Source: www.infosecurity-magazine.com – Author:
The DoNot APT group has recently conducted a multi-stage cyber espionage campaign targeting the Italian Ministry of Foreign Affairs, according to Trellix.
The group, attributed by several cyber threat intelligence companies to India, impersonated European defense officials, mentioning their visit to Bangladesh, and lured their targets to click on a malicious Google Drive link.
“While historically focused on South Asia, this incident targeting South Asian embassies in Europe indicates a clear expansion of their interests towards European diplomatic communications and intelligence,” said the Tellix researchers in a July 8 report.
Background on DoNot APT
DoNot APT, also known as APT-C-35, Mint Tempest, Origami Elephant, SECTOR02 and Viceroy Tiger, has been active since at least 2016.
The group traditionally focuses on cyber espionage campaigns with South Asian geopolitical interests. Its operations are marked by persistent surveillance, data exfiltration and long-term access.
The group is known for using custom-built Windows malware, including backdoors such as YTY and GEdit, which are often delivered through spear-phishing emails or malicious documents.
Multi-Stage Espionage Campaign Targets Italian Defense Officials
The latest DoNot APT attack identified by Trellix began with a spear-phishing email originating from a Gmail address, int.dte.afd.1@gmail[.]com, which impersonated official diplomatic correspondence. The target was an Italian government entity operating within the diplomatic sector.
The email leveraged diplomatic themes related to defense attaché coordination between Italy and Bangladesh.
Although the exact body content was not gathered in the findings, the subject line “Italian Defence Attaché Visit to Dhaka, Bangladesh” suggests a lure designed to appear as legitimate diplomatic correspondence, which would reasonably contain document attachments or links.
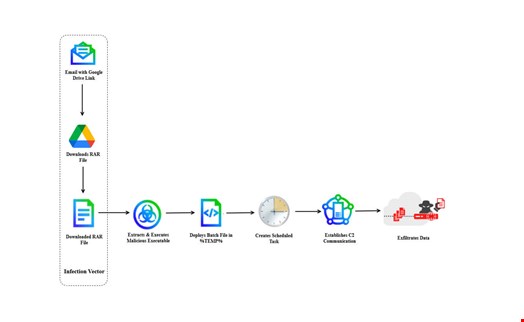
The email contained a Google Drive link that directed the recipient to a malicious RAR archive named SyClrLtr.rar.
Upon execution, the archive deployed notflog.exe, which then triggered a batch file (djkggosj.bat) in the system’s %TEMP% directory.
To maintain persistence, the malware established a scheduled task named “PerformTaskMaintain”, configured to run every 10 minutes. This ensured continuous communication with the attackers’ command-and-control (C2) server, allowing for sustained access to the compromised network.
The ultimate goal of the attack was to establish a foothold within the target’s infrastructure and exfiltrate sensitive information.
Analysis of the payload revealed its association with LoptikMod malware, a tool reportedly used exclusively by the DoNot APT group since 2018.
This multi-stage infection chain demonstrated a sophisticated approach to evading detection while maintaining long-term access to the victim’s systems.
The use of legitimate services, such as Google Drive, and carefully crafted spear-phishing tactics underscored the attackers’ efforts to appear credible and bypass initial security defenses.
“The recent targeting of a European foreign affairs ministry highlights DoNot APT’s expanding scope and persistent interest in gathering sensitive information, underscoring the need for heightened vigilance and robust cybersecurity measures,” the Trellix report concluded.
Original Post URL: https://www.infosecurity-magazine.com/news/indian-cyber-espionage-italian/
Category & Tags: –
Views: 0




















































