Source: levelblue.com – Author: hello@alienvault.com.
Summary
Preparing evidence for a HITRUST Validated Assessment is a detailed process that requires careful organization, proper documentation, and alignment with HITRUST’s control framework. By following the below steps, you will be better prepared for the HITRUST Validated Assessment, increasing your chances of successfully achieving certification. The key is thorough, well-organized evidence collection, clear documentation, and ensuring that the evidence directly demonstrates compliance with the HITRUST CSF controls.
Below are the essential steps to prepare the necessary evidence.
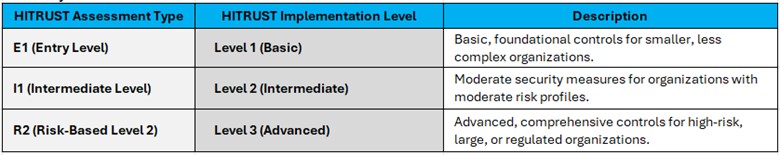
Understand the HITRUST CSF and Your Implementation Level
- HITRUST CSF (Common Security Framework) outlines a comprehensive set of controls across various security, privacy, and regulatory domains.
- Review the relevant controls for your implementation level (Level 1, Level 2, or Level 3), as the evidence required will vary based on the level of complexity and risk associated with your organization.
- Familiarize yourself with the HITRUST validated assessment process, which includes external validation from a HITRUST assessor.
Develop a Detailed Evidence Collection Plan
Create an evidence collection plan that specifies:
- What evidence is needed to demonstrate compliance for each control.
- Who is responsible for gathering the evidence (e.g., IT, security, compliance, HR).
- When the evidence needs to be collected, ensuring it is current and covers the assessment period.
Gather Evidence for Each HITRUST Control
For each HITRUST control, the evidence should clearly demonstrate how the control is implemented and functioning. Evidence can include:
Policies and Procedures:
- Provide up-to-date documentation of your organization’s policies, procedures, and practices relevant to HITRUST control requirements (e.g., data protection, incident response, access control).
System Configurations and Technical Evidence:
- Provide screenshots, configuration files, or diagrams that show the implementation of technical controls like firewalls, encryption, access restrictions, etc.
Audit Logs:
- Provide logs from security systems such as SIEM (Security Information and Event Management), firewalls, and other monitoring tools that demonstrate compliance with specific controls (e.g., continuous monitoring, access management).
Risk Assessments and Remediation Plans:
- Include documentation showing the results of risk assessments, identified risks, and steps taken to remediate or manage them.
Training and Awareness Records:
- Provide records showing that employees received required security awareness training and any role-specific training on compliance policies.
Third-Party Assessments:
- If applicable, include evidence from third-party audits or certifications (e.g., ISO 27001, SOC 2) that support your compliance.
Ensure the Evidence is Accurate, Current, and Relevant
- Date Stamp: Ensure that the evidence includes timestamping (e.g., date and time) to verify when the evidence was generated and to confirm it is relevant to the current assessment period.
- Source Systems: Identify and document the source system where the evidence originated (e.g., SIEM tool, firewall system, employee training platform). This adds authenticity to the evidence.
- Evidence Description: Provide clear, concise descriptions for each piece of evidence. Describe the purpose of the evidence and how it demonstrates compliance with the specific HITRUST control.
Example of Evidence Description:
- “This screenshot shows the configuration settings for our firewall, which block all inbound traffic except for specific, authorized IP addresses. This supports compliance with the access control policy.”
Organize and Index the Evidence
- Organize the evidence by control family (e.g., Risk Management, Access Control, Incident Response) or by the specific HITRUST control number.
- Ensure that each piece of evidence is clearly labeled and cross-referenced to the corresponding HITRUST control it supports.
- Use evidence mapping document or index to track and link evidence to specific controls, ensuring nothing is overlooked.
Ensure Evidence Integrity
- Maintain the integrity of your evidence to prevent tampering or alteration. This is especially important for logs or audit trails.
- Consider using methods such as digital signatures or encryption for sensitive evidence to ensure it cannot be altered.
- For logs or reports, ensure that timestamps and audit trails are visible.
Review and Validate Evidence Internally
- Conduct internal evidence walkthroughs to ensure that all evidence is accurate, up-to-date, and appropriately linked to HITRUST controls.
- Have internal stakeholders (IT, compliance, security teams) review the evidence to verify its relevance and completeness.
- Perform a gap analysis to ensure that all necessary evidence is collected and that any control gaps are identified and addressed before the external assessment.
Prepare for Evidence Walkthroughs with the Assessor
- During the validated assessment, an external HITRUST assessor will review your evidence and may ask for further clarifications or details.
- Be ready to walk through the evidence and explain how it demonstrates the effectiveness of your security controls.
- Prepare your team to answer questions about the evidence in a clear and concise manner.
Keep Evidence Accessible and Organized
- Keep all evidence well-organized and easily accessible for the assessment. This is particularly important if the assessor requests additional details during the walkthrough.
- Use a centralized repository (digital folder or GRC system) for evidence storage that is both secure and organized by control family or assessment category.
Ensure Compliance with Privacy Regulations
- If you handle sensitive data (such as PII or PHI), make sure that your evidence collection process complies with privacy regulations (e.g., GDPR, HIPAA).
- Secure sensitive information and follow internal guidelines for managing data privacy during the evidence collection process.
Prepare for the Final Assessment
- Once all evidence has been collected and reviewed, schedule the formal HITRUST Validated Assessment.
- During the assessment, be prepared for an assessor to review the evidence and potentially request clarifications or additional documentation.
Additional Resources:
Original Post url: https://levelblue.com/blogs/security-essentials/preparing-evidence-for-a-validated-hitrust-assessment
Category & Tags: –
Views: 2




















































