Source: socprime.com – Author: Steven Edwards
How It Works
The “Hot OSINT Indicators” tab within Uncoder AI extends the built-in Threat Detection Marketplace search with continuously updated TLP:CLEAR threat intelligence. This data is sourced from publicly disclosed CERT-UA reports and is presented in a structured, query-ready format for immediate operational use. The interface allows users to filter through IOCs categorized by threat campaigns or malware types, and incorporate them directly into custom detection workflows.
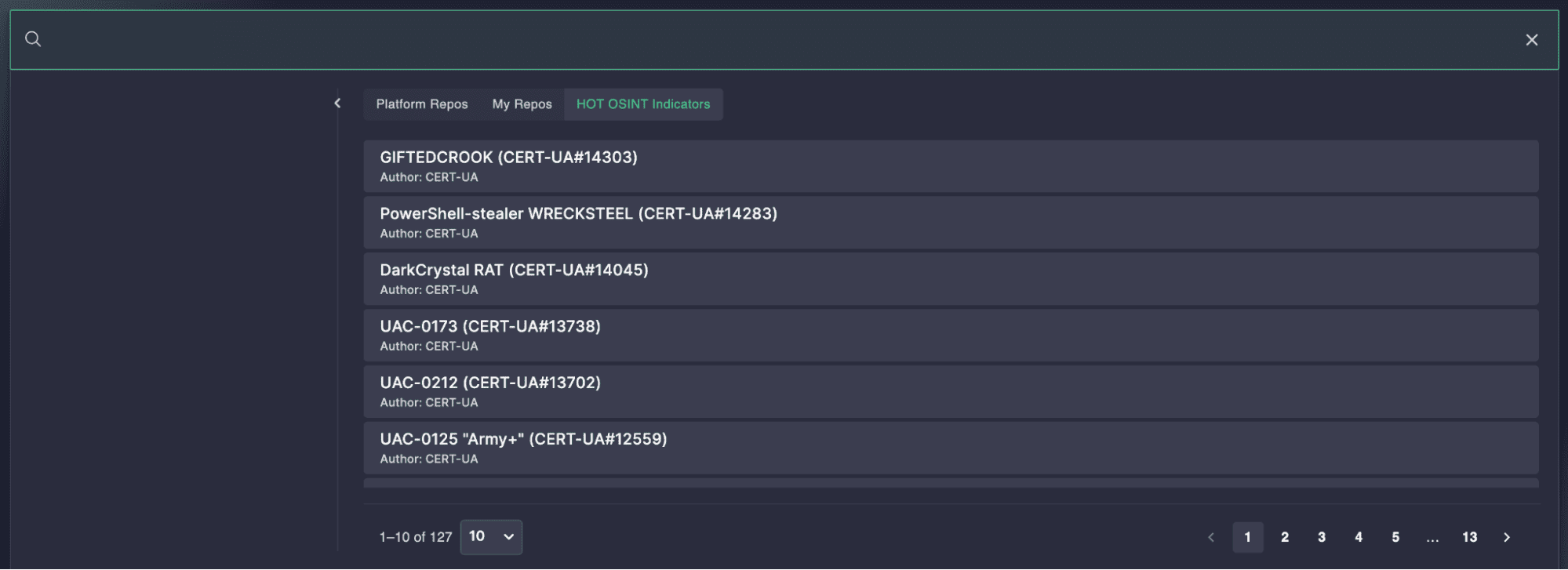
Why It’s Innovative
Uncoder AI bridges the gap between threat intelligence and operational detection by embedding OSINT-based indicators directly into the detection engineering workflow. This eliminates the need to hunt for reliable IOCs separately. Unlike traditional threat intel feeds, the Hot OSINT Indicators feature integrates directly with Threat Detection Marketplace and supports real-time usage inside the Uncoder AI interface — no exports, plugins, or sync jobs required.
Operational Value
Security teams can instantly generate or enhance detection logic using real-world indicators with zero manual enrichment. This reduces response time, improves coverage of active threats, and simplifies threat modeling based on current adversary activity. The seamless integration of CERT-UA IOCs also helps align detection logic with region-specific threat intelligence, boosting operational relevance.
Get immediate access to actionable, public threat intelligence — directly within your detection workflow.
Original Post URL: https://socprime.com/blog/hot-osint-indicators/
Category & Tags: Blog,SOC Prime Platform,IOC,OSINT – Blog,SOC Prime Platform,IOC,OSINT
Views: 4




















































