Source: securityboulevard.com – Author: Don Hoffman
Last week, the BlackCat ransomware group (also known as ALPHV) attacked the operations of MGM Resorts and forced them to shut down their IT systems. What sets this attack apart from more traditional ransomware attacks is that at a certain point attackers were able to leverage their domain dominance of the on-prem environment to compromise the cloud identity infrastructure, harvesting cleartext passwords of Okta users.
The attack now joins others – including against Okta, Uber, and Cisco – in marking a new pattern that exploits the interconnectivity of the on-prem and SaaS environments to compromise the SaaS through the on-prem. This introduces a significant risk for all organizations today that have a hybrid environment (i.e., employing both an on-prem and a cloud directory) and emphasizes the need of a unified identity protection approach.
MGM Breach: Walking Through the Attack’s Stages
From publicly available data we can construct the following flow:
- Attackers got information on LinkedIn about an employee, called the help desk and used social engineering to get access to the network.
- Following that, they performed lateral movement until they gained access to a domain controller (details on the exact techniques used in this stage remain unclear) and stole user passwords stored there.
- At this point, the attackers asked for the ransom and, when it was refused, subsequently installed ransomware on MGM’s ESXi servers, then persisted in their lateral movement until gaining access to Okta server.
- Once there, the attackers exfiltrated cleartext passwords from servers that then gave them the ability to log into Okta and access any of the SaaS apps it manages.
On-Prem Domain Dominance Used as a Stepping Stone to the SaaS Environment
What’s interesting about this attack is that while hackers had access to Active Directory (AD) hashes, they did not have access to the passwords. Attackers used AD to pivot to Okta and managed to steal plaintext passwords. Essentially, Active Directory served as a gateway to Okta. This highlights the need for organizations to identify and address any weaknesses and misconfigurations in their identity infrastructure. Many organizations connect Active Directory to Okta but often overlook securing this connection, which in this case provided attackers with an opportunity to exploit the weakness.
The Critical Gap of Hybrid Identity Infrastructure: Connected but Not Protected
This breach highlights an inherent weakness that is all too commonly ignored – the fragmented and siloed nature of the identity infrastructure in the hybrid environment. Let’s now dive into this in more detail.
Most organizations manage their on-prem users in Active Directory. In parallel, they manage the same users in a cloud directory of a federation server (e.g., Entra ID, Okta, Ping, etc.). To enable users to have a seamless login experience, these two different identity providers are synced – meaning that the same username and password combination is used to access both the on-prem and the SaaS resources. Additionally, the directory used for the SaaS apps often has some footprint in the on-prem environment (for example, the Okta server in the case of this breach).
This connection implies that if an attacker has successfully compromised user credentials in the on-prem environment, they can then use them to directly log in to SaaS apps as well as move laterally and compromise the cloud identity infrastructure components in the on-prem environment.
The On-Prem’s Exposure to Identity Threats Makes it the Ultimate Attack Vector to Compromise SaaS
The recent white paper published by Osterman Research, “The State of the Identity Attack Surface: Insights into Critical Security Gaps,” clearly shows that the on-prem environment is critically vulnerable to the use of compromised credentials for malicious access.
As the report details, traditional multi-factor authentication (MFA) and Privileged Access Management (PAM) solutions fail to provide sufficient real-time protection against identity threats for the vast majority of organizations.
Threat actors are painfully aware of these blind spots and leverage them in performing lateral movement within the on-prem environment, encountering little to no resistance. And lateral movement is the X factor that turns a local event (such as a single compromised machine) into an enterprise-level incident, as the MGM breach illustrates.
Conclusion: Identity Protection for On-Prem Equals Identity Protection for the Cloud
Any chain is only as strong as its weakest link. And the hybrid environment is a chain where the on-prem and cloud are closely interwoven. Thus, strengthening the on-prem environment means strengthening the whole chain. Regardless of how far you’ve come in your cloud migration, if you still have an on-prem portion this is a serious exposure you need to address.
But how exactly can organizations address this gap? After all, even before there was a cloud, there was no security solution that could mitigate the risk of lateral movement and prevent it in real time.
Silverfort Unified Identity Protection Platform: Blocking Lateral Movement in Real Time
Silverfort has pioneered the first Unified Identity Protection platform that’s purpose built to prevent identity threats in real time across any user, system, and environment. Silverfort integrates with the on-prem and cloud identity infrastructure to provide continuous monitoring, risk analysis and controls such as MFA or access blocking on every authentication and access attempt.
In this way, Silverfort can bring identity protection to resources that could have never been protected before. An example is access to workstations and servers over command line via tools such as PsExec or Remote PowerShell. This type of access is the default way attackers perform lateral movement and is beyond the coverage of traditional MFA solutions. Silverfort is the first solution able to require MFA to detect and block malicious access of this type.
How Silverfort Could Have Prevented an MGM-Like Attack Scenario
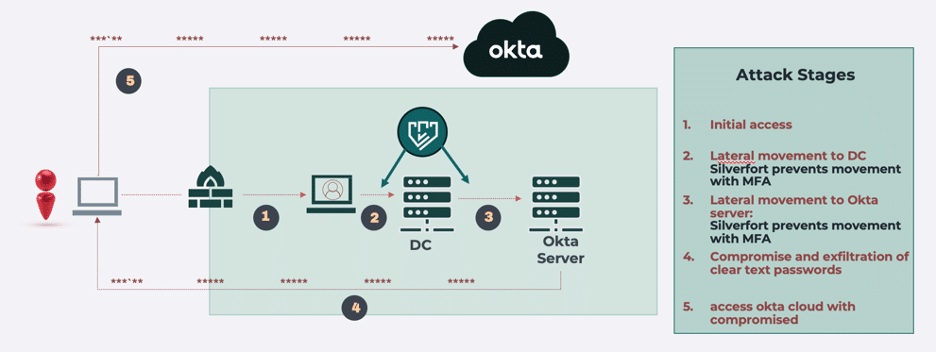
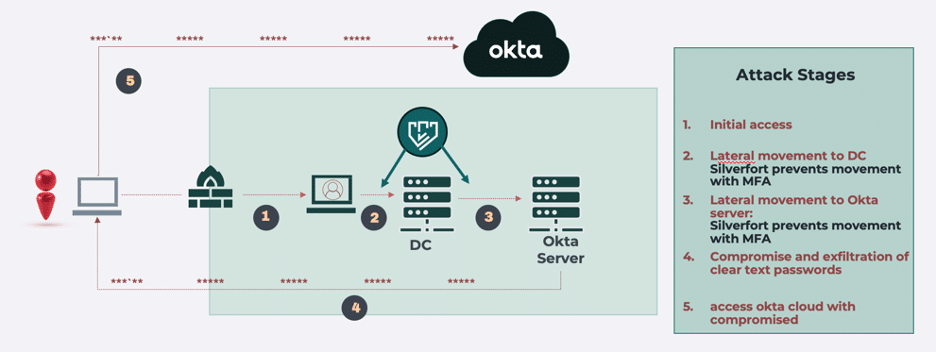
As previously stated, it’s unclear exactly how the attackers performed the lateral movement attack in the network. But it is likely that Silverfort could have prevented this breach in two ways:
- Silverfort would have likely detected the lateral movement to Active Directory, stopping the attackers before they could compromise it.
- Alternatively, Silverfort would likely have detected the attackers moving from AD to Okta, thus preventing the compromise of the Okta server.
The diagram below illustrates how Silverfort’s protection would have stopped the attack in its early stages:
Does your organization have a hybrid environment? Find out more about how Silverfort can help reduce your risk. Schedule a call with one of our experts.
The post MGM Breach Takeaway: On-Prem Has Become Attackers’ Gateway to the Cloud appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Blog – Silverfort authored by Don Hoffman. Read the original post at: https://www.silverfort.com/blog/mgm-breach-takeaway-on-prem-has-become-attackers-gateway-to-the-cloud/
Original Post URL: https://securityboulevard.com/2023/09/mgm-breach-takeaway-on-prem-has-become-attackers-gateway-to-the-cloud/
Category & Tags: Cloud Security,Security Bloggers Network,Threats & Breaches,Attack,Breach,Cloud,Combatting Identity Threats,hybrid,lateral movement,On-prem,Ransomware,SaaS – Cloud Security,Security Bloggers Network,Threats & Breaches,Attack,Breach,Cloud,Combatting Identity Threats,hybrid,lateral movement,On-prem,Ransomware,SaaS
Views: 3