Source: socprime.com – Author: Steven Edwards
When new CVEs drop, defenders race to understand how attackers might exploit them. One such vulnerability—CVE-2024-35250—involves suspicious usage of the ksproxy.ax module. Palo Alto Cortex XSIAM is among the platforms providing early detection logic for potential abuse. But parsing the query manually? Not quick.
That’s where Uncoder AI’s Short Summary becomes indispensable. This feature reads the detection rule and instantly provides a plain-language explanation, helping security teams get clarity without reverse-engineering complex conditions.
Real-World Use Case: ksproxy.ax Exploitation
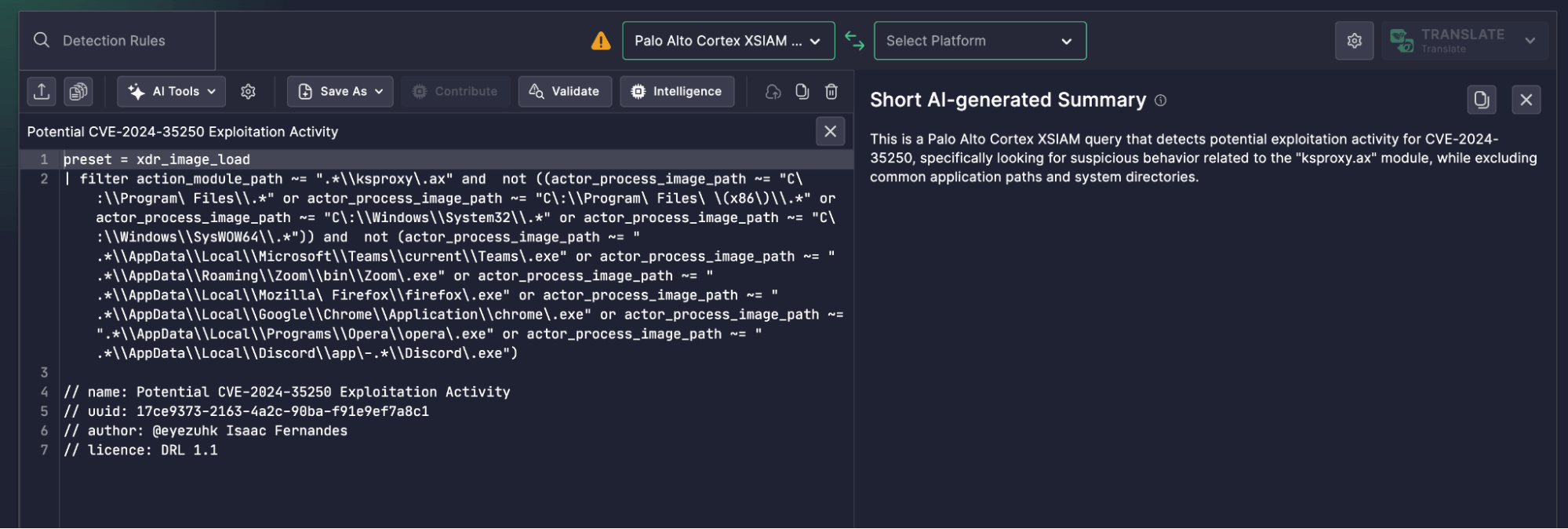
The provided Cortex XQL query aims to flag image loads involving ksproxy.ax—a DirectShow-related module—when invoked by non-standard processes. It’s a solid detection strategy for post-exploitation scenarios, particularly when attackers hijack legitimate multimedia components to evade detection.
The logic also carefully excludes known safe paths, such as:
C:WindowsSystem32C:Program FilesAppDatapaths associated with common apps: Chrome, Zoom, Firefox, Opera, Teams, Discord
This exclusion helps reduce false positives by ensuring that known legitimate binaries using ksproxy.ax are filtered out.
Input we used (click to show the text)
preset = xdr_image_load
| filter action_module_path ~= “.*\ksproxy.ax” and not ((actor_process_image_path ~= “C:\Program Files\.*” or actor_process_image_path ~= “C:\Program Files (x86)\.*” or actor_process_image_path ~= “C:\Windows\System32\.*” or actor_process_image_path ~= “C:\Windows\SysWOW64\.*”)) and not (actor_process_image_path ~= “.*\AppData\Local\Microsoft\Teams\current\Teams.exe” or actor_process_image_path ~= “.*\AppData\Roaming\Zoom\bin\Zoom.exe” or actor_process_image_path ~= “.*\AppData\Local\Mozilla Firefox\firefox.exe” or actor_process_image_path ~= “.*\AppData\Local\Google\Chrome\Application\chrome.exe” or actor_process_image_path ~= “.*\AppData\Local\Programs\Opera\opera.exe” or actor_process_image_path ~= “.*\AppData\Local\Discord\app-.*\Discord.exe”)
// name: Potential CVE-2024-35250 Exploitation Activity
// uuid: 17ce9373-2163-4a2c-90ba-f91e9ef7a8c1
// author: @eyezuhk Isaac Fernandes
// licence: DRL 1.1
AI Output (click to show the text)
This is a Palo Alto Cortex XSIAM query that detects potential exploitation activity for CVE-2024-35250, specifically looking for suspicious behavior related to the "ksproxy.ax" module, while excluding common application paths and system directories.
Operational Impact
With vulnerabilities like CVE-2024-35250, defenders don’t have the luxury of time. Rapid triage and hunting depend on understanding detection logic immediately. Uncoder AI’s Short Summary:
- Boosts onboarding of new team members
- Supports faster detection validation
- Improves retro-hunting with clearer rule context
- Bridges detection engineering with Tier 1–2 analyst workflows
By transforming verbose queries into actionable summaries, Uncoder AI becomes an essential lens through which defenders interpret machine logic.
Original Post URL: https://socprime.com/blog/how-uncoder-ai-clarifies-cve-2024-35250-detection-in-cortex-xsiam/
Category & Tags: Blog,SOC Prime Platform,CVE-2024-35250,Short Summary,Uncoder AI – Blog,SOC Prime Platform,CVE-2024-35250,Short Summary,Uncoder AI
Views: 10




















































