Source: socprime.com – Author: Steven Edwards
How It Works
Uncoder AI reads a Sigma detection rule designed to identify DNS queries to malicious domains linked with the Katz Stealer malware family. It then automatically rewrites the logic into a fully compatible Microsoft Defender for Endpoint (MDE) Advanced Hunting query using the Kusto Query Language (KQL).
Left Panel – Sigma Rule:
- The rule is tagged with MITRE ATT&CK techniques like
T1071.004(Command and Control over DNS). - It detects DNS queries to domains such as
katz-panel.com,katzstealer.com, and related C2 infrastructure. - It uses the
dns_querycategory underwindowslogs.
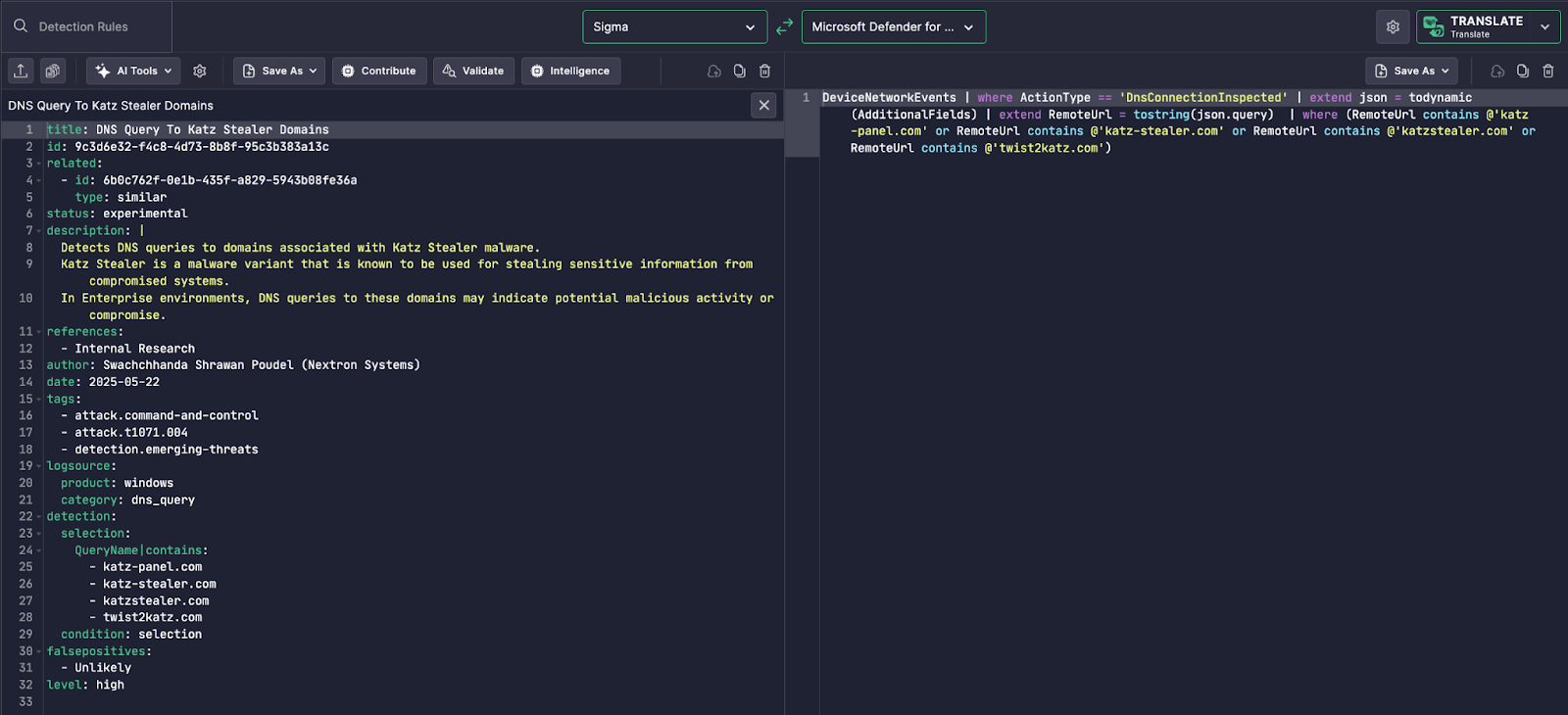
Right Panel – MDE Query:
Uncoder AI outputs a structured MDE query that:
- Filters DNS inspection events (
ActionType=="DnsConnectionInspected") - Dynamically extracts the domain name from
json.queryusingtodynamic()andtostring() - Matches domain names against the known IOC list using the contains operator
Example query excerpt:
DeviceNetworkEvents
|where ActionType=='DnsConnectionInspected'
|extend RemoteUrl=tostring(json.query)
|where RemoteUrl contains@"katz-panel.com" …
This query is ready to be used in Microsoft 365 Defender’s Advanced Hunting module for real-time or retroactive detection.
Why It’s Innovative
Translating detection rules across platforms is a major challenge, especially when adapting:
- Sigma’s abstracted field names to vendor-specific telemetry structures
- Query syntax for different environments (e.g., from YAML logic to KQL for MDE)
- Domain-based detection into structured JSON-aware logic
Uncoder AI automates this with precision by:
- Parsing Sigma’s selection logic
- Mapping detection fields to Microsoft Defender schema
- Maintaining intent, indicators, and logic across formats
Operational Value
With this feature, detection engineers can:
- Deploy Sigma rules directly into Microsoft Defender environments without writing KQL from scratch
- Detect threats like Katz Stealer across enterprise DNS telemetry
- Accelerate detection engineering cycles
- Ensure syntax validity and semantic correctness across translations
This capability dramatically improves the reuse and portability of threat detection content in modern SOC workflows.
Original Post URL: https://socprime.com/blog/sigma-to-mde-query-conversion-dns-detection-for-katz-stealer-via-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,MDE hunting,Microsoft Defender for Endpoint,Uncoder AI – Blog,SOC Prime Platform,MDE hunting,Microsoft Defender for Endpoint,Uncoder AI
Views: 1




















































