Source: www.infosecurity-magazine.com – Author:
The lines between cybercrime and espionage are increasingly blurring, eroding the traditional distinctions between criminal hackers and state-sponsored actors.
In a report published on June 30, Proofpoint highlighted substantial overlaps between two malicious campaigns.
One originated from TA829, a hybrid hacking group that conducts both cyber extortion and pro-Russian cyber espionage activities, and the other from a newly identified cybercriminal cluster tracked as UNK_GreenSec.
While it is unclear how the known threat actor and the new cluster are linked, Proofpoint estimated that the similarities between the two groups’ activities suggests that the barriers between cyber espionage and cybercrime are dissolving.
TA829, A Cyber Extorsion Group Conducting Cyber Espionage
TA829 is a unique hybrid threat actor. Initially tracked as a financially motivated group, TA829 also regularly conducts espionage campaigns using the same custom tool suite.
Following the invasion of Ukraine, TA829 began conducting targeted espionage campaigns in Ukraine, in alignment with Russian state interests, in addition to its more traditional cyber extortion campaigns.
TA829’s typical techniques, tactics and procedures (TTPs) involve phishing campaigns to deploy variants of its SingleCamper (aka SnipBot) an updated version of the RomCom backdoor or the lightweight DustyHammock malware.
The group’s automated and scaled processes, such as the regular updating of packers and loaders, the use of varied sending infrastructure and source addresses for each target and the use of extensive redirection chains to detect and evade researchers, are more typical of cybercriminals compared to espionage.
However, it also deploys higher-end capabilities, such as the use of browser or operating-system zero-day exploits, in dedicated espionage campaigns.
The Proofpoint researchers tracking TA829 noted that the group’s activity overlaps with that of other groups and clusters tracked by different vendors, such as RomCom, Void Rabisu, Storm-0978, CIGAR, Nebulous Mantis and Tropical Scorpius.
“It is unclear if the actor’s capabilities are co-opted for the espionage campaigns, or if there is some other form of guidance or tasking from the Russian government,” said the researchers.
Four TA829-Like Campaigns Attributed to a New Cluster
According to Proofpoint, TA829’s activity has been relatively quiet over the past year until the group resurfaced in February 2025 with a series of campaigns aimed at deploying a previously unobserved malware payload.
Upon investigating these February campaigns, the Proofpoint researchers noticed that four of them featured the hallmark characteristics of TA829 activity, but contained notable differences, including message volumes in the thousands targeting a broader set of industries and geographies, lure themes that consistently referenced job applications and hiring and the unique payload that came to be known as TransferLoader.
They attributed these four campaigns to a new cluster that tracked as UNK_GreenSec.
TA829 and UNK_GreenSec: Similarities and Differences
The most recent TA829 campaigns and the four campaigns attributed to UNK_GreenSec share many similarities, including:
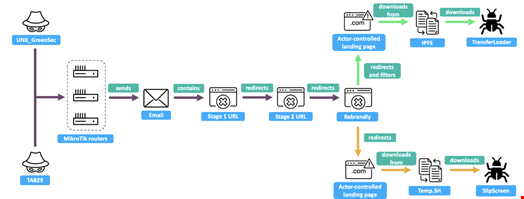
- Delivery: Both actors rely on REM Proxy services, which are likely rented to users to relay traffic and deployed on compromised MikroTik routers as part of their upstream sending infrastructure. Proofpoint also hypothesized that the actors share an email builder utility that allows the bulk creation and sending of these emails via REM Proxy nodes
- Phishing emails: The emails in both campaigns are comprised of plaintext message bodies that contain a link to an actor-controlled domain, either directly in the body or in an attached PDF. The messages are themed around job seeking or complaints against the targeted entity and the content is generic enough to be reused across the campaign, but with a unique link for each target
- Phishing links: Upon opening the link, a series of redirectors routes real users to a landing page that spoofs OneDrive or Google Drive, the landing pages display a link to a download site, which in turn drops a signed loader that spoofs a PDF
The main differences are in the group’s infrastructure and how the payloads – SingleCamper and DustyHammock for TA829, TransferLoader for UNK_GreenSec – are deployed and installed.
Four Hypotheses About the TA829-UNK_GreenSec Link
While there is not sufficient evidence to substantiate the exact nature of the relationship between TA829 and UNK_GreenSec, there is very likely a link between the groups, according to Proofpoint.
The researchers have suggested four potential hypotheses:
- TA829 and UNK_GreenSec buy distribution and infrastructure from the same third-party provider
- TA829 procures and distributes its own infrastructure, and provided those services temporarily to UNK_GreenSec
- UNK_GreenSec is the infrastructure and distribution provider, that normally sells to TA829 operators, and temporarily used those services to deploy its own malware, TransferLoader
- The two clusters are the same actor, and TransferLoader is a new family in the testing phase from TA829
“In the current threat landscape, the points at which cybercrime and espionage activity overlap continue to increase, removing the distinctive barriers that separate criminal and state actors. Campaigns, indicators, and threat actor behaviors have converged, making attribution and clustering within the ecosystem more challenging,” the Proofpoint researchers concluded.
Original Post URL: https://www.infosecurity-magazine.com/news/major-overlaps-cybercrime-espionage/
Category & Tags: –
Views: 0



















































