Source: socprime.com – Author: John Stevens

One interesting feature of the specification of the URL schema parsing is that literal IP addresses can be accepted as decimal numbers.
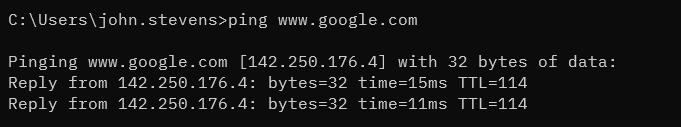
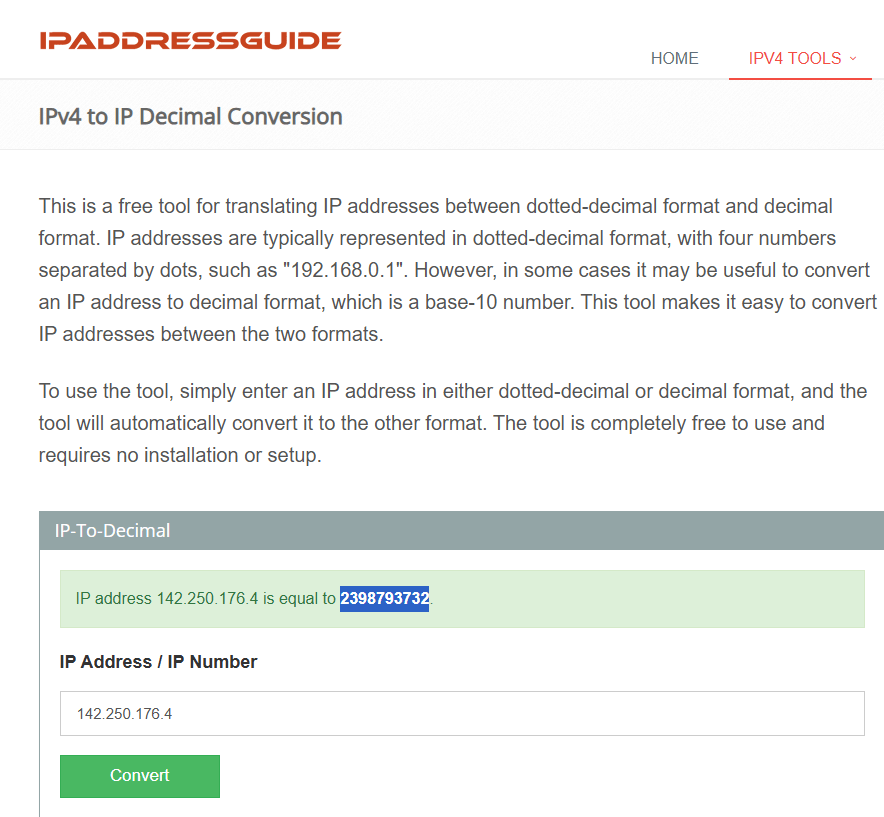
- taking a known public IP - converting that address to decimal. (a calculator I found that works can be found here https://www.ipaddressguide.com/ip) - pasting the number in your browser's address bar after `http:`I was able to find this decimal number by pinging google and using the IP address in the linked calculator site.
Another interesting feature of the schema and the other half of the technique behind the structure of the phishing links that I will demonstrate at the end of this post is that the @ symbols parse with everything to the left of them as user names used for basic auth which may just be ignored if it’s not implemented at the web site the user is eventually brought to. For example a link like this http://definitely_not_google_dot_com@2398793732 will still take you to the google search landing page.
Where you can really make some convincing phish links with what we know so far is in applications that interpret unicode. For the example we’ll look at in this post, we’ll make use of the math symbol for division ∕ you can get a copy of it in your clip board and read about it’s purpose on this unicode wiki https://codepoints.net/U+2215
Using these division slashes, we can make links that look convincing like this:
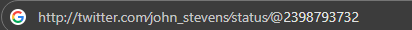
which actually looks like a link to a twitter post but it will actually take the victim to the google search page interpreting twitter.com∕john_stevens∕status∕ as a long user name.
Was this article helpful?
Like and share it with your peers.
Related Posts
Original Post URL: https://socprime.com/blog/interesting-url-schema-abuse-patterns-merry-phishmas/
Category & Tags: Blog,Knowledge Bits,Phishing – Blog,Knowledge Bits,Phishing
Views: 2





















































