Source: www.hackerone.com – Author: Pieter Ockers.
Triage and validation are at the heart of any bug bounty or Vulnerability Disclosure Program (VDP). Despite their central role, not all triage teams and workflows are created equal.
Like triaging in a hospital emergency room, security issues must be diagnosed and handled by an expert as soon as they arrive. But it doesn’t stop there. Just as an ER needs good doctors, a triage team needs experienced security analysts to conduct a deep analysis and ask:
- What is the potential impact of an incident?
- Is this something that needs immediate escalation?
- Do we have enough information to continue?
- How can we de-duplicate and validate the submitted vulnerability?
- Which is the right group to assign this issue?
- What is the right remediation advice to fix the issue effectively?
At HackerOne, we realize that delivering the most effective triage experience for customers and hackers is a meticulous job and requires a team of experts who should function as an extension of your security or development team. That’s where HackerOne Security Analysts come in.
Meet the Extension of Your Security Team
HackerOne’s Triage Services consists of over 45 highly skilled in-house security analysts who triage over 4,000 reports per week and 16,000 reports per month across five different continents. Our global coverage enables the triage team to deliver quicker results and faster resolution at scale.
HackerOne’s Security Analysts have a broad range of technical skills and industry experience to cover a diverse range of assets, including web, mobile, API, binary, firmware, IoT, and hardware. All team members have a finger on the pulse of high-volume reports, zero-days, and other vulnerabilities. Our team understands security concepts inside and out. They know how ethical hackers think and behave based on their own experience.
About the team:
- Hundreds of years of combined experience in AppSec, hacking, and triaging.
- A geographically diverse structure, covering Pacific to Eastern time zones in the Western Hemisphere and British Standard Time to India Standard Time in the Eastern Hemisphere, allowing the team to correspond with hackers in over ten languages.
- In-depth knowledge with prior industry experience at global organizations such as Adobe, DoD, Dell, RSA, Microsoft, HP, GoDaddy, and more.
- Average time to first response of 11 hours.
Triage Is Just the First Step
HackerOne’s Security Analysts go far beyond triaging for our customers. The detail and quality of the validated vulnerability triage reports empower our customers to better manage the remediation process and respond to incidents. With this advantage, your team can fix verified vulnerabilities, reduce the time from report submission to code repair, and minimize the risk of attack with greater efficiency.
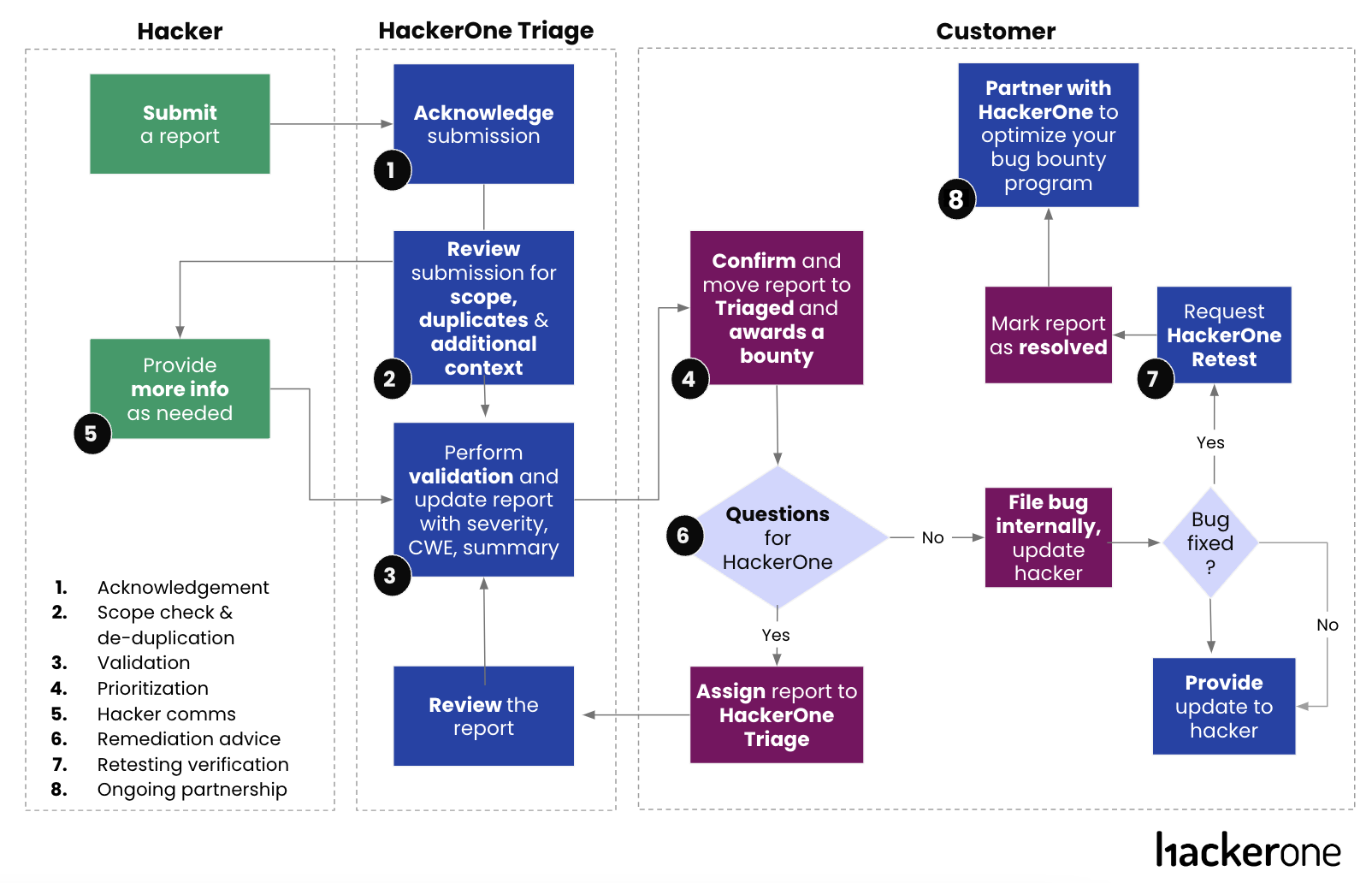
Here is a recap of HackerOne’s Triage Lifecycle to shed light on the process:
- Acknowledgment: First response by HackerOne security analysts.
- Scope Check and De-duplication: Removal of false positives, deduplication and scope check.
- Validation: Verification of valid vulnerabilities using a consistent methodology that includes a reproduction of the report, severity calculation, metadata enrichment and a detailed summary of the finding, the impact, and expert analysis.
- Hacker Communications: Maintain ongoing engagement and communication with hackers.
- Remediation Advice: Actionable guidance to effectively address risk and help customers close the risk gap.
Retesting Verification: Test implemented fixes in collaboration with hackers. HackerOne Retest becomes available for customers who want to ensure fixes have been made and are secure.
Get Started With HackerOne
HackerOne Triage Services are among the key components of the HackerOne Platform help your organization protect an ever-expanding attack surface. Contact us to learn more about achieving attack resistance by engaging with HackerOne’s expert security analysts. Get started with world-class triage today.
Original Post url: https://www.hackerone.com/hackerones-depth-approach-vulnerability-triage-and-validation
Category & Tags: –
Views: 0




















































