Rate this post
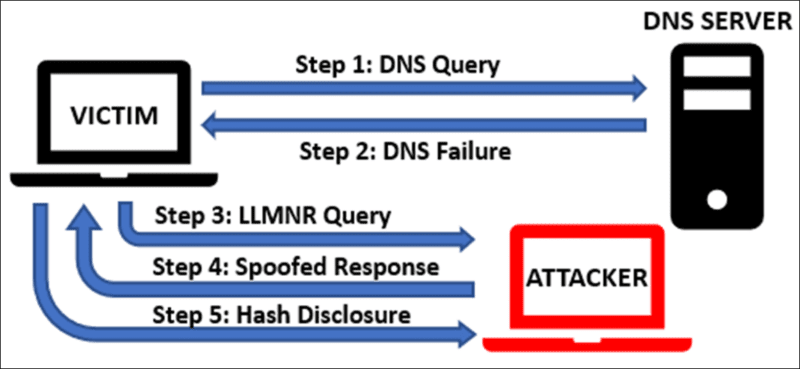
Most of us already know the basic principle of authentication, which, in its simplest form, helps us to identify and verify a user, process, or account. In an Active Directory environment, this is commonly done through the use of an NTLM hash. When a user wants to access a network resource, such as a file […]… Read More
The post How to Prevent High Risk Authentication Coercion Vulnerabilities appeared first on The State of Security.
The post How to Prevent High Risk Authentication Coercion Vulnerabilities appeared first on Security Boulevard.
Leer másSecurity Boulevard
Views: 0