Source: securelist.com – Author: Kaspersky Security Services

minute read

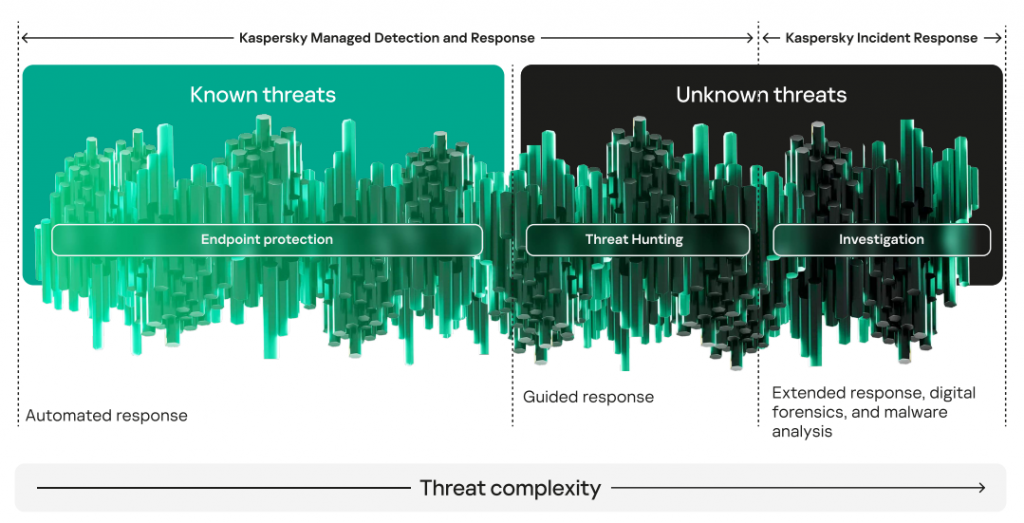
Kaspersky Managed Detection and Response (MDR) is a service for 24/7 monitoring and response to detected incidents based on technologies and expertise of Kaspersky Security Operations Center (SOC) team. MDR allows detecting threats at any stage of the attack – both before anything is compromised and after the attackers have penetrated the company’s infrastructure. This is achieved through preventive security systems and active threat hunting – the essential MDR components. MDR also features automatic and manual incident response and expert recommendations.
The annual Kaspersky Managed Detection and Response analytical report sums up the analysis of incidents detected by Kaspersky SOC team. The report presents information on the most common offensive tactics and techniques, the nature and causes of incidents and gives a breakdown by country and industry.
2022 incidents statistics
Security events
In 2022, Kaspersky MDR processed over 433,000 security events. 33% of those (over 141,000 events) were processed using machine learning technologies, and 67% (over 292,000) were analyzed manually by SOC analysts.
Over 33,000 security events were linked to 12,000 real incidents. Overall, 8.13% of detected incidents were of high, 71.82% of medium, and 20.05% of low severity.
Response efficiency
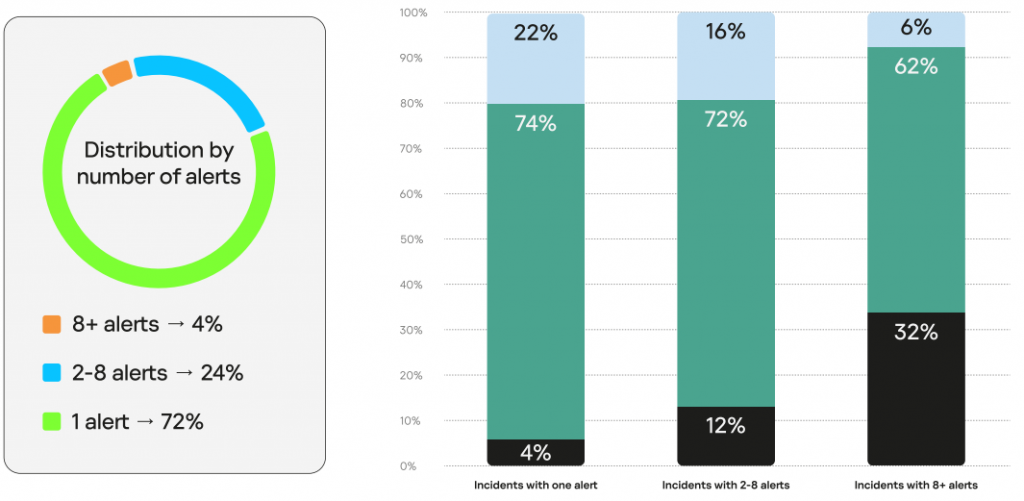
72% of 2022 incidents were detected based on a single security event, after which the attack was stopped right away. Of these, 4% were of high, 74% of medium, and 22% of low severity.
On average, in 2022, a high severity incident took the SOC team 43.8 minutes to detect. The 2022 figures for medium and low severity incidents are 30.9 and 34.2, respectively.
Geographical distribution, breakdown by industry
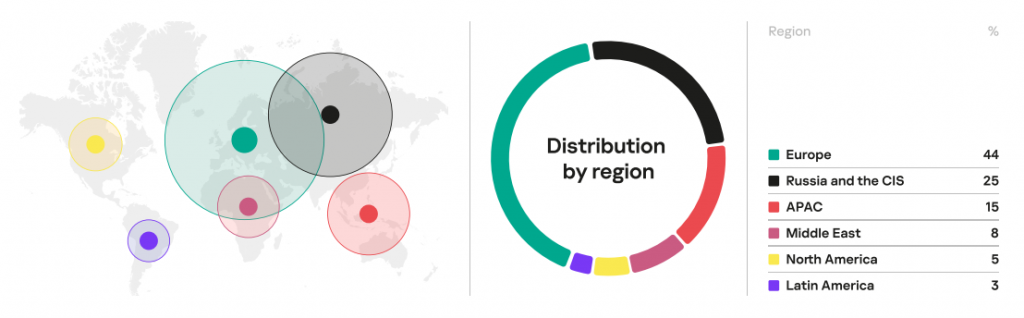
In 2022, 44% of incidents were detected in European organizations. Russia and CIS are in second place with a quarter of all detected incidents. Another 15% of incidents relate to organizations from the Asia-Pacific.
Industry-wise, industrial organizations suffered more incidents than any. Most of the critical incidents were detected in government agencies, industrial and financial organizations. It is worth noting though that a fair share of critical incidents across financial organizations was due to Red Teaming events.
Recommendations
For effective protection from cyberattacks, these are Kaspersky SOC team’s recommendations to organizations:
- Apart from the classic monitoring instruments, deploy the active threat hunting methods and tools allowing for early detection of incidents.
- Hold regular cyberdrills involving Red Teaming to train your teams to detect attacks and analyze the organization’s security.
- Practice the multilevel malware protection approach comprising various threat detection technologies – from signature analysis to machine learning.
- Use MITRE ATT&CK knowledge bases.
See the full version of the report (PDF) for more information on the incidents detected in 2022, main offensive tactics and techniques, MITRE ATT&CK classification of incidents, and detection methods. To download it, please, fill in the form below.
Reports
For more than five years, the Global Research and Analysis Team (GReAT) at Kaspersky has been publishing quarterly summaries of advanced persistent threat (APT) activity. These summaries are based on our threat intelligence research; and they provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports.
We continued to track Tomiris as a separate threat actor over three new attack campaigns between 2021 and 2023, and our telemetry allowed us to shed light on the group. In this blog post, we’re excited to share what we now know of Tomiris with the broader community, and discuss further evidence of a possible connection to Turla.
The Lazarus group is a high-profile Korean-speaking threat actor with multiple sub-campaigns. In this blog, we’ll focus on an active cluster that we dubbed DeathNote.
A DLL named guard64.dll, which was loaded into the infected 3CXDesktopApp.exe process, was used in recent deployments of a backdoor that we dubbed “Gopuram” and had been tracking internally since 2020.
Original Post URL: https://securelist.com/mdr-report-2022/109599/
Category & Tags: SOC, TI and IR posts,Industrial threats,Internal Threats Statistics,MDR,Security services,Security technology,Targeted attacks,Internal threats – SOC, TI and IR posts,Industrial threats,Internal Threats Statistics,MDR,Security services,Security technology,Targeted attacks,Internal threats
Views: 1