 24 hours to identify an email attack. According to the study, the long period means users have time to click on a malicious link or respond to an email. Thirty-eight percent of respondents reported taking more than 24 hours to respond to and remediate attacks. Obstacles cited include lack of automation, predictability and knowledge among staff hampering the discovery process. (Figure D).
Figure D
“Even though spearphishing is low volume, with its targeted and social engineering tactics, the technique leads to a disproportionate number of successful breaches, and the impact of just one successful attack can be devastating,” said Shi. “To help stay ahead of these highly effective attacks, businesses must invest in account takeover protection solutions with artificial intelligence capabilities. Such tools will have far greater efficacy than rule-based detection mechanisms. Improved efficacy in detection will help stop spearphishing with reduced response needed during an attack.”
Organizations victimized by spearphishing were more likely to say the costs associated with an email security breach increased in the last year: $1.1 million versus about $760,880 for those who were victims of other kinds of email attacks, according to the report.
Automation and AI accelerate response times
According to Barracuda Networks, 36% of organizations in the U.S. use automated incident response tools, and 45% use computer-based security awareness training. Both groups report faster response times on average, which means they are using fewer IT resources, and those resources can focus on other tasks.
Larger organizations cite lack of automation as the most likely obstacle preventing a rapid response to an incident — 41% for organizations with more than 250 employees, compared to 28% for organizations with 100–249 staff. The smaller companies cite additional reasons almost equally, including:
- Lack of predictability (29%)
- Knowledge among staff (32%)
- Proper security tools (32%)
The spearphishing trend to continue in 2023
Shi said it is likely that spearphishing, particularly related to conversation hijacking and business email compromise, will continue to prevail this year, with conversation hijacking building on past data breaches, basically where emails had been stolen.
“The example I will use is ProxyLogon, which was a vulnerability exchange by Microsoft where attackers took not only credentials but past email conversations that allowed them to reiterate and basically recreate a weapon based on previous interactions,” he said. “So, it makes it much easier to bypass all the guardrails, especially the human level awareness that we have.”
He also said that these attacks will be harder to block because not all of them are going to have links and attachments. “Sometimes it’s just an interaction to gain trust, and then it potentially leads to further access to the environment,” he said.
BECs drive spearphishing and vice versa
Shi sees the relationship between BECs and spearphishing as “intimate and symbiotic” because BECs can lead to additional phishing attacks, and phishing can lead to BECs.
“The main difference is that most BECs do not have links or attachments. It’s an interaction, a conversation that eventually leads to something bad happening. In order to get there, however, somebody has to compromise the environment. That weapon could be the initial spearphishing type of attack where credentials get stolen.”
Then, he added, with stolen credentials, actors can access the environment to identify communication patterns that continue the attack. “They somewhat camouflage themselves into the environment because once trust is built, an attacker can start activating new weapons that can be evasive to detection mechanisms.”
AI models can flag unusual email communication patterns
Barracuda Networks suggested machine learning is a useful tool for identifying anomalous emails through the establishment of normal communication patterns. And, that AI can be deployed to automatically recognize when accounts have been compromised.
The firm also suggests:
- Using technology to identify logins from unknown accounts.
- Monitoring emails for inbox rules that are malicious.
- Using multifactor authentication.
- Implementing DMARC authentication and reporting.
- Automating incident réponse.
- Training staff to recognize and report attacks.
Original Post URL: https://www.techrepublic.com/article/barracuda-networks-spearphishing-study/
Category & Tags: Artificial Intelligence,CXO,Security,Tech & Work,ai,cybersecurity,email security,incident response,phishing,remote work,spearphishing – Artificial Intelligence,CXO,Security,Tech & Work,ai,cybersecurity,email security,incident response,phishing,remote work,spearphishing
Views: 0




















































