Source: securityaffairs.com – Author: Pierluigi Paganini

New ReaderUpdate malware variants, now written in Crystal, Nim, Rust, and Go, targets macOS users, SentinelOne warns.
SentinelOne researchers warn that multiple versions of the ReaderUpdate malware written in Crystal, Nim, Rust, and Go programming languages, are targeting macOS users.
ReaderUpdate is a macOS malware loader that has been active since 2020, the malicious code was first seen as a compiled Python binary and was spotted delivering Genieo adware.
it remained largely undetected until resurfacing in late 2024 with new variants written in Crystal, Nim, and Rust.
1/ As the holiday season approaches, we’ve identified a new suspicious binary written in Nim. It contacts a C2 server, gains persistence, and collects system information. While only one sample is currently detected by antivirus tools, many others remain undetected. Read more 👇 pic.twitter.com/H9gEFvuCHb
— Moonlock Lab (@moonlock_lab) December 18, 2024
SentinelOne says that the ReaderUpdate is currently distributed in five variants compiled from five different source languages.
| Language | ~Size | Example SHA-1 |
| Compiled Python | 5.6Mb | fe9ca39a8c3261a4a81d3da55c02ef3ee2b8863f |
| Go | 4.5Mb | 36ecc371e0ef7ae46f25c137aa0498dfd4ff70b3 |
| Crystal | 1.2Mb | 86431ce246b54ec3372f08c7739cd1719715b824 |
| Rust | 400Kb | 01e762ef8a10bbcda639ed62ef93b784268d925a |
| Nim | 166Kb | 21a2ec703a68382b23ce9ff03ff62dae07374222 |
New ReaderUpdate variants are spread via older infections and third-party downloads, often through trojanized apps like “DragonDrop.” All versions are Intel x86-only, requiring Rosetta 2 on Apple Silicon. Recent reports have analyzed Crystal, Nim, and Rust versions, while the Go variant is now being documented for the first time.
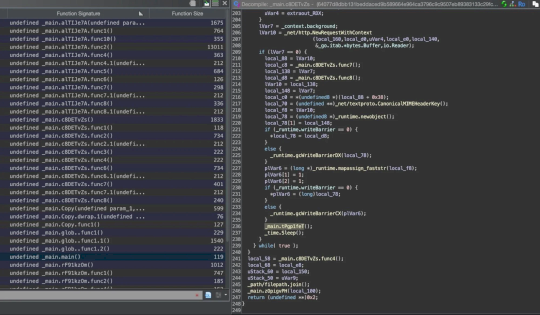
The Go variant of the malware analyzed by the researchers collects system hardware info for unique victim IDs and hides in ~/Library/Application Support/. The malware maintains persistence via a .plist file. It executes remote C2 commands, SentinelOne experts believe that the malicious code might be used to offer other threat actors Pay-Per-Install (PPI) or Malware-as-a-Service (MaaS).
The malware obfuscates strings and URLs to evade analysis.
“Throughout the binary, the developers obfuscate many of the strings, including the C2 URL and the property list content, using functions that either assemble characters on the stack or run some simple character substitution algorithm.” reads the report.

While Nim, Crystal, and Rust variants are widespread, the Go version is rarer, with only nine samples observed, linked to seven domains tied to broader malware infrastructure.
“ReaderUpdate is a widespread campaign utilising binaries written in a variety of different source languages, each containing its own unique challenges for detection and analysis. Interestingly, this loader platform has been quietly infecting victims through old infections that went largely unnoticed due to the malware remaining dormant or delivering little more than adware.” concludes the report.
“Nevertheless, where compromised, hosts remain vulnerable to the delivery of any payload the operators choose to deliver, whether of their own or sold as Pay-Per-Install or Malware-as-a-Service on underground markets.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
Original Post URL: https://securityaffairs.com/175891/malware/readerupdate-malware-variants-targets-macos.html
Category & Tags: Breaking News,Cyber Crime,Malware,Cybercrime,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,ReaderUpdate,Security News – Breaking News,Cyber Crime,Malware,Cybercrime,Hacking,hacking news,information security news,IT Information Security,malware,Pierluigi Paganini,ReaderUpdate,Security News
Views: 4