Source: www.securityweek.com – Author: Ionut Arghire
A Russia-linked threat actor tracked as Storm-2372 has been targeting government and private organizations in a global campaign employing device code phishing for account compromise, Microsoft reports.
The campaign has been ongoing since at least August 2024, targeting entities in the government, IT, defense, telecoms, health, education, and energy sectors, as well as NGOs in Africa, Europe, the Middle East, and North America.
Relying on a numeric or alphanumeric code, the device code authentication flow is used to authenticate an account from a device that cannot perform an interactive authentication.
As part of a device code phishing attack, the threat actor asks the targeted service to generate a device code and convinces the victim to enter that code on a legitimate sign-in page. The targeted service then generates an access token that the attacker can recover and abuse to access the target’s accounts and data.
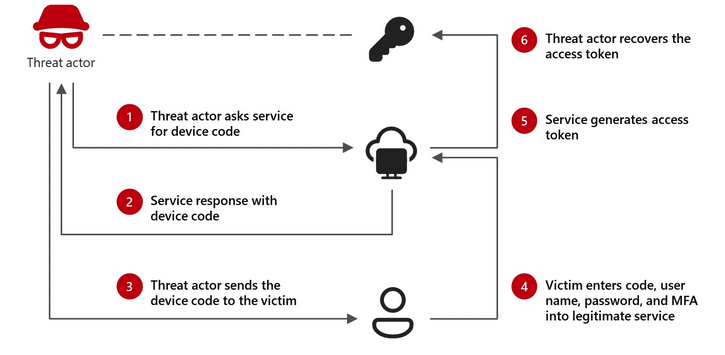
The threat actor can use the tokens to access email and cloud storage services that the victim has permissions to, without a password, and to move laterally.
“This technique could enable persistent access as long as the tokens remain valid, making this attack technique attractive to threat actors,” Microsoft notes.
As part of the observed attacks, Storm-2372, described by Microsoft as a Russian state-sponsored threat actor, crafted phishing emails containing fake Microsoft Teams meeting invitations designed to steal the victims’ authenticated sessions by convincing them to complete device code authentication requests.
“Storm-2372 likely targeted potential victims using third-party messaging services including WhatsApp, Signal, and Microsoft Teams, falsely posing as a prominent person relevant to the target to develop rapport before sending subsequent invitations to online events or meetings via phishing emails,” Microsoft notes.
After successfully obtaining an authentication token, the threat actor would access the victim’s account and abuse it to send additional device code phishing messages to other users within the organization, Microsoft says.
Advertisement. Scroll to continue reading.
Storm-2372 was also seen using Microsoft Graph to search the victims’ inboxes for messages “containing words such as username, password, admin, teamviewer, anydesk, credentials, secret, ministry, and gov”, and to exfiltrate any email found in these searches.
Starting February 13, the threat actor switched to using the specific client ID for Microsoft Authentication Broker in the device code authentication flow, enabling them to receive a refresh token they could use to obtain another token to register their own devices with Entra ID.
“With the same refresh token and the new device identity, Storm-2372 is able to obtain a Primary Refresh Token (PRT) and access an organization’s resources. We have observed Storm-2372 using the connected device to collect emails. The actor has also been observed to use proxies that are regionally appropriate for the targets, likely in an attempt to further conceal the suspicious sign in activity,” Microsoft notes.
According to cybersecurity firm Volexity, the device code phishing technique has been used in attacks targeting the US State Department, Ukrainian Ministry of Defence, European Union Parliament, and various research institutions since January 2025.
Volexity identified three other Russia-linked threat actors employing the technique, namely CozyLarch (also tracked as APT29, Cozy Bear, and Midnight Blizzard), UTA0304, and UTA0307, but says that it is possible that a single threat actor is responsible for the attacks.
Related: Russian Cyberspies Caught Spear-Phishing with QR Codes, WhatsApp Groups
Related: PayPal Phishing Campaign Employs Genuine Links to Take Over Accounts
Related: Organizations Warned of Rise in Okta Support Phishing Attacks
Related: Businesses Worldwide Targeted in Large-Scale ChatGPT Phishing Campaign
Original Post URL: https://www.securityweek.com/russian-state-hackers-target-organizations-with-device-code-phishing/
Category & Tags: Nation-State,device code phishing,Microsoft,phishing,Russia,Storm-2372 – Nation-State,device code phishing,Microsoft,phishing,Russia,Storm-2372
Views: 6




















































