Source: www.csoonline.com – Author:
Microsoft’s latest rollouts to Windows 11 24H2 and Windows Server 2025 include the arrival of Recall and hotpatching. Here are the security settings and recommendations to note.
Windows 11 24H2 and Server 2025 are rolling out new features and enhancements — some of which are aimed to better help you harden your network, while others will need to be reviewed to ensure they don’t undercut your network’s security.
Here’s what CISOs should know about the latest Windows 11 and Server 2025 updates.
Recall brings its privacy and security concerns to Windows 11
Nearly a year after announcing Recall, Microsoft will start to roll out the feature in its May update to qualifying hardware running 24H2. Received on announcement as a ‘privacy nightmare,’ Recall has since been made an opt-in feature after early waves of privacy and security backlash.
Recall allows users to take snapshots of actions they take on their machines. To use Recall, users’ machine require a turbocharged neural processing unit (NPU) capable of performing more than 40 trillion operations per second (TOPS). Windows 11 machines shipping with the feature are branded as Copilot+ computers and have Windows 11 Home software shipped on the machines. However, Recall is also supported on systems running Windows 11 Professional and Enterprise. And while the feature can be enabled on qualifying machines, it will not be enabled by default on domain machines.
Recall’s main draw is that its snapshots, which are processed locally using AI and optical character recognition (OCR), create a searchable archive of the user’s activity, including actions taken in apps and documents, as well as on websites.
Susan Bradley / CSO
Security teams should consider setting policies to block Recall’s installation in cases where its use doesn’t meet your privacy and security policies. In addition, you should consider the impact that consultants and independent or temporary employees may have when accessing your resources.
The feature is not without its criticisms. Early versions of Recall were not encrypted. Moreover, snapshots could be accessed by other users on the system and were merely protected with NTLM permissions.
Guidance is provided by Microsoft on how to best manage the service. As the company notes, “By default, Recall is removed on commercially managed devices. If you want to allow Recall to be available for users in your organization and allow them to choose to save snapshots, you need to configure both the Allow Recall to be enabled and Turn off saving snapshots for Recall policies.”
Windows hotpatching could shake up update policies
Microsoft is also rolling out a new feature that enables security teams to push out OS updates without requiring as many reboots of Windows 11 or Server 2025 systems.
The feature, called Windows hotpatching, requires companies to run Windows 11 Enterprise 24H2 (Build 26100.2033 or later). You’ll also need to be managing the systems with Intune and be licensed under Windows Enterprise E3/E5 or Windows 365 Enterprise.
Note that not every update will be available as a hotpatch. Microsoft has published a calendar of updates, noting hotpatches that do not require a reboot and “baseline” updates that require a reboot. For example, the April update (KB5055523) is considered a baseline update that requires a reboot, whereas the May update (KB5058497) is a hotpatch and thus will not require a restart. Once you have installed the baseline, you’ll then need to enable the Hotpatching policy in Intune.
Security teams interested in hotpatching need to review your security policies and baselines before rolling out workstations and servers with this new feature. If your systems need monthly reboots due to established organizational policies, or other software in your organization mandates a monthly reboot, you may need to update and evaluate your policies.
Additional Windows 24H2 security actions: Entra ID, Recall, Copilot
In addition to evaluating patching policies, security teams should take the time to evaluate your security baselines for Windows 24H2 as well as Server 2025. Both Microsoft and the Center for Internet Security have guidance and documentation to roll out secured versions of these platforms.
One consideration is to set “Block all consumer Microsoft account user authentication” to “Enabled” (Automated). This will ensure that users can only use Entra ID based logins and will not be offered login options using a Microsoft account on their systems.
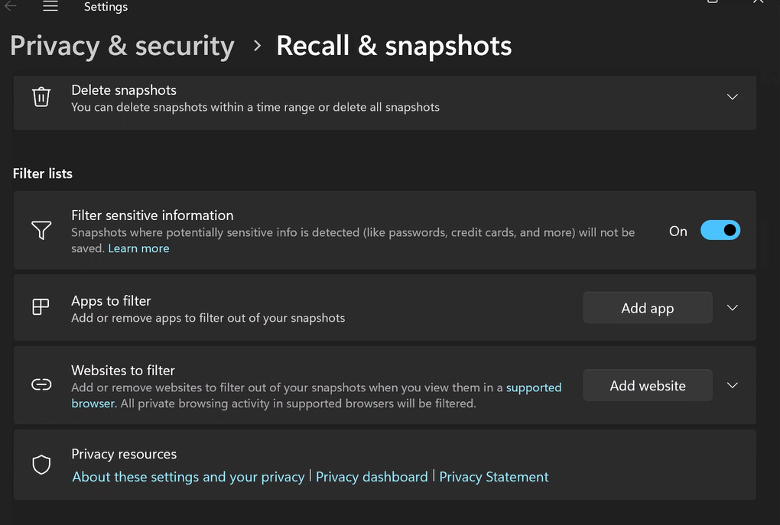
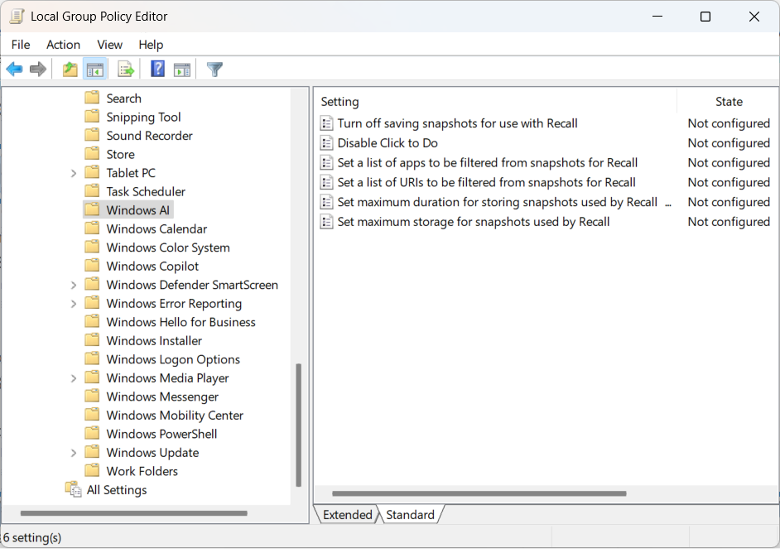
Microsoft also includes settings to control Copilot, Recall, and other technologies. Security teams should review these options. For example, you can proactively control Recall by setting the following values under User Configuration > Administrative Templates > Windows Components >Windows AI:
Susan Bradley / CSO
You can prevent Recall use by turning off the saving of snapshots and also disabling Click to Do. Alternatively, if you want to enable the service, I recommend setting a list of applications that you want filtered as well as excluding a list of URLs.
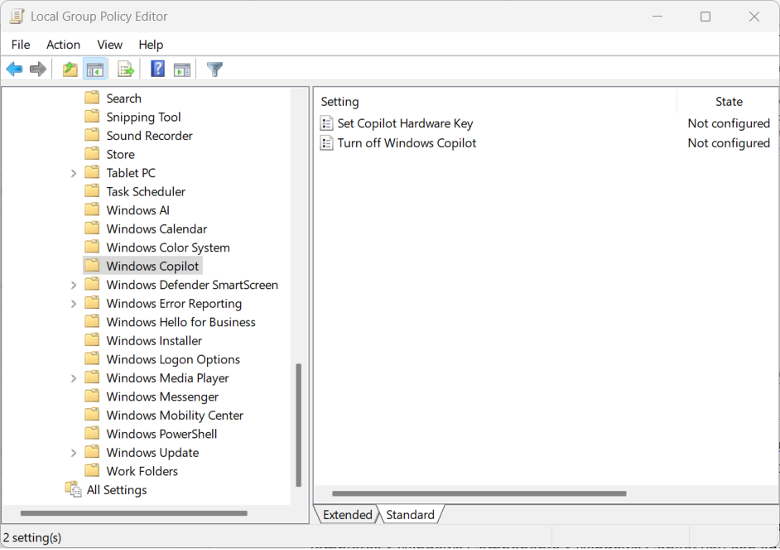
In addition, you can set policies for Copilot. Under User Configuration > Administrative Templates > Windows Components > Windows Copilot, you can enable or disable the use of Copilot proactively:
Susan Bradley / CSO
Windows Server 2025: Recommendations and enhancements
For Server 2025, it is now recommended to have additional security settings to protect accounts and logons. For example, security teams should set an account lockout threshold of three attempts. Previously, the recommendation for this setting was 10 attempts before locking an account.
Microsoft has also added a policy for smart card crypto agility located at SystemKDC and SystemKerberos, allowing users to configure the hash algorithm used in smart card deployments.
Server 2025 has also enhanced the policies for controlling Local Administrator Password Solution. These policies include:
- Size of Encrypted Password History allows administrators to define the number of previous encrypted passwords stored in Active Directory. By managing password history effectively, we enhance security by preventing reuse of old passwords.
- Post-authentication Actions specifies the actions that should be taken after an authentication by the managed account. Administrators can choose to reset the password, log off the managed account, reboot the device, or terminate processes. A grace period can also be configured before these actions are executed, ensuring robust security measures are in place.
- Configure Automatic Account Management configures options for automatic account management, allowing administrators to specify the target account, whether it be the built-in admin account or a custom account. Administrators can define the name or prefix for the managed account and decide whether the managed account should be enabled or disabled. Additionally, there is an option to add a random numeric suffix to the managed account name, enhancing security through complexity and uniqueness.
NTLM in the crosshairs
Microsoft is making a strong push to disable NTLM (Windows New Technology LAN Manager), long viewed as a security sinkhole, and has two new security policies specifically to harden or prevent use of NTLM:
- Block NTLM provides administrators an option to configure SMB to block NTLM. When enabled, the SMB client will not use NTLM for remote connection authentication, thereby reducing the risk of NTLM-based attack. It’s not enabled by default.
- Block NTLM Server Exception List allows administrators to specify servers that can still use NTLM for remote connection authentication, even if the Block NTLM policy is enabled. This setting is useful for maintaining compatibility with legacy systems that require NTLM while still enforcing stricter security measures for other connections.
Of all the new security settings in Server 2025, security teams must review your use of NTLM. Begin the process now to phase it out.
As you begin to evaluate Windows 11 24H2 and Server 2025, you should also evaluate how you authenticate into your network. Take the time to review whether you are still using or needing older authentication processes such as NTLM that should be phased out. Take the time to review if you can phase out these legacy settings.
SUBSCRIBE TO OUR NEWSLETTER
From our editors straight to your inbox
Get started by entering your email address below.
Original Post url: https://www.csoonline.com/article/3996290/securing-windows-11-and-server-2025-what-cisos-should-know-about-the-latest-updates.html
Category & Tags: Windows Security – Windows Security
Views: 7



















































