Source: thehackernews.com – Author: .
Feb 15, 2024The Hacker NewsSaaS Security / Risk Management
With many of the highly publicized 2023 cyber attacks revolving around one or more SaaS applications, SaaS has become a cause for genuine concern in many boardroom discussions. More so than ever, considering that GenAI applications are, in fact, SaaS applications.
Wing Security (Wing), a SaaS security company, conducted an analysis of 493 SaaS-using companies in Q4 of 2023. Their study reveals how companies use SaaS today, and the wide variety of threats that result from that usage. This unique analysis provides rare and important insights into the breadth and depth of SaaS-related risks, but also provides practical tips to mitigate them and ensure SaaS can be widely used without compromising security posture.
The TL;DR Version Of SaaS Security
2023 brought some now infamous examples of malicious players leveraging or directly targeting SaaS, including the North Korean group UNC4899, 0ktapus ransomware group, and Russian Midnight Blizzard APT, which targeted well-known organizations such as JumpCloud, MGM Resorts, and Microsoft (respectively), and probably many others that often go unannounced.
The first insight from this research cements the concept that SaaS is the new supply chain, providing an almost intuitive framework to the importance of securing SaaS usage. These applications are clearly an integral part of the modern organization’s set of tools and vendors. That said, long gone are the days when every 3rd party with access to company data had to go through security or IT approval. Even in the most rigorous companies, when a diligent employee needs a quick and efficient solution, they’ll look it up and use it to get their jobs’ done faster and better. Again, think of the widespread use of GenAI, and the picture is clear.
As such, any organization concerned about the security of its supply chain must adopt SaaS security measures. According to the MITRE ATT&CK technique ‘Trusted Relationships’ (T1199), a supply chain attack occurs when an attacker targets a vendor to exploit it as a means to infiltrate a broader network of companies. By entrusting sensitive data to external SaaS vendors, organizations subject themselves to supply chain risks that reach beyond immediate security concerns.
Four Common SaaS Risks
There are various reasons and ways in which SaaS is being targeted. The good news is that most of the risks can be significantly mitigated when monitored and controlled. Basic SaaS security capabilities are even free, suited for organizations that are just beginning to develop their SaaS security posture or need to compare it to their current solution.
1) Shadow SaaS
The first problem with SaaS usage is the fact that it often goes completely unnoticed: The number of applications used by organizations is typically 250% larger than what a basic and often-used query of the workspace reveals.
Amongst the companies analyzed:
- 41% of applications were used by only one individual, resulting in a very long tail of unsanctioned applications.
- 1 out of 5 users were utilizing applications not used by anyone else within their organization, creating security and resource strains.
- 63% of single-user applications were not even accessed within a 3-month period, begging the question – why keep them connected to company data?
- 96.7% of organizations used at least one application that had a security incident in the previous year, solidifying the continuous risk and need for proper mitigation.
2) MFA Bypassing
Wing’s research indicates a trend where users opt to use a username/password to access the services they need, bypassing the security measures in place (see image 1).
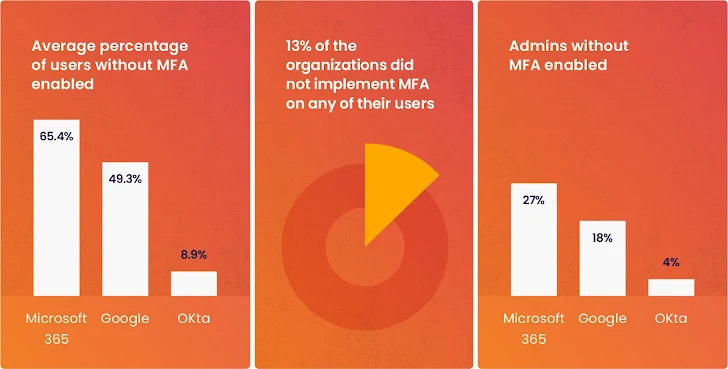 |
| Image 1: From Wing Security’s research, bypassing MFA. |
3) Forgotten tokens
Users grant the applications they need tokens; this is necessary for the SaaS applications to serve their purpose. The problem is that these tokens are often forgotten about after a few or just one use. Wing’s research revealed a large presence of unused tokens over a period of 3 months, creating an unnecessarily large attack surface for many customers (Image 2).
4) The new risk of Shadow AI
In the beginning of 2023, security teams primarily concentrated on a select few renowned services offering access to AI-based models. However, as the year progressed, thousands of conventional SaaS applications adopted AI models. The research shows that 99.7% of companies were using applications with integrated AI capabilities.
Organizations were required to agree to updated terms and conditions permitting these applications to utilize and refine their models using the organizations’ most confidential data. Often, these revised terms and conditions slipped under the radar, along with the usage of AI itself.
There are different ways in which AI applications may use your data for their training models. This can come in the form of learning your data, storing your data and even having a human manually go over your data to improve the AI model. According to Wing, this capability is often configurable and totally avoidable, provided it is not overlooked.
Solving SaaS Security Challenges In 2024
The report ends on a positive note, listing 8 ways in which companies can mitigate the growing threat of the SaaS supply chain. Including:
- Ongoing shadow IT discovery and management.
- Prioritize the remediation of SaaS misconfigurations
- Optimize anomaly detection with predefined frameworks, automate when possible.
- Discover and monitor all AI-using SaaS applications, and constantly monitor your SaaS for updates in their T&C pertaining to AI usage.
For the full list of findings, tips on ensuring safe SaaS usage and a 2024 SaaS security forecast, download the full report here.
Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Twitter and LinkedIn to read more exclusive content we post.
Original Post url: https://thehackernews.com/2024/02/how-nation-state-actors-target-your.html
Category & Tags: –
Views: 2





















































