Russia-linked Gamaredon APT group targets Ukrainian entities with PowerShell info-stealer malware dubbed GammaLoad.
Russia-linked Gamaredon APT group (aka Shuckworm, Actinium, Armageddon, Primitive Bear, and Trident Ursa) targets Ukrainian entities with PowerShell info-stealer malware dubbed GammaLoad, Symantec warns.
The Computer Emergency Response Team of Ukraine (CERT-UA) confirmed the ongoing cyber espionage campaign.
Symantec and TrendMicro first discovered the Gamaredon group in 2015, but evidence of its activities has been dated back to 2013. The group targeted government and military organizations in Ukraine.
The recent wave of attacks began on July 15 and was ongoing as recently as August 8, 2022.
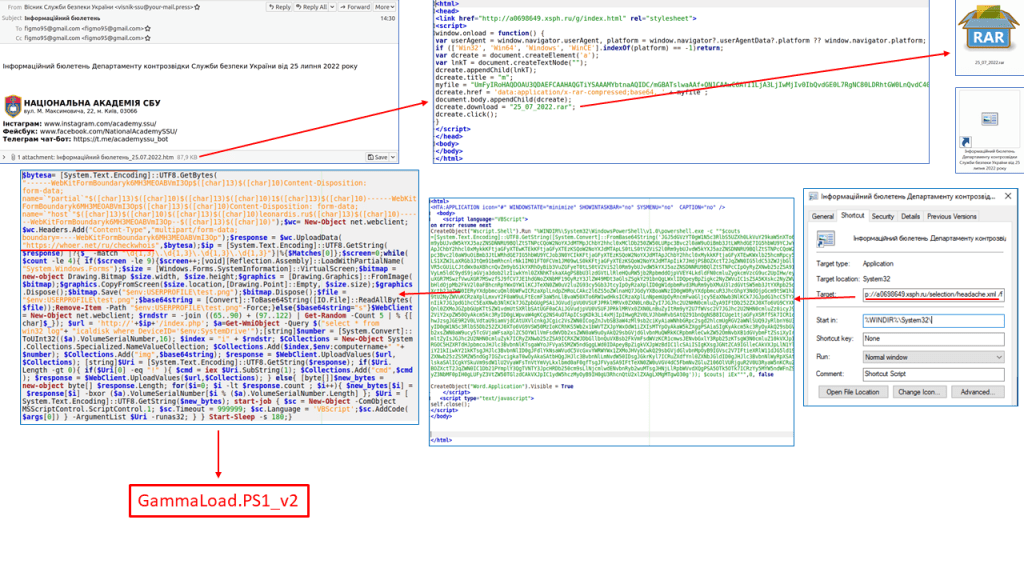
The attack chain starts with spear-phishing messages using a self-extracting 7-Zip file, which was downloaded via the system’s default browser. Then the mshta.exe downloaded an XML file, which was likely masquerading as an HTML application (HTA) file.
“The downloading of the XML file onto victim networks was followed by the execution of a PowerShell stealer. We saw three versions of the same PowerShell stealer appear on the one system.” reads the analysis published by Symantec. “It’s possible the attackers may have deployed multiple versions of the stealer, which were all very similar, as an attempt to evade detection.”
The files were hosted on a subdomain known to be associated with Shuckworm activity since May 2022. The final payload deployed by the attackers is a PowerShell stealer malware dubbed GammaLoad.PS1_v2.
In some cases, attackers also delivered two backdoors named Giddome and Pterodo, which are known to be part of the Gamaredon arsenal.
Pterodo is a multistage Visual Basic Script (VBS) backdoor designed to collect sensitive information or maintain access to compromised machines. It is distributed in a spear-phishing campaign with a weaponized office document that appears to be designed to lure military personnel.
The Giddome backdoor supports multiple capabilities, including recording audio, taking screenshots, logging keystrokes, and downloading and executing arbitrary executables onto the infected hosts.
Threat actors also used the legitimate remote desktop protocol (RDP) tools Ammyy Admin and AnyDesk for remote access
“As the Russian invasion of Ukraine approaches the six-month mark, Shuckworm’s long-time focus on the country appears to be continuing unabated. That this recent activity continues even after CERT-UA documented it shows that fear of exposure does not deter the group from its activities.” concludes the report. “While Shuckworm is not necessarily the most tactically sophisticated espionage group, it compensates for this in its focus and persistence in relentlessly targeting Ukrainian organizations.”
Symantec also shared Indicators of Compromise (IoCs) for this campaign.
Follow me on Twitter: @securityaffairs and Facebook
(SecurityAffairs – hacking, Gamaredon)
The post Russia-linked Gamaredon APT continues to target Ukraine appeared first on Security Affairs.
Leer másSecurity Affairs
Views: 0