Source: socprime.com – Author: Steven Edwards
Monitoring remote file transfer utilities like rsync is essential in detecting stealthy lateral movement or data exfiltration across Unix-based environments. But not all rsync usage is equal. In some cases, it can silently launch shell processes under the hood—making threat detection harder for defenders.
That’s where Uncoder AI’s Full Summary becomes invaluable. When used alongside VMware Carbon Black Cloud Query Language, it delivers instant, structured context for complex detection patterns—saving analysts time and preventing missed insights.
Detection Objective: Spotting Shell Spawns from Rsync
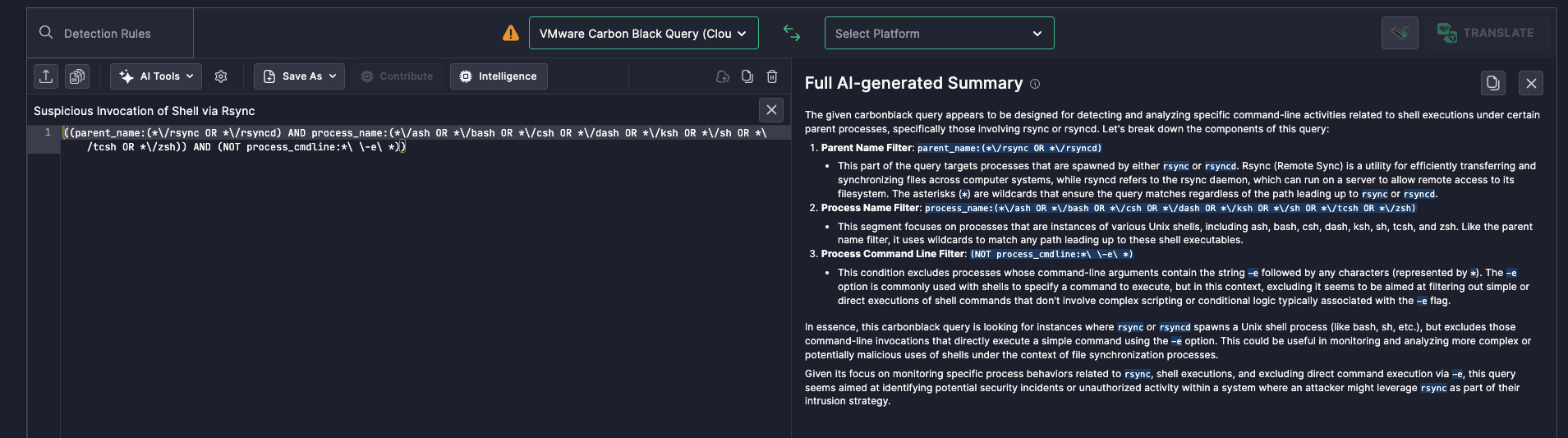
The rule focuses on identifying shell executions that originate from rsync or rsyncd processes, but specifically excludes straightforward, direct executions using the -e flag. Here’s what the logic aims to catch:
- Parent Process Match:
It filters for processes where the parent is eitherrsyncorrsyncd,indicating the shell was invoked as part of a file synchronization job. - Shell Process Spawned:
It looks for child processes that are common Unix shells likebash,dash,zsh,tcsh, etc.—suggesting the initiation of a command execution context. - Exclusion of Direct Commands:
It excludes shell invocations containing-e, which is often used in rsync to run a single remote command. This narrows the focus to non-obvious shell spawns, which may indicate a more advanced or evasive technique.
Input we used (click to show the text)
((parent_name:(*/rsync OR */rsyncd) AND process_name:(*/ash OR */bash OR */csh OR */dash OR */ksh OR */sh OR */tcsh OR */zsh)) AND (NOT process_cmdline:* -e *))
Full Summary: Fast Context for Confident Response
Without Uncoder AI, parsing this multi-condition logic would require careful line-by-line reading and interpretation. Instead, the Full Summary feature automatically laid out:
- Each logical component (parent name, process name, and command-line filters)
- The intended detection use case (complex or suspicious shell behavior)
- The threat relevance (potential lateral movement, remote command execution)
Practical Outcomes
With Full Summary, the detection was confidently deployed to monitor shell activity triggered by file sync processes. The team:
- Flagged non-standard rsync behavior in staging environments
- Avoided false positives tied to scripted -e usage
- Gained clarity on where to pivot next in their investigation chain
From Ambiguity to Action
Uncoder AI turns Carbon Black queries into structured, security-contextual insights. Instead of reverse engineering detection logic mid-incident, teams can focus on decision-making, response, and tuning—without sacrificing depth.
For any SOC hunting advanced Unix activity, this combination is a powerful asset.
Original Post URL: https://socprime.com/blog/investigating-suspicious-rsync-shell-activity-with-uncoder-ai-and-carbon-black-query-language/
Category & Tags: Blog,SOC Prime Platform,Full Summary,Uncoder AI,VMware Carbon Black – Blog,SOC Prime Platform,Full Summary,Uncoder AI,VMware Carbon Black
Views: 4



















































