Source: www.infosecurity-magazine.com – Author:
Keir Giles, a British expert on Russian information operations, has been targeted by a sophisticated spear phishing attack using novel social engineering techniques.
The writer and senior consulting fellow at the UK think tank Chatham House was lured into sending app-specific passwords to someone impersonating a US State Department employee.
The Google Threat Intelligence Group (GTIG) investigated the case in collaboration with the Citizen Lab.
The tech giant attributed the campaign to a threat actor tracked as UNC6293 and assessed “with low confidence” that cluster is associated with APT29, a cyber espionage group linked to Russia’s Foreign Intelligence Service (SVR).
Email From a Fake US State Department Official
On May 22, 2025, Giles received an email from someone posing as ‘Claudie S. Weber’ who purported to be a senior program advisor at the US Department of State (DoS).
In the email, ‘Claudie S. Weber’ invited Giles for a meeting to discuss “certain recent developments” with the sender and their colleagues.
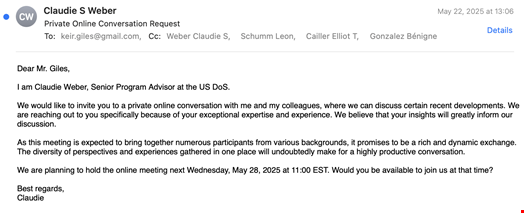
Such an invitation is “something that would be common for him to receive,” said the Citizen Lab in its report, published on June 18.
However, the researchers stated that they were unable to find any ‘Claudie S. Weber’ in the US State Department registries or elsewhere.
While the attacker used a Gmail account for the entire interaction (claudie.s.weber[at]gmail.com), they cc’d four other email addresses ending with @state.gov, including ‘WeberCS[at]state.gov,’ as a way of making the email exchange look more credible.
“We believe that the attacker is aware that the State Department’s email server is apparently configured to accept all messages and does not emit a ‘bounce’ response even when the address does not exist,” said the Citizen Lab researchers.
They also assessed that the generic tone and evasiveness of the email sender could suggest that the attacker used a large language model (LLM) to craft the message.
Leveraging App-Specific Passwords
Although the initial email did not contain any malicious content, a subsequent email included a PDF file with instructions to register for an “MS DoS Guest Tenant” account.

To create such an account, Giles was told he would need to create an app-specific password (ASP) on a Google email account, which would provide him access to a secure government resource enabling him to participate in the consultation.
“In reality, of course, the ASP would provide them complete and persistent access to his accounts,” said the Citizen Lab researchers.
An ASP is a password created by a user to allow certain applications that are incompatible with multifactor authentication (MFA) or a platform’s standard login workflow to access their online accounts that have MFA enabled.
Google refers to these apps as Less Secure Apps (LSAs) and has been phasing out support in Google Workspaces. However, Google users can still create and remove these passwords on their personal Gmail accounts.
A Sophisticated Spear Phishing Campaign
Slightly suspicious, Giles followed the procedure, but with a different account from the one the attacker had intended for him to use.
On June 14, after over 10 email exchanges, Giles publicly shared his suspicion that the material exfiltrated from his accounts is likely to be manipulated and selectively released as part of a future information operation.
In a social media thread, he explained that one factor that increased the supposed legitimacy of the request is what he described as its “unhurried pacing.”
“The attackers were also ready with answers and prepared to adapt in response to Mr. Giles’ replies. For example, after Mr. Giles stated that the initially proposed time would not work, the attackers chose to not explicitly add pressure or urgency, instead suggesting that they set up the platform for the future,” the Citizen Lab researchers explained.
Google’s Mitigation Recommendations
Google later identified the attack, locked down the impacted accounts and disabled the attacker’s email.
In a separate report published on June 18, GTIG stated it had identified another similar campaign that started in April 2025 and involved a Ukrainian and Microsoft-themed ASP name.
The GTIG report provided a list of mitigation recommendations, including:
- Not using ASPs for accounts that are part of the Advanced Protection Program (APP), as this program is designed for high-risk individuals and does not allow ASP creation
- Revoking ASPs when no longer needed
- Regularly monitoring account activity and notifications, such as those sent by Google when an ASP is created.
- Implementing enhanced security measures, like those provided by the Advanced Protection Program, for individuals at high risk of targeted attacks
Original Post URL: https://www.infosecurity-magazine.com/news/russia-expert-elite-hackers-us/
Category & Tags: –
Views: 4



















































