Source: levelblue.com – Author: hello@alienvault.com.
Knowing Your Software Supply Chain
Software complexity is increasing at unprecedented levels. The average software supply chain now contains artifacts from open-source repositories, internally developed code, software developed by third-parties, and commercial-off-the-shelf (COTS) software. All of this combines to run your business.
The questions surrounding the software supply chain range from its visibility to its trustworthiness to the origin of the bits and bytes. The 2025 LevelBlue Data Accelerator: Software Supply Chain and Cybersecurity takes an empirical look at how organizations perceive visibility, invest in, and are prepared to remediate attacks of their software supply chain.
Attackers Know Your Software Supply Chain Weaknesses
Across organizations, there are similarities in the software supply chain that attackers can easily identify and exploit. Adversaries are looking for an easy way into your organization through unpatched software, insecure and common third-party APIs, or known open-source vulnerabilities.
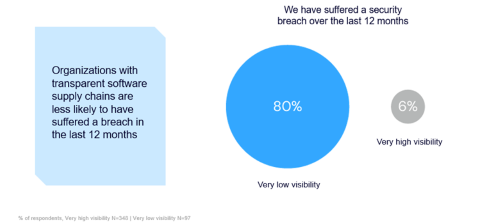
Gaining access through these known vulnerabilities allow adversaries to infiltrate your systems through the last mile; your software. A key element in thwarting these attacks on the software supply chain is greater visibility. LevelBlue’s new research finds that organizations with transparent software supply chains are less likely to suffer a breach. The data shows that 80% of organizations with low software supply chain visibility have suffered a breach over the past 12 months compared to only 6% of those with high visibility suffering a breach in the same timeframe.
Download your complimentary copy of the new LevelBlue Data Accelerator: Software Supply Chain and Cybersecurity to learn more about the need for visibility of the software supply chain.
Is Anyone Really Prepared for Software Supply Chain Attacks?
Software supply chain attacks are on the rise and will continue to be a prime entry point for adversaries.
The new LevelBlue research examined software supply chain:
- Visibility
- Investment
- Likelihood of attack
- Preparedness for remediation
- Engagement with software suppliers about security credentials
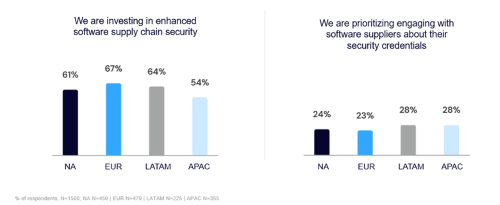
The results are surprising with:
- Low visibility
- High investment
- High likelihood of attack
- High level of confidence for remediation of attack
- Low engagement with software suppliers about their security credentials
This seeming disconnect in visibility, investment, and preparedness is consistent around the world. How is your organization preparing and planning for a software supply chain attack?
Build a Framework for Software Supply Chain Preparedness
Use the LevelBlue research to help your organization prepare for attacks against the software supply chain by following these four suggested steps.
1. Engage Executives – The C-suite is aware of the risks posed by low visibility of the software supply chain and understands it as a business imperative. Use this alignment to secure resources and accelerate transformation.
2. Map Your Supply Chain Dependencies – Conduct cross-functional risk assessments to uncover the most vulnerable areas in your supplier and development pipelines. Align your teams on short-term visibility goals and long-term risk reduction.
3. Invest in the Appropriate Technology – Implement threat detection, vulnerability management, and AI-driven exposure management and analysis.
4. Demand Transparency from Suppliers – Engage the suppliers of your software supply chain in regular security reviews. Require a software bill of material (SBOM), assess their security posture, and require continuous compliance.
Download Your Complimentary Copy of the New Research
The 2025 LevelBlue Data Accelerator Report offers region-specific data, C-suite insights, and a roadmap for improving your software supply chain visibility.
Continue to deliver business impact through cyber resilience by securing your software supply chain.
The content provided herein is for general informational purposes only and should not be construed as legal, regulatory, compliance, or cybersecurity advice. Organizations should consult their own legal, compliance, or cybersecurity professionals regarding specific obligations and risk management strategies. While LevelBlue’s Managed Threat Detection and Response solutions are designed to support threat detection and response at the endpoint level, they are not a substitute for comprehensive network monitoring, vulnerability management, or a full cybersecurity program.
Original Post url: https://levelblue.com/blogs/security-essentials/is-your-software-supply-chain-a-weak-link
Category & Tags: –
Views: 0




















































