Source: heimdalsecurity.com – Author: Andreea Chebac
Chinese researchers discovered a new type of attack targeting smartphones. BrutePrint is a brute-force attack that can bypass fingerprint authentication. They managed to breach security measures enabled for brute-force attacks like attempt limits and liveness detection.
Brute-force attacks use numerous trial-and-error attempts to decipher a key, or password in order to obtain access to accounts without authorization.
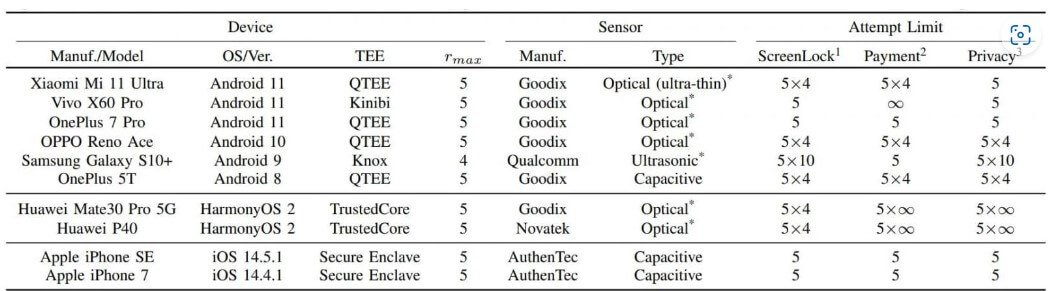
Experts tested the new method on ten smartphone models. These tests resulted in unlimited login attempts on all Android and HarmonyOS (Huawei) phones and ten additional attempts on iOS devices.
How BrutePrint Attacks Work
Researchers at Tencent Labs and Zhejiang University explained that they exploited two vulnerabilities in this attack: Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL). As well as that the Serial Peripheral Interface (SPI) of the fingerprint sensors’ biometric data was insufficiently safeguarded, making it possible for a man-in-the-middle (MITM) attack to steal fingerprint images.
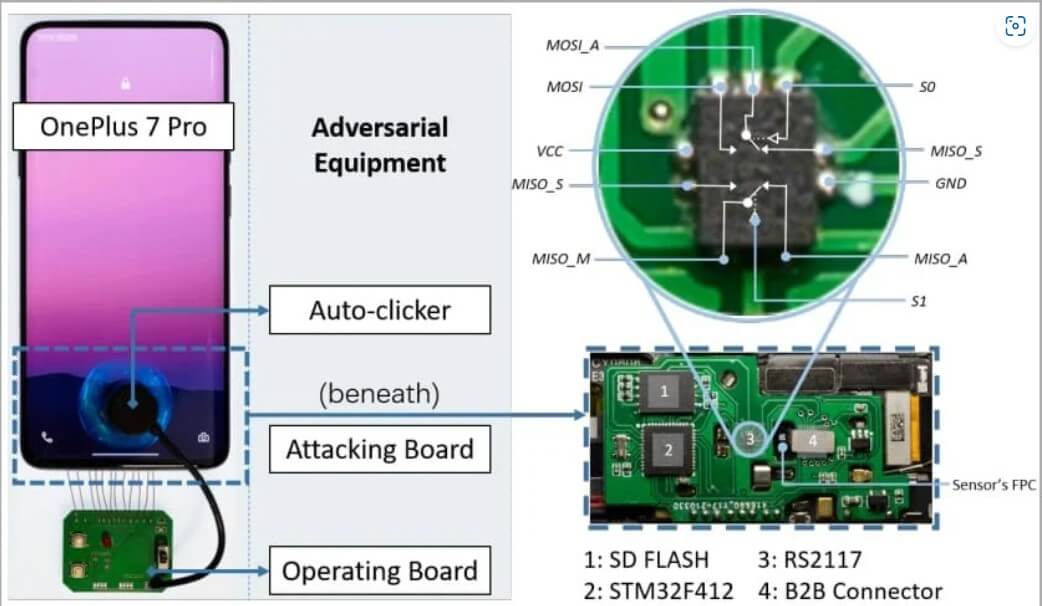
The main goal of this type of brute-force attack is to allow intruders to an unlimited number of attempts in unlocking a device using a fingerprint match.
For a BrutePrint attack, hackers need proximity to the device, a fingerprint database, and $15 worth of equipment.
Contrary to how password cracking works, fingerprint matches use a reference threshold instead of a specific value, so attackers may manipulate the False Acceptance Rate (FAR) to increase the acceptance threshold and create matches more easily.
BrutePrint stands in between the fingerprint sensor and the Trusted Execution Environment (TEE) and exploits the CAMF flaw to manipulate the multi-sampling and error-canceling mechanisms of fingerprint authentication on smartphones.
Cancel-After-Match-Fail (CAMF) vulnerability inserts an error in the fingerprint data that stops the authentication process. This way, threat actors can try an infinite number of fingerprints on the device without triggering the security system.
The Match-After-Lock (MAL) bug allows them to continue the authentication attempts even when the device is in “lockout mode”. The lockout mode activates after a number of failed attempts, and it shouldn’t allow any more attempts for a while.
To close up, the BrutePrint attack enables a transfer system. This makes all the images from the fingerprint database look like the targeted device scanned them. This tricks the scanning sensor into thinking that it is a valid image.
The Results of the BrutePrint Tests
Specialists tested the attack method on Android and iOS devices. The results show that all of them had at least one weakness that made them vulnerable.
Android devices permit an endless number of fingerprint trials, making it practically viable to brute-force the user’s fingerprint and unlock the device. However, the authentication security on iOS is significantly stronger and efficiently thwarts brute-force attacks.
Although the researchers found that iPhone SE and iPhone 7 are vulnerable to CAMF, they could only increase the fingerprint tryout count to 15, which isn’t enough to brute-force the owner’s fingerprint.
Regarding the SPI MITM attack that involves hijacking the user’s fingerprint image, all tested Android devices are vulnerable to it, while iPhones are again resistant.
The researchers explain that the iPhone encrypts fingerprint data on the SPI, so any interception has little value in the context of the attack.
For a successful BrutePoint attack the time ranges from 2.9 to 13.9 hours, when the user has enrolled one fingerprint. And from 0.66 to 2.78 hours, when multiple fingerprints are enrolled.
In conclusion, although for now, this type of cyberattack is a slow one, criminals and thieves could use it to unlock stolen smartphones.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/new-type-of-attack-bruteprint-can-breach-your-smartphones-fingerprint-security/
Category & Tags: Cybersecurity News,Uncategorized – Cybersecurity News,Uncategorized




















































