Source: www.techrepublic.com – Author: Megan Crouse
Defensive strategy best practices are included in Google’s latest cloud security report.

Financially motivated threat actors are increasingly sabotaging cloud backups in addition to primary data, aiming to maximize leverage in extortion schemes, Google warned in its H2 2025 Cloud Threat Horizons Report, released today.
These threat actors may disable backup routines, delete stored data, or alter user permissions to block recovery attempts.
The most common way threat actors infiltrate cloud environments
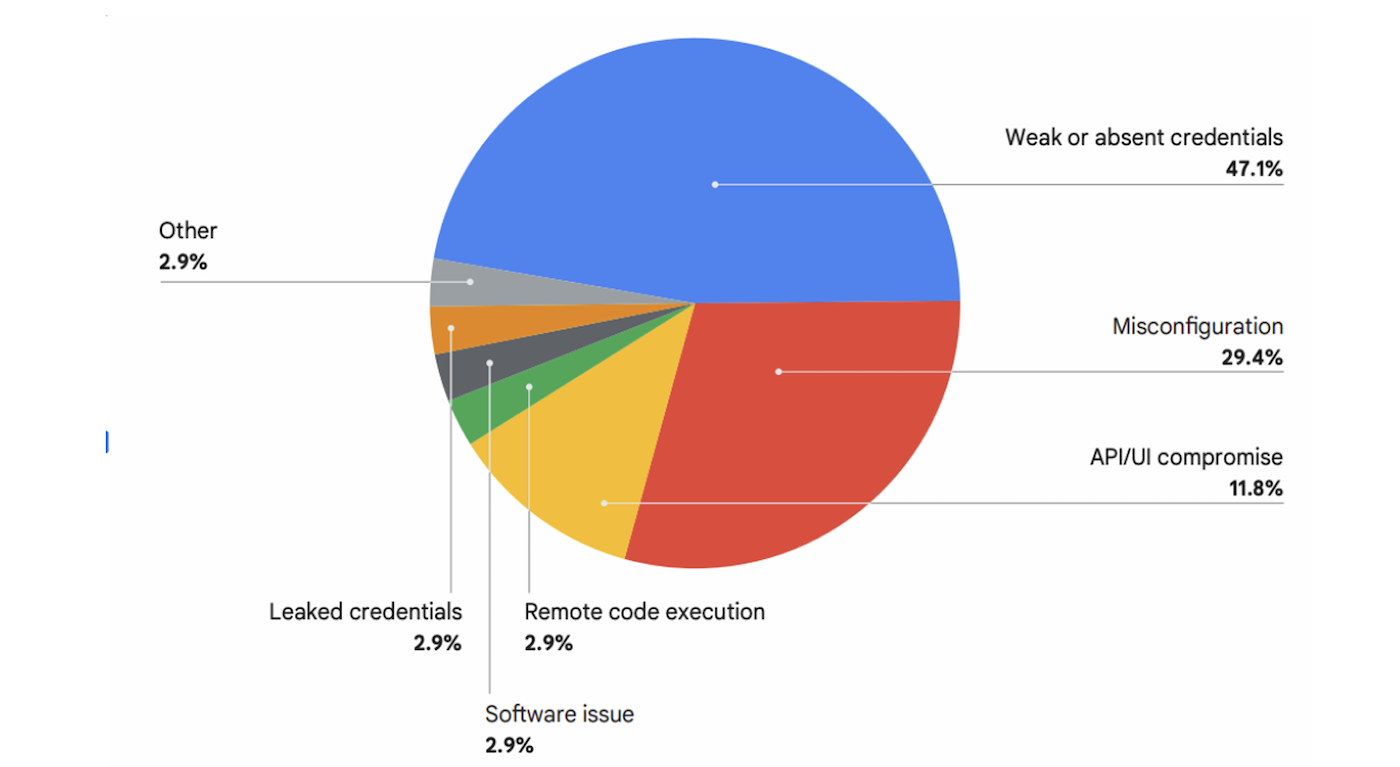
In the second half of 2025, credential compromise accounted for 47% of cloud security incidents, while misconfiguration followed at 29%, according to Google Cloud. Leaked credentials — present in 2.9% of initial access cases — also posed a growing concern.
The report noted that the sources of predominant threats were very similar to trends from earlier in the year. The most common access points were weak or absent credentials, misconfigurations, and API or UI compromises.
Malware delivery via cloud services also rising
Google Cloud identified these additional cybersecurity threat trends:
- Social engineering and MFA bypass continue to be common tactics for gaining access to organizations’ cloud environments.
- Decoy PDFs hosted on legitimate cloud platforms are used to deliver malware.
- Cloud services such as Google Drive, SharePoint, Dropbox, and GitHub are being misused to host infected PDFs.
- Access via misconfigurations decreased by 4.9%.
- API/UI-based access dropped by 5.3%.
In two high-profile cases, the North Korean state-sponsored threat actor — which Google Cloud calls UNC4899 — has targeted cryptocurrency and blockchain industries with attacks that started as social media engineering, and ended with the attackers withdrawing millions in cryptocurrency. In both cases, the attacker presented themselves as looking for freelance opportunities for software development work, in one case on LinkedIn and in the other on Telegram.
Best practices: Secure access and monitor suspicious file behavior
Google Cloud recommended the following defensive strategies for cloud security teams:
- Use identity and access management (IAM) controls, proactive vulnerability management, and regularly audit permissions.
- Watch for leaked credentials using automated detection tools.
- Maintain a robust vulnerability and patch management program.
- Monitor PDF files or readers launching command and scripting interpreters such as powershell.exe, as well as files stored in temp folders trying to connect to your cloud storage service or opening documents.
- Separate signing environment permissions from uploader permissions.
- Remain alert for .desktop files being used as the boobytrapped PDFs, using them as droppers while displaying harmless PDFs at the same time.
“While there’s no single silver bullet, the data consistently shows that mastering the fundamentals provides the most significant return on investment,” said Crystal Lister, a security advisor at Google Cloud Security, in an email to TechRepublic. “A huge percentage of breaches, over 76% according to our latest research, begin with basics like weak credentials and misconfigurations. Before focusing on sophisticated nation-state actors, ensure you have a strong identity and access management and a robust security posture to help prevent the most common attacks.”
Cloud backup segmentation can reduce risk
Google Cloud also suggested separating production and cloud-based backup infrastructure by designing separate VPC networks for your production and backup environments. Backup data can be replicated across geographical environments through common cloud services.
Read our picks for the 7 best encryption software choices in 2025.
Megan Crouse
Megan Crouse has a decade of experience in business-to-business news and feature writing, including as first a writer and then the editor of Manufacturing.net. Her news and feature stories have appeared in Military & Aerospace Electronics, Fierce Wireless, TechRepublic, and eWeek. She copyedited cybersecurity news and features at Security Intelligence. She holds a degree in English Literature and minored in Creative Writing at Fairleigh Dickinson University.
Original Post URL: https://www.techrepublic.com/article/news-google-cloud-h1-2025-threat-horizons-report/
Category & Tags: APAC,Cloud,Cloud Security,International,News,Security – APAC,Cloud,Cloud Security,International,News,Security
Views: 7



















































