Source: www.infosecurity-magazine.com – Author:
Written by

A sophisticated Phishing-as-a-Service (PhaaS) platform has been identified spoofing over 100 brands to steal credentials, new research from Infoblox Threat Intel has found.
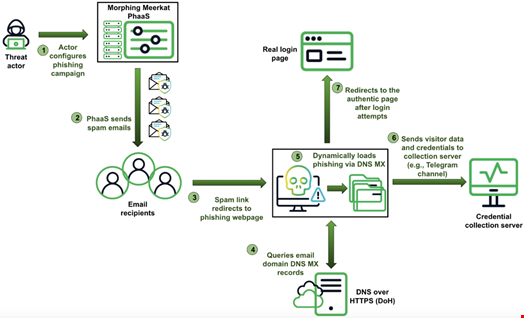
The threat actor behind these campaigns has been dubbed ‘Morphing Meerkat’. As part of its tactics, techniques and procedures (TTP), it employs DNS email exchange (MX) records to serve fake logging pages and steal credentials.
When a victim clicks on a phishing link, the phishing kit queries the MX record of the victim’s email domain to determine their email service provider.
Based on the MX record, the phishing kit dynamically serves a fake login page that mimics the victim’s real email service provider’s login page.
In its research blog, Infoblox said that it has discovered that Morphing Meerkat has sent thousands of spam emails.
Infoblox explained that this novel DNS technique allows threat actors to customize content for victims using mail configurations that exist for other purposes. It is a DNS version of the technique referred to as “living off the land”, in which threat actors use elements of the existing environment to hide.
With the stolen credentials, cybercriminals can infiltrate corporate networks, steal sensitive data and even launch further attacks.
Morphing Meerkat Phishing Kit Evolves
Virtually all Morphing Meerkat attacks target email user login credentials, and the developers of the PhaaS platform appear to have designed it specifically for this kind of activity.
Infoblox said it first identified campaigns that used this phishing kit as early as 2020.
The early version was only capable of serving phishing web templates disguised as five email brands: Gmail, Outlook, AOL, Office 365 and Yahoo. They also had no translation module, so the kits could only display English text in the phishing templates.
There are now 114 brand designs.
By July 2023, the kits could dynamically load phishing pages based on DNS MX records. Today, the phishing kits can also dynamically translate text based on the victim’s web profile and target users in over a dozen different languages.
Morphing Meerkat also uses a large number of security evasion features compared to other phishing kits, according to Infoblox. This includes using open redirects on adtech servers and obfuscating code to hinder analysis.
To avoid suspicion, the phishing kit often redirects the victim to the real login page of their email service provider after a couple of failed login attempts.
Infoblox Recommends Strong DNS Security
Infoblox noted that the Morphing Meerkat phishing kit shows how cybercriminals exploit security blind spots using advanced techniques like DNS cloaking and open redirects.
Organizations can protect themselves against these kinds of attacks by adding a strong layer of DNS security to their systems.
This involves tightening DNS control so that users cannot communicate with DoH servers or blocking user access to adtech and file sharing infrastructure not critical to the business.
If companies can reduce the number of unimportant services in their network, they can reduce their attack surface, giving fewer options to cybercriminals for threat delivery, Infoblox concluded.
Original Post URL: https://www.infosecurity-magazine.com/news/morphing-meerkat-phaas-platform/
Category & Tags: –
Views: 5




















































