Source: socprime.com – Author: Steven Edwards
How It Works
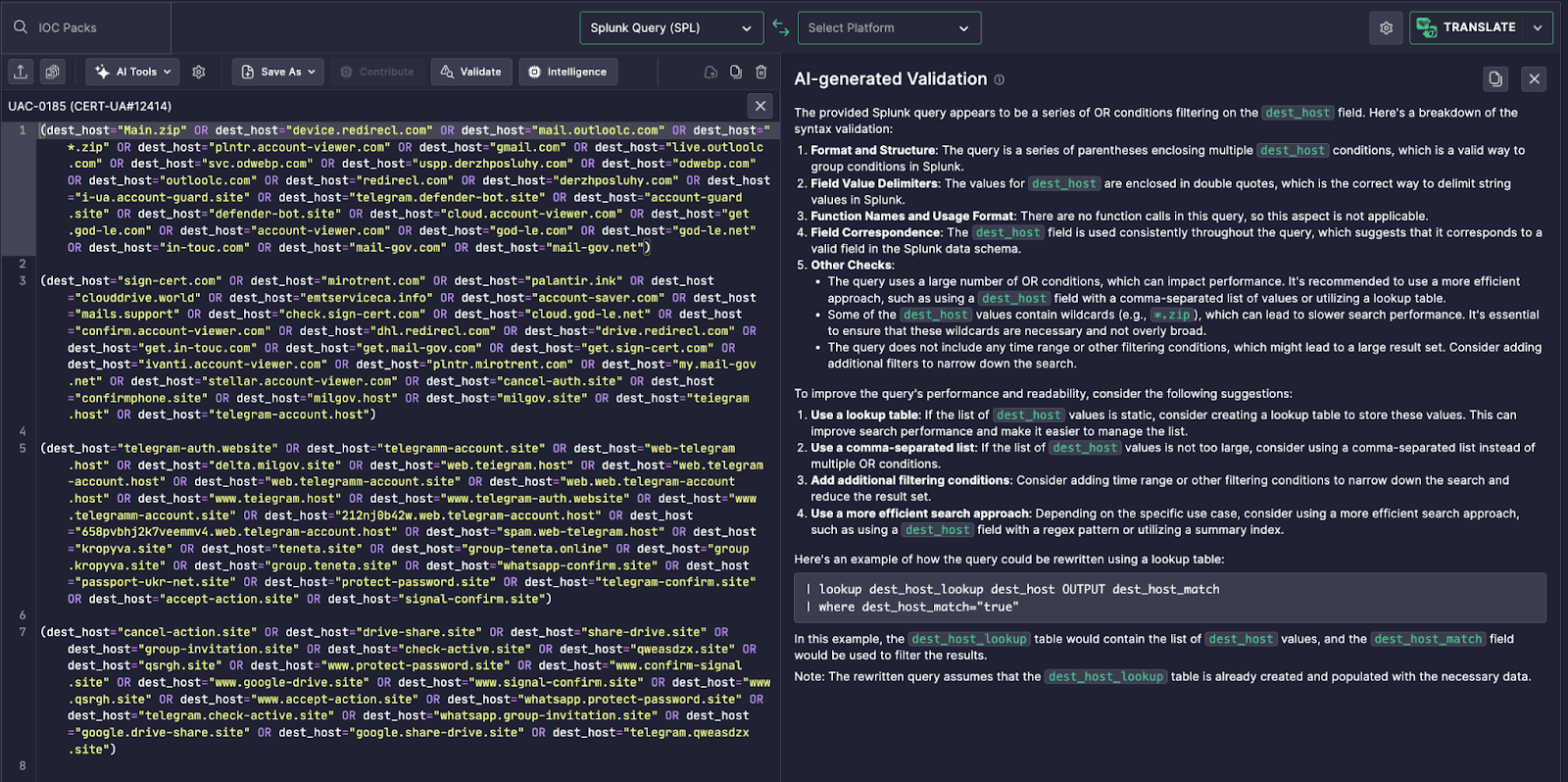
This feature in Uncoder AI ingests structured IOCs from threat reports — in this case, dozens of malicious domains tied to credential phishing (e.g., fake Google, Microsoft, and Telegram login portals). The tool processes and structures the data to automatically output a Splunk-compatible detection query.
Domain-Based Filtering with dest_host
The output query uses a sequence of OR conditions against the dest_host field:
( dest_host = "Main.zip" OR dest_host = "device.redirecl.com" OR dest_host = "mail.outoloc.com" …)
Each value corresponds to a known attacker-controlled domain extracted from the CERT-UA#1241 investigation.
The query is syntactically correct for Splunk SPL and ready for deployment to:
- Hunt for suspicious outbound traffic
- Match historical logs for evidence of compromise
- Detect attempted connections to phishing infrastructure
Why It’s Innovative
The key innovation lies in the automatic structuring of large-scale IOC lists into production-ready query syntax. Traditional detection engineering workflows require manual:
- Extraction of domain IOCs from reports
- Syntax formatting for Splunk queries
- Deduplication and wildcard management
Uncoder AI removes all of that by:
- Using NLP to extract only resolvable and valid FQDNs
- Mapping them directly to detection logic (e.g.,
dest_host) - Outputting a query optimized for field compatibility in Splunk
In the provided screenshot, over 50 hostnames — including complex ones like telegram-account.site or cloudviewer.world — are parsed and integrated instantly.
Operational Value/Results
Security analysts benefit from:
- Speed: A query covering dozens of phishing domains is generated in seconds
- Accuracy: Only malicious domains are included; no formatting errors
- Reusability: The query can be adapted, scheduled, or integrated into detection pipelines
SOC teams can directly run the output against web proxy, DNS, or firewall logs to uncover previously unseen beaconing attempts or user clicks on spoofed portals.
Original Post URL: https://socprime.com/blog/instant-domain-matching-logic-for-splunk-via-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,SPL,Splunk,Uncoder AI – Blog,SOC Prime Platform,SPL,Splunk,Uncoder AI
Views: 4




















































