Source: securityboulevard.com – Author: Tally Shea
Reading Time: 7 minutes
Let’s establish the problem: practitioners are experiencing alert fatigue – desensitized, overwhelmed, and unable to manage the sheer scale of cloud security alerts. Why? The vast nature of the cloud means more potential for security risks, on average the typical large enterprise hosts six different security tools (each firing off their own alerts), and about half of daily alerts are reported to be false positives. When every alert begins to look the same – with the same level of urgency – it becomes impossible to tackle them all.
At the leadership level, this deluge of alerts concerns you too. Tackling security alerts, be it vulnerabilities or other risks, means hiring more people or working your current team harder and longer (both translate into major costs.) It becomes inevitable that your risk reduction efforts are inefficient as practitioners waste time and energy chasing dead end vulnerabilities that aren’t actually business critical, or miss the ones that actually can hurt you.
It’s nothing new to approach this problem with the recently adopted ‘risk in context’ approach. Meaning, gaining the insights needed to better understand how an alert or vulnerability actually ties back to sensitive assets, overprivileged identities, and ultimately business disruption. But, a lot of these tools claiming to offer this risk in context really only consider one thing when rating an alert’s sensitivity: the nature of the incident or violation itself – for example logging not enabled on a datastore vs an overprivileged API accessing an S3 bucket it never has before.
There is a better solution out there, and it’s Sonrai Security’s Prioritized Actions.
What is Different about Sonrai’s Prioritized Actions?
It is no longer sufficient to try and tackle everything, so it’s time to focus efforts where they’ll have the greatest impact (keeping your business running, customers happy, and avoiding compliance fines.) Sonrai’s Prioritized Actions not only prioritize alerts at the most granular level so you can address high risk scenarios, but also identify the highest value fixes across broad cloud estates. That means finding the alerts that if remediated, translate into the greatest risk reduction for your business.
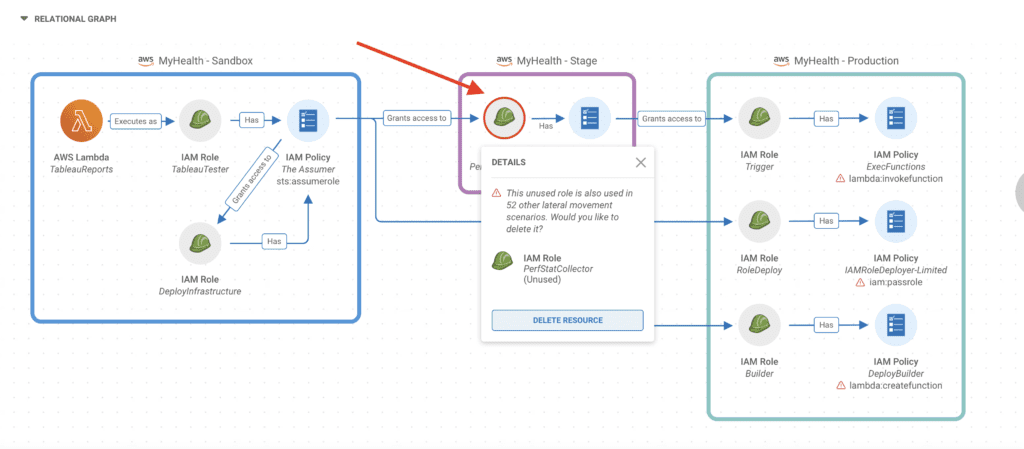
Sonrai’s technology helps you reveal those root causes or ‘problem children’ that are systemically causing risk in your cloud. Consider the attack path graph below.
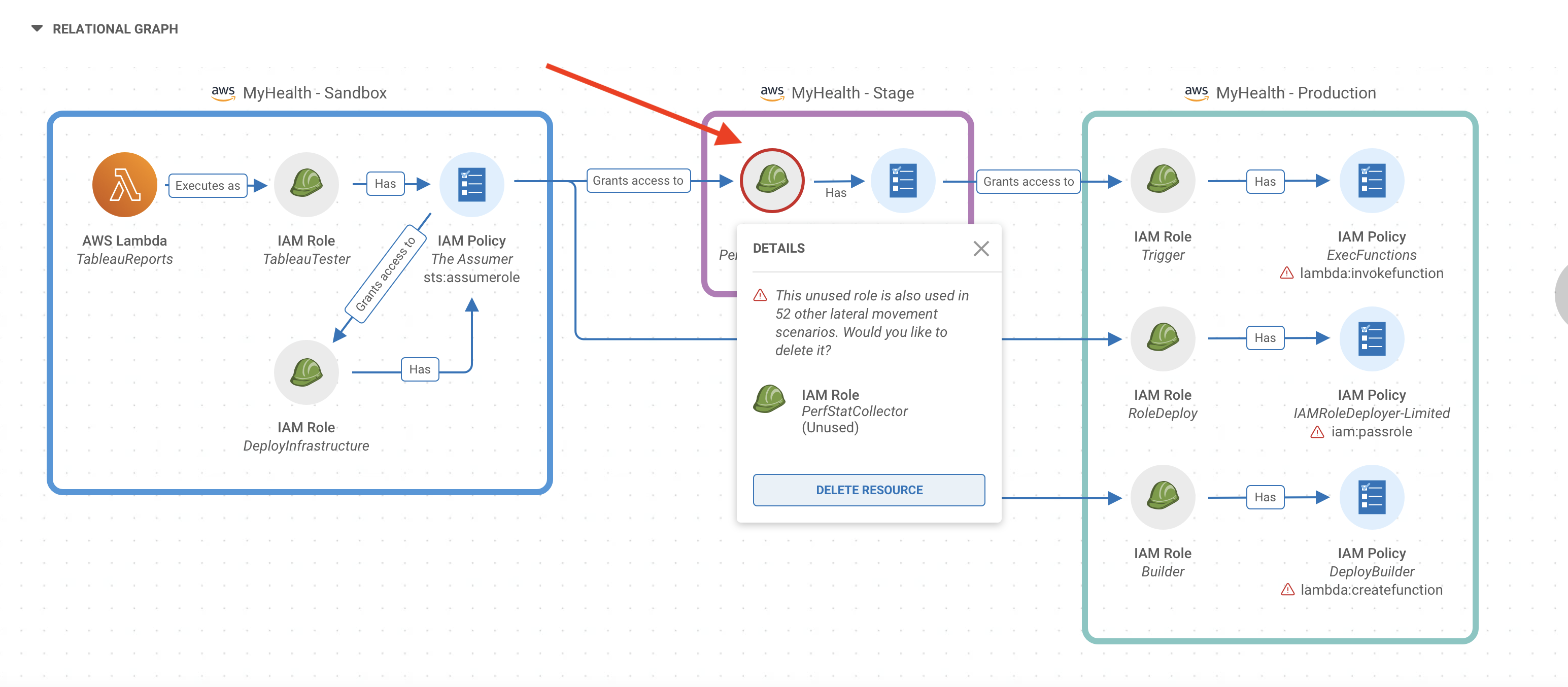
Notice the helmet circled in red, this is an IAM Role that Sonrai has detected in 52 other lateral movement scenarios. In this case, deleting this one resource (or configuring it differently) will reduce risk in 53 very similar scenarios – talk about efficiency. This suggestion highlights the final differentiator in Sonrai’s Prioritized Actions, the actionable suggestions to fix cloud problems. These remediation suggestions include a wide range of cloud security concerns spanning across identity, data, platform, and workloads, and offer enough detail that teams feel enabled to fix the problem.
How Does Sonrai Security Measure Risk?
To help your team’s determine what the most pressing matters are, Sonrai designates a risk score for each alert, ranging from low to critical. This score isn’t just considering the nature of the alert itself, (e.g. an open port to the internet, an identity with privilege escalation risks, etc.) but includes the sensitivity of the environment where the incident originates from, and if the incident has any ties back to sensitive data or applications.
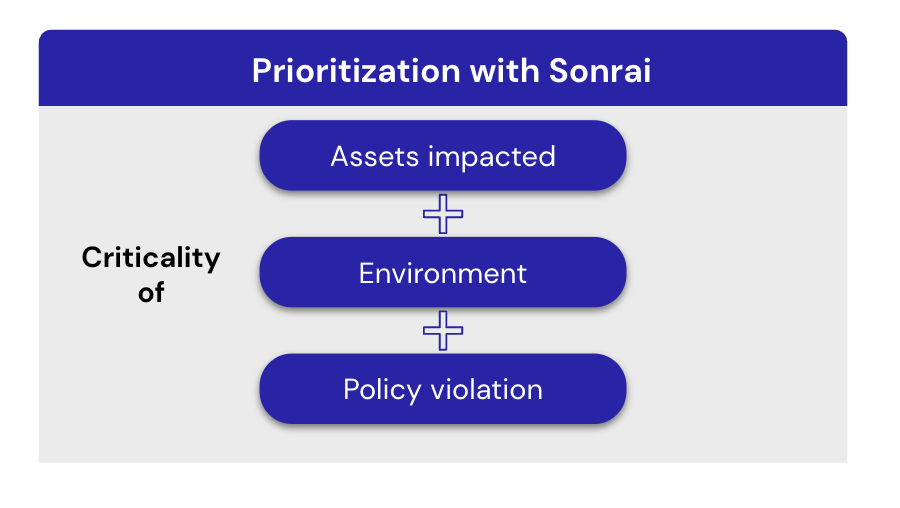
This insight is fueled by Sonrai’s patented identity access analytics that reveal every access point to data and potential attack path, and Sonrai’s customizable workflow where your business classifies the sensitivity of different environments. Speaking of workflow – Sonrai’s Prioritized Actions isn’t just intelligence, but fittingly, actionable recommendations.
We offer Console instructions or CLI code and bot remediation. This information is routed in an intelligent workflow that’s customized to your teams and projects because at the enterprise level, remediation is often distributed across teams. This ensures the right people get alerted when the data, project, or environment they’re responsible for is at risk, so that the people who know best are the ones fixing it. With escalation paths and workflow all routed properly, you have a chance at distributed security, or supporting a shift left initiative.
Seeing Prioritized Actions, In Action.
Here are two examples of vulnerabilities detected on cloud workloads. Both have CVSS scores of 9.8. Other tools that base prioritization off of CVSS scores or a policy violation alone would leave your teams to remediate these at your own discretion. While two remediations may not seem like much work, imagine hundreds of these. What’s important to note is while these both have a 9.8 rating, Sonrai calculates two very different risk scores – critical and low. Let’s see why.
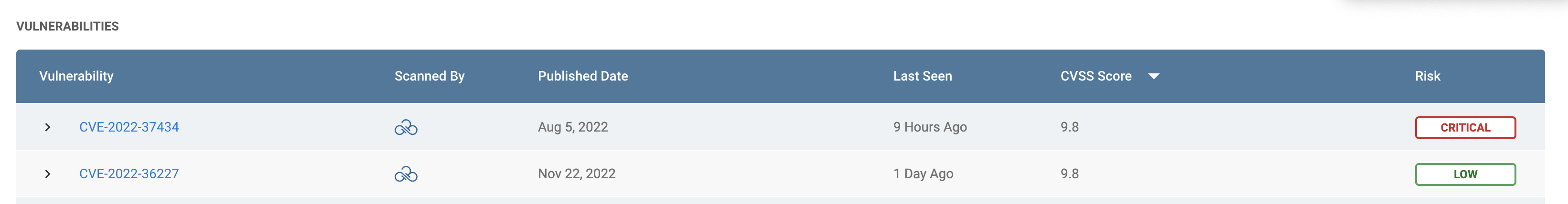
Clicking into CVE-2022-37434, rated critical, we can see many virtual machines distributed across various environments. We’ll hone in on the production environment & sensitive data.
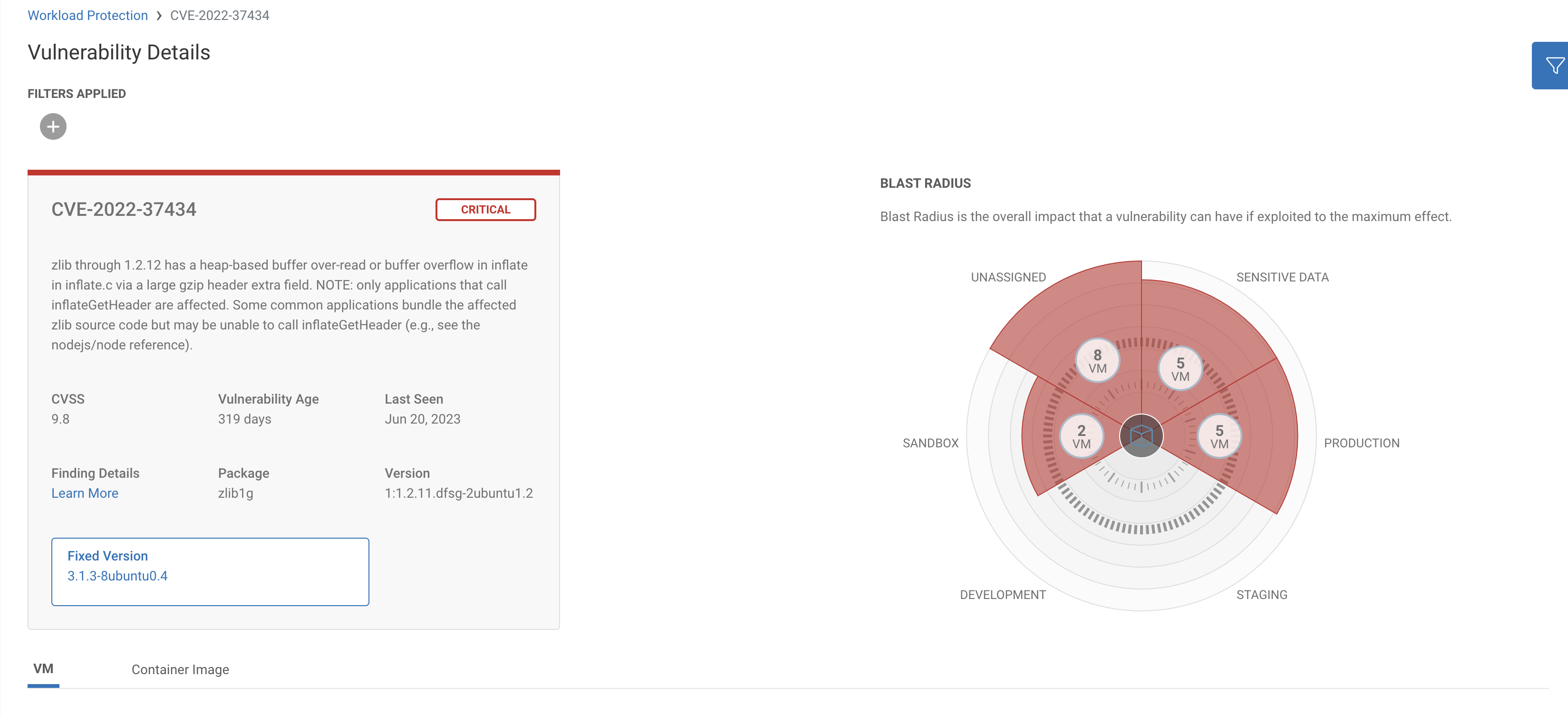
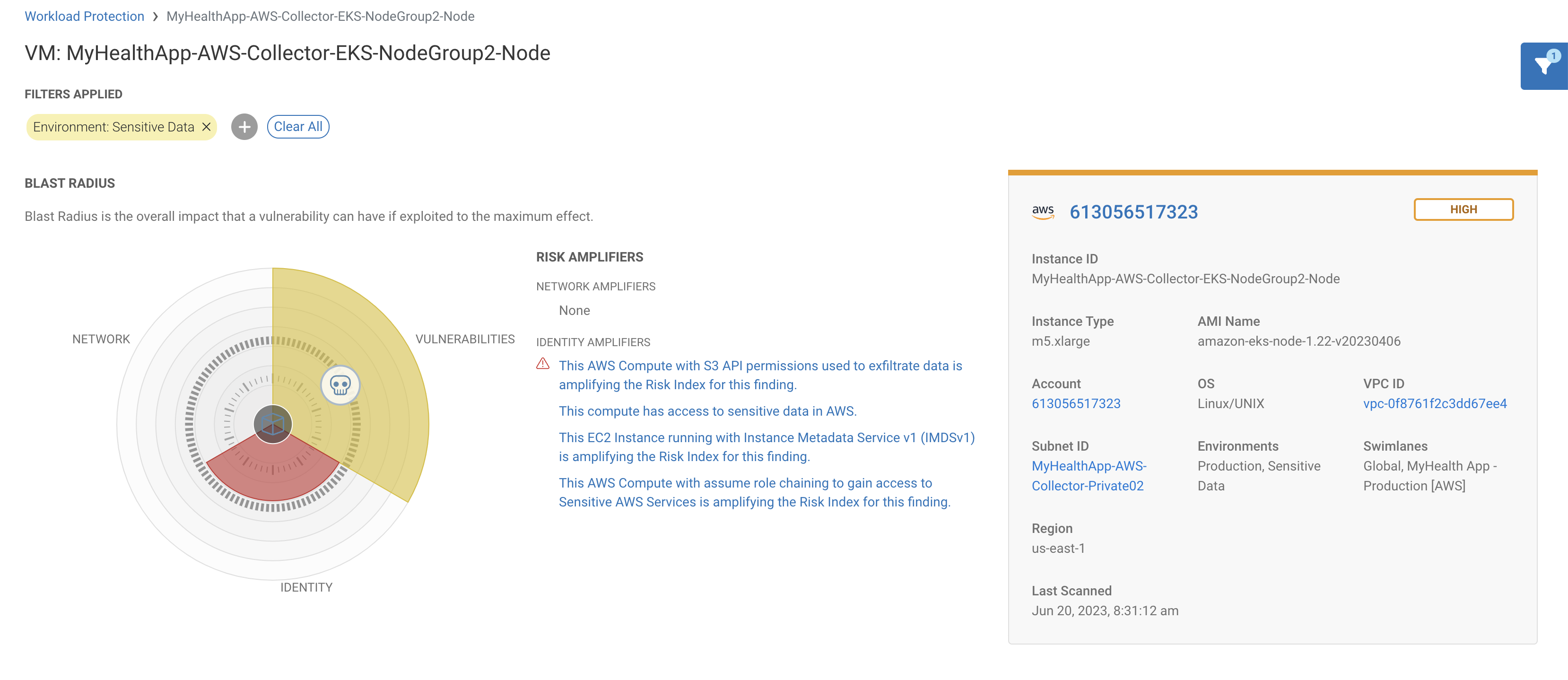
In Prod we can see one of the virtual machines, MyHealthApp-AWS-Collector-EKS-NodeGroup2 has an alert for an identity ‘Risk Amplifier’ – AWS Compute with S3 API permissions used to exfiltrate data.
Taking an even closer look, the platform offers the chance to actually see the permission path allowing this compute the chance to exploit API permissions and end up with exfiltration rights from an S3 bucket.
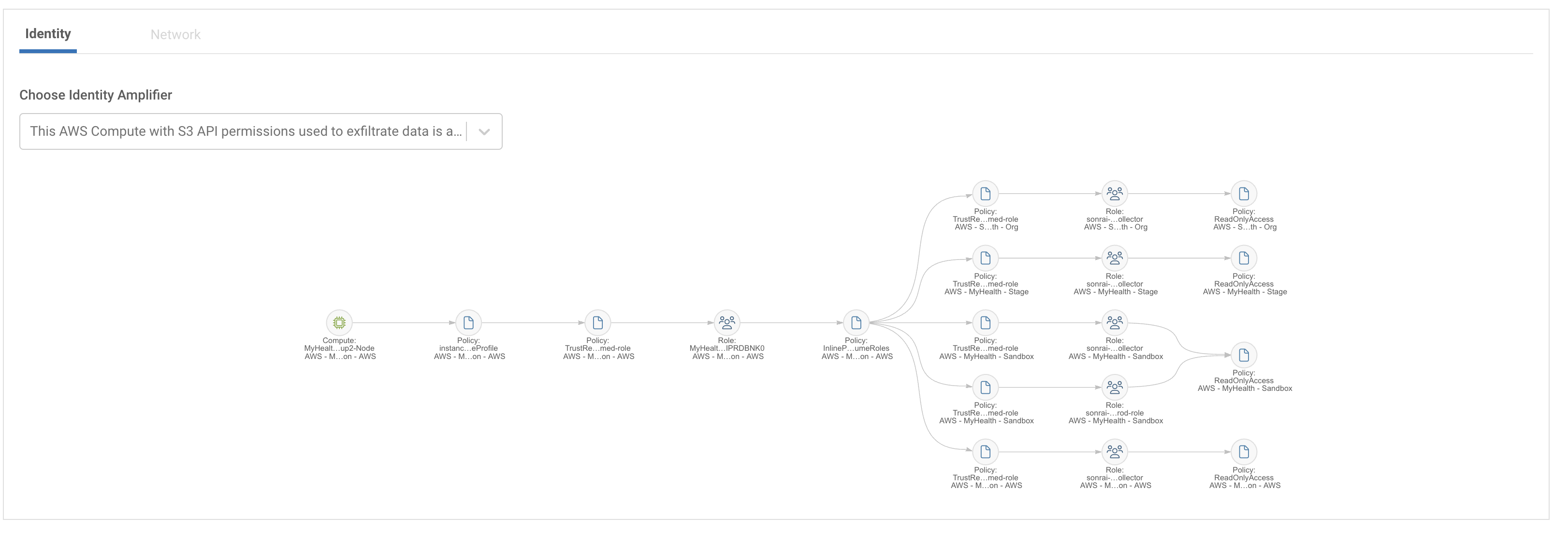
This is a great example of Sonrai considering all three evaluations of risk (a policy violation/CVSS score, an environment sensitivity, and a tie back to sensitive data) to designate a truly ‘critical’ alert and help your teams sort through top priorities.
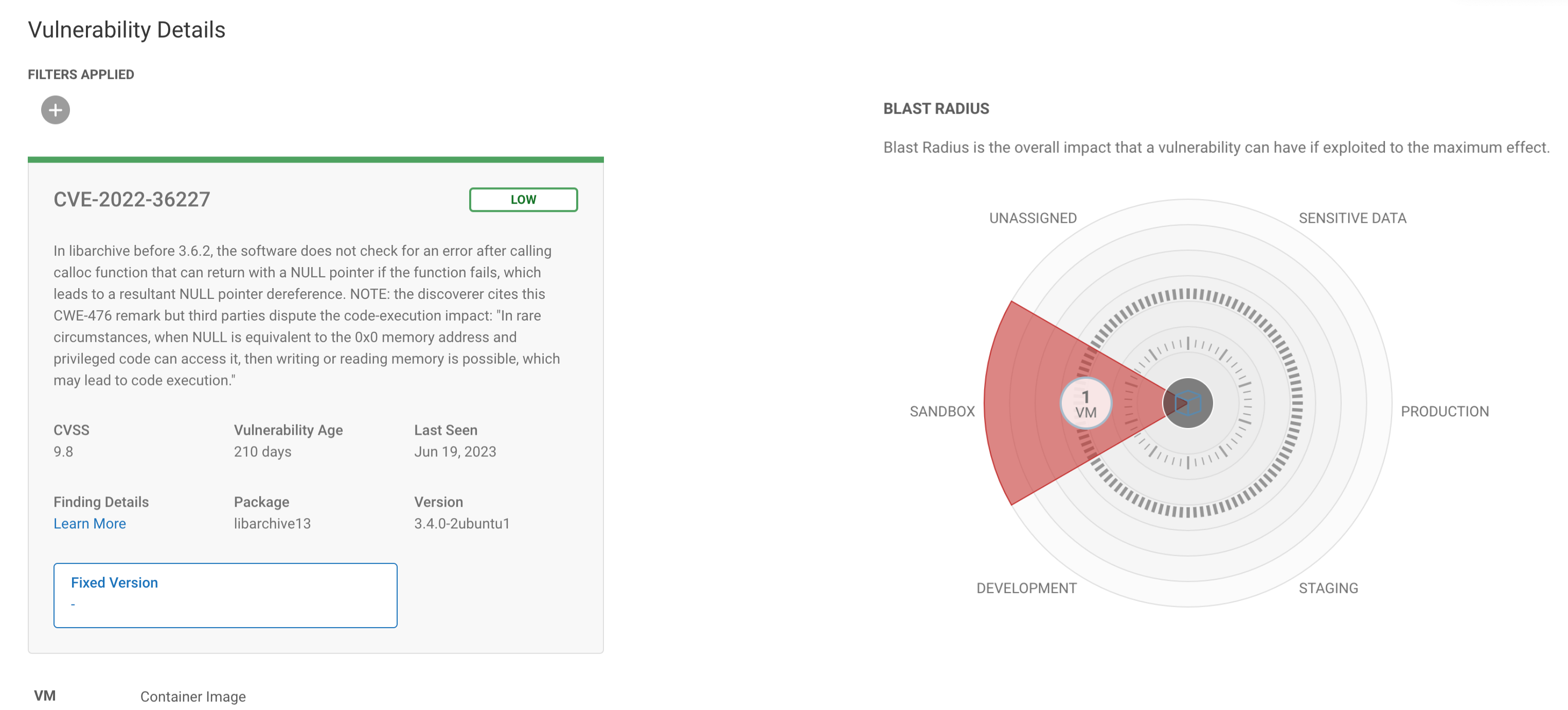
On the other hand, de-prioritization is just as useful as prioritization when it’s your teams’ limited time, energy, and resources being used to secure your entire cloud infrastructure. Looking back to CVE-2022-36227, it has a CVSS score of 9.8, but Sonrai calculates a risk score of ‘Low.’

If the CVSS score were the only information your team had, it would prioritize remediating this alert before other more pressing concerns – this is a waste of time and resources. Sonrai however, considered that this vulnerability not only was in a sandbox account (it’s safe to assume the environment is at a lower security level), but also that the virtual machine is a dead end with zero access to business critical assets. The result is a calculated low score, and a team that knows remediating this alert can wait till another day.
For this last example, let’s consider a story where other solutions may rank something a low priority, but Sonrai’s risk evaluation says otherwise. As you can see, CVE-2022-24448 is given a CVSS score of just 3.3, yet Sonrai rates it a critical alert – let’s reveal why.
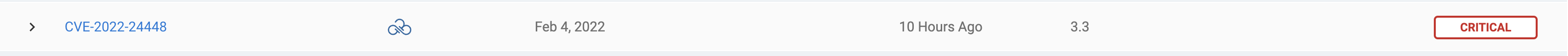
Digging deeper, we see several virtual machines in seemingly harmless environments.
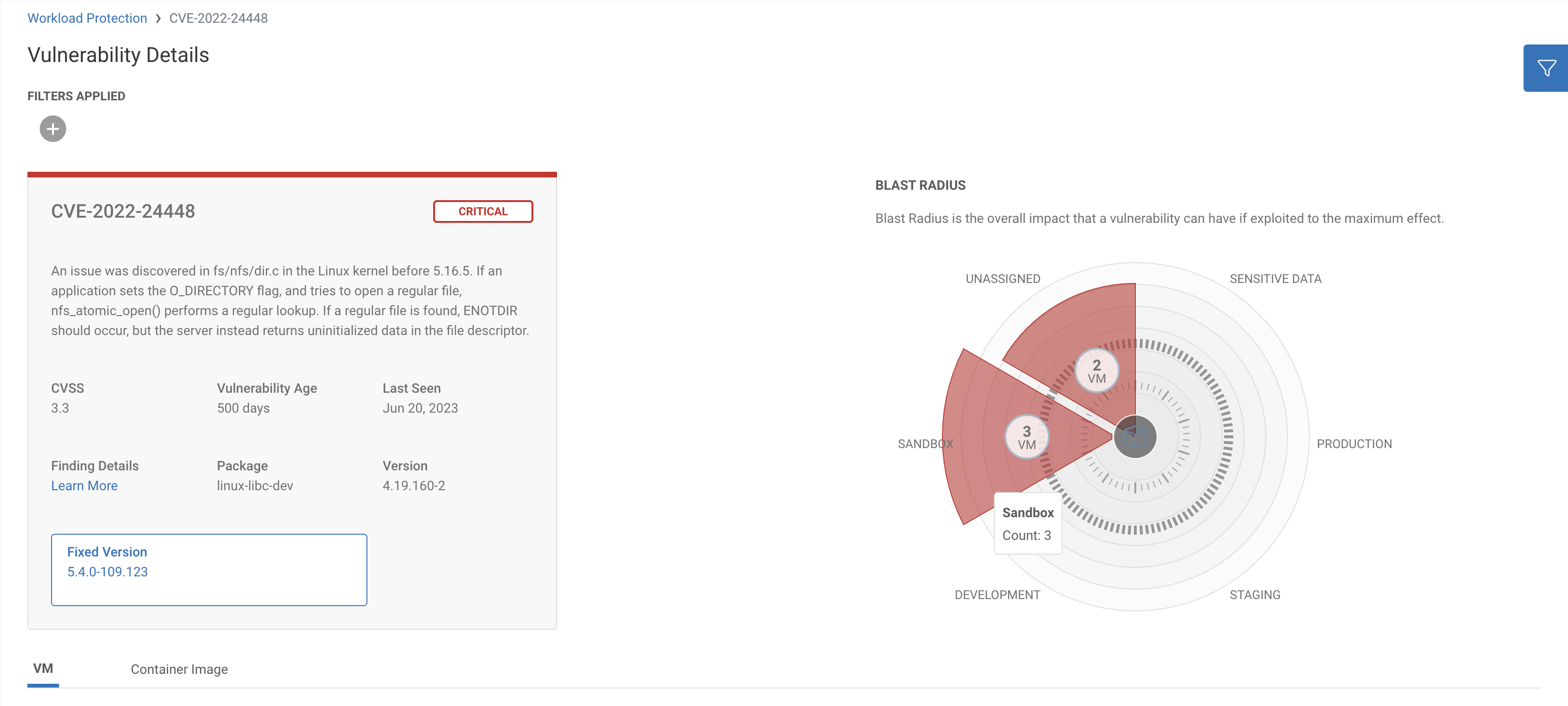
But, investigating further into the Sandbox environment, Sonrai’s Platform shows there’s actually several high and critically rated virtual machine risks.
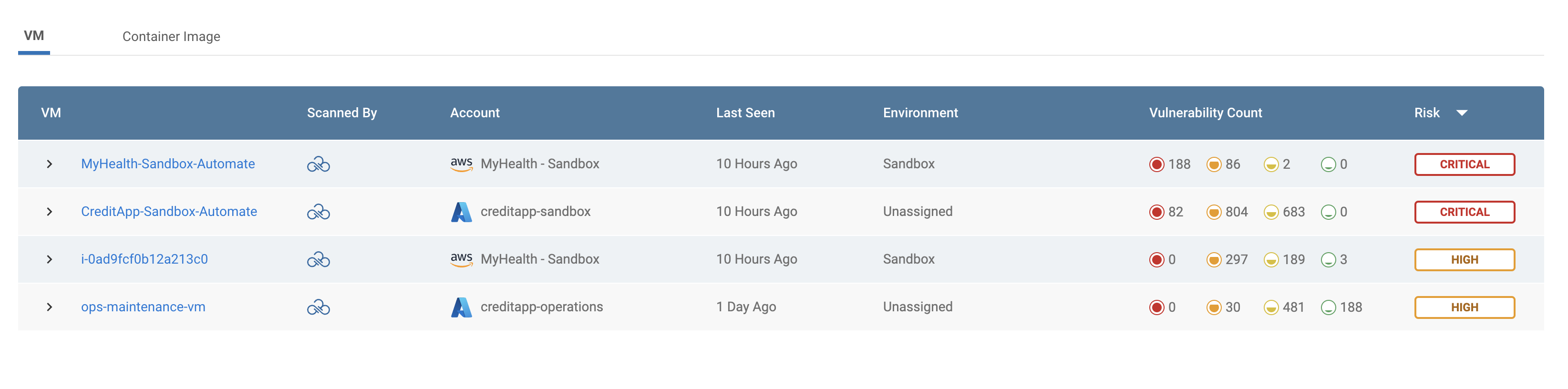
Let’s consider VM: CreditApp-Sandbox-Automate. Sonrai is able to detect numerous Risk Amplifiers on the network and identity level that skyrocket the severity of this alert in a sandbox environment.
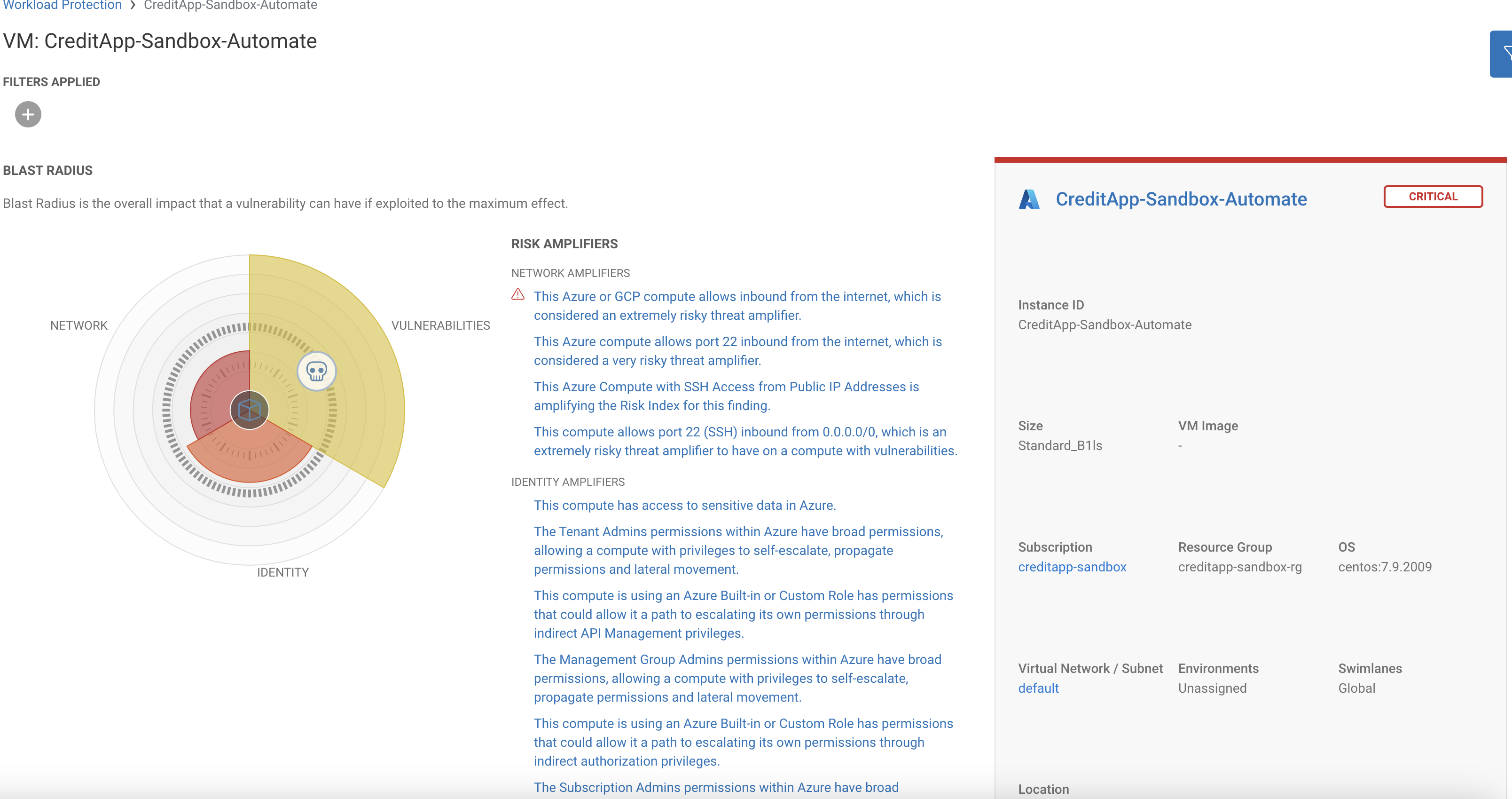
Picking just one example Risk Amplifier, ‘The management group admins permissions within Azure have broad permissions allowing a compute with privileges to self escalate, propagate permissions and lateral movement.’ Sonrai details the actual permission-path allowing this.
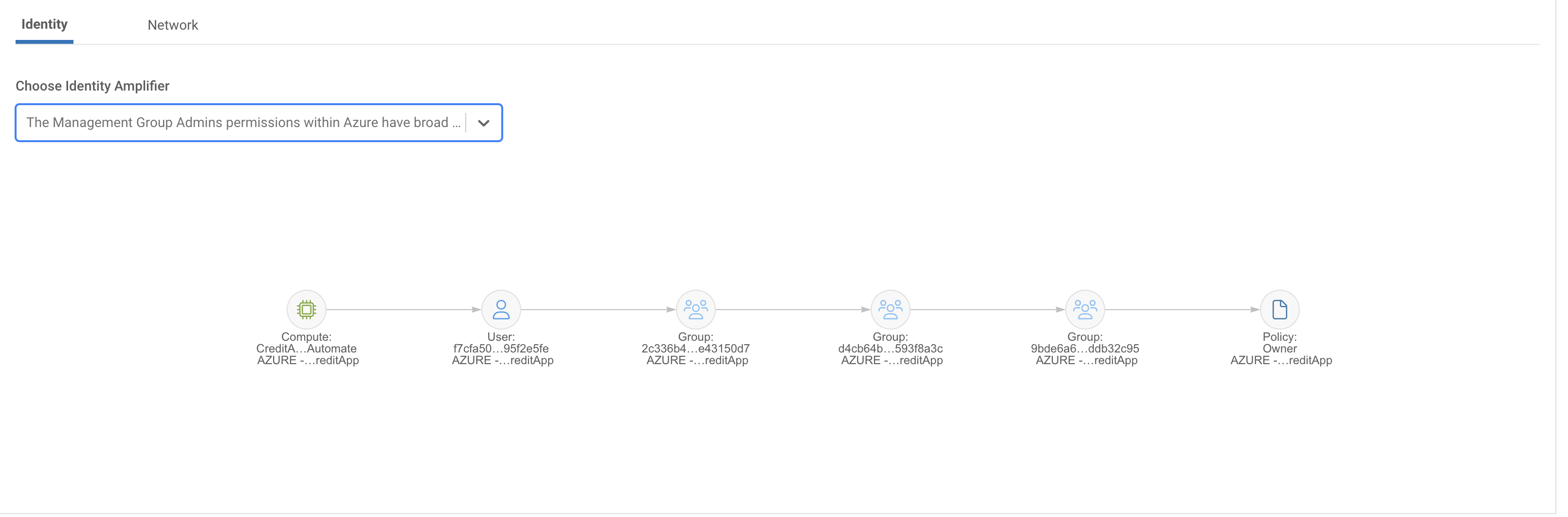
And there you have it, a low CVSS score rated vulnerability, that Sonrai is able to determine is a real business concern due to a piece of compute’s ability to inherit privileges through several Azure Groups and ultimately access data in a sensitive application.
Prioritized Remediation with Risk Insights
As we’ve said, prioritization intelligence alone is not enough. Sonrai’s Risk Insights dashboard is a central location detailing your cloud estate’s greatest risks to remediate first. This is visualized from both systemic and strategic viewpoint, as well as one-off actionable items under ‘5 Things You Can Do Right Now.’ The goal is the greatest risk reduction in the most efficient means.
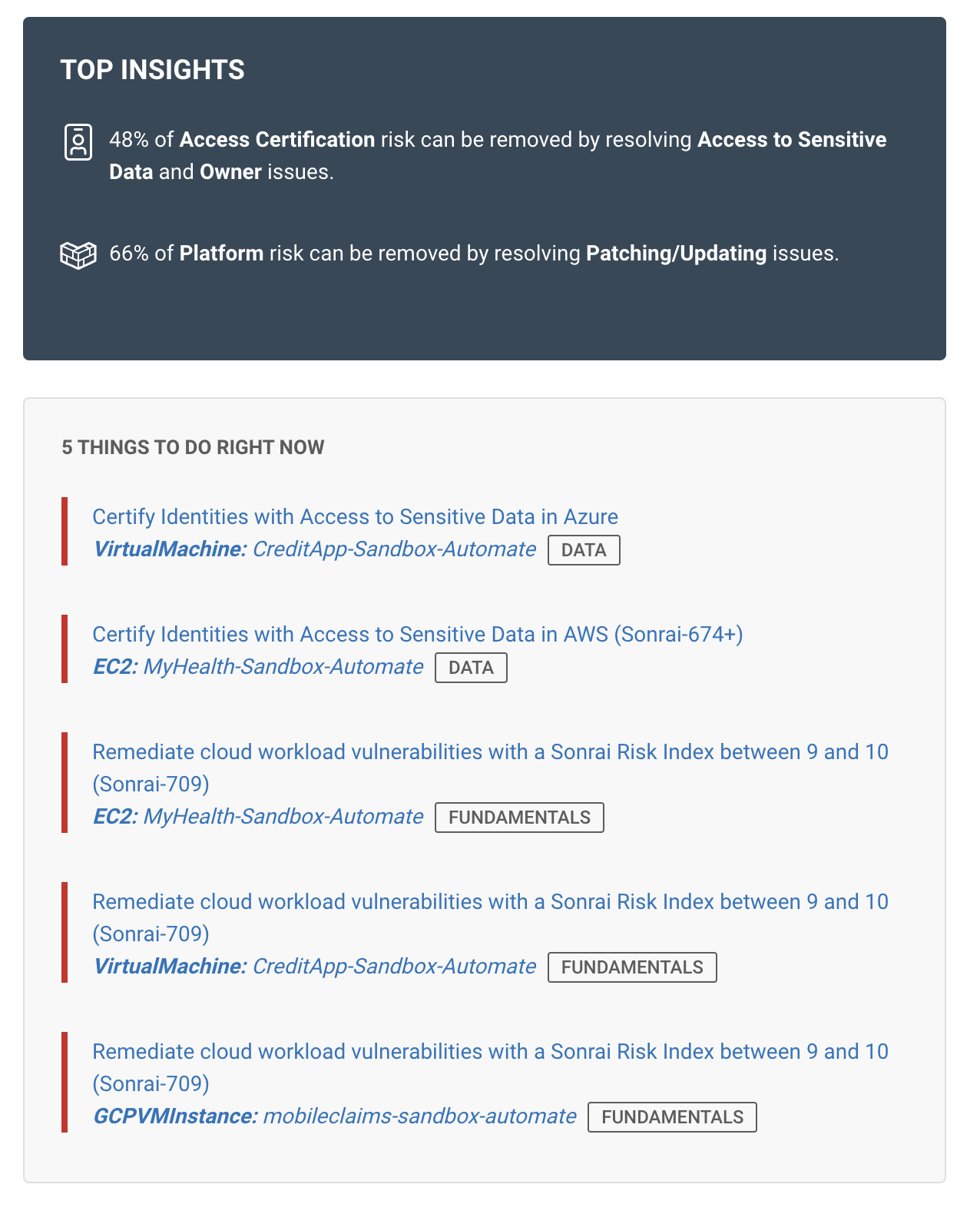
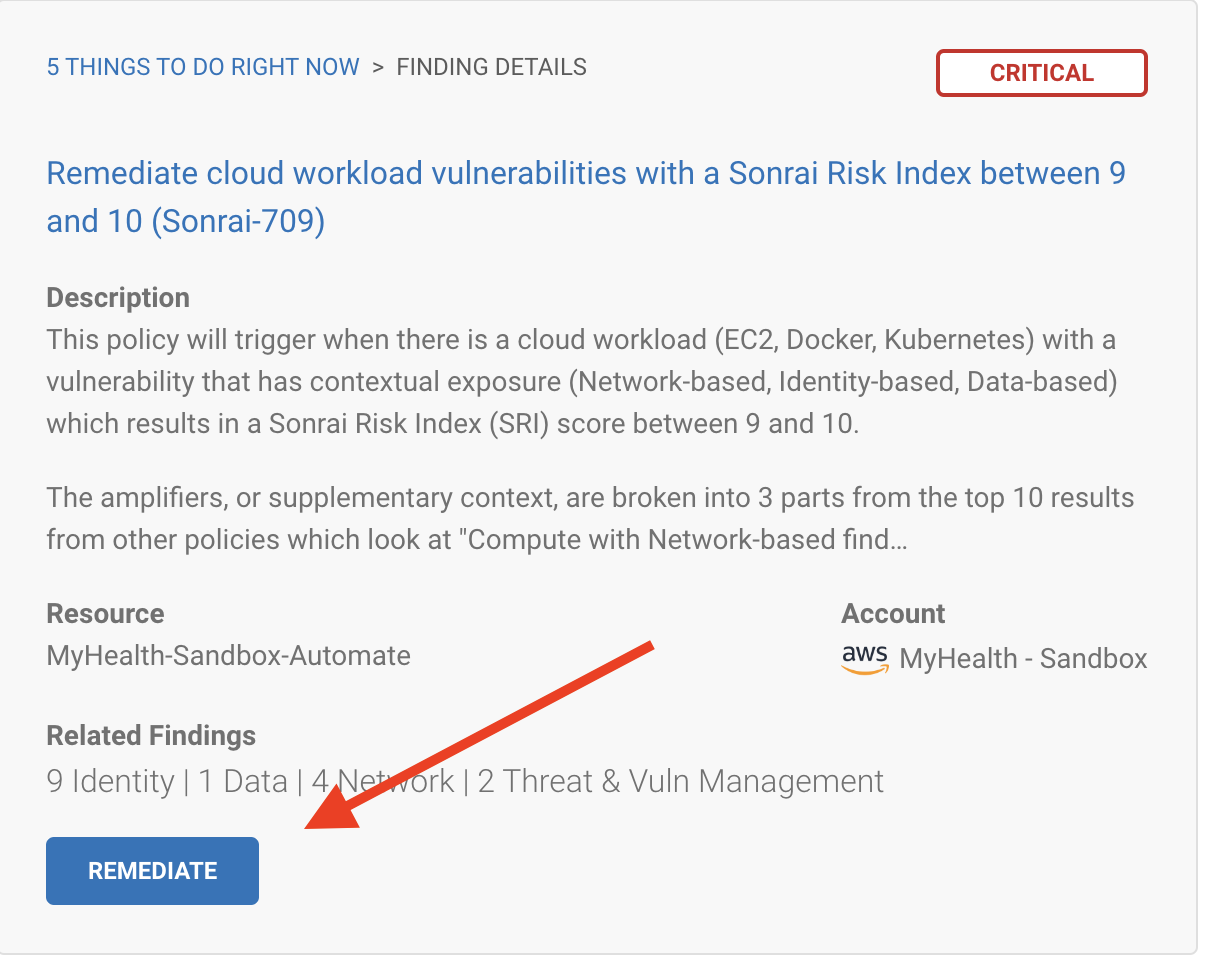
Clicking into any of these, you’d find a ‘remediation’ option where Sonrai offers either detailed instructions for your console or CLI code, and automated bot remediation.
Reducing Risk: Doing More, With Less
No alert or security risk exists in your cloud in total isolation. Sensitivity of the violation itself, the environment in which it exists and if there are any connection points to overprivileged identities or critical data all influence how urgent an alert is. Understanding the context behind every risk enables your teams to tackle the business critical concerns first – and, with Sonrai’s help, locate those quick fixes that would have a major risk reduction impact across your estate.
Save time, save resources, and prevent attacks by fixing serious alerts, first.
To witness how Sonrai offers prioritized actions for remediation, consider requesting a demo or watching an on-demand version available now.

*** This is a Security Bloggers Network syndicated blog from Sonrai | Enterprise Cloud Security Platform authored by Tally Shea. Read the original post at: https://sonraisecurity.com/blog/reduce-risk-efficiently-save-time-with-prioritized-actions/
Original Post URL: https://securityboulevard.com/2023/06/reduce-risk-efficiently-save-time-with-prioritized-actions/
Category & Tags: Cloud Security,DevOps,Security Bloggers Network,DEVOPS,Governance Automation – Cloud Security,DevOps,Security Bloggers Network,DEVOPS,Governance Automation
Views: 2