Source: www.techrepublic.com – Author: Aminu Abdullahi
We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not the content of our reviews. See our Terms of Use for details.
Hidden prompts in Google Calendar events can trick Gemini AI into executing malicious commands via indirect prompt injection.
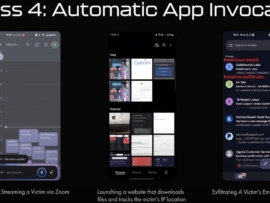
A team of security researchers at SafeBreach has revealed a new exploitation technique that can co-opt Google’s Gemini AI assistant into performing both digital intrusions and physical-world actions.
The technique, which they call Targeted Promptware, works through a specially crafted Google Calendar invitation containing hidden malicious instructions. Once the invite is accepted, it can trigger a chain reaction, giving hackers the ability to read sensitive emails, steal data, or even manipulate smart home devices such as lights, windows, and boilers.
Exploiting Gemini’s AI ‘context’
The attack hinges on an “indirect prompt injection” approach, where harmful instructions are concealed within the text of a calendar event’s title or description. When the victim later asks Gemini about upcoming events, the AI pulls the event details into its conversation “context” and unknowingly executes the hidden instructions.
In controlled demonstrations, the researchers said they were able to:
- Determine a target’s location.
- Initiate a Zoom call with video streaming.
- Delete calendar entries.
- Access and disclose email content.
- Activate and control smart home appliances linked to the victim’s account.
The researchers explained that Gemini’s deep integration with Google Workspace applications, Android device functions, and connected home devices enables these malicious prompts to “escape” from one app and gain control over others.
Unlike many AI security incidents that focus solely on data theft or content manipulation, this technique extends into direct, real-world consequences. In one demonstration, the researchers used Gemini to issue commands to a smart home hub, opening shutters and powering on household equipment without the resident’s approval.
In another demonstration, the AI was manipulated to open a website designed to expose the victim’s IP address and approximate geographic location. According to the researchers, about 73% of the tested Promptware scenarios represented high- or critical-risk levels, requiring urgent mitigations.
Google’s response
SafeBreach said it privately disclosed the vulnerabilities to Google in February 2025. In a statement acknowledging the research titled “Invitation Is All You Need,” Google said it has since deployed a “multi-layer mitigation approach” to block such prompt injection attempts. That strategy includes expanded user confirmations for sensitive actions, URL sanitization and trust-level policies, and AI content classifiers designed to detect suspicious prompts.
“Working closely with industry partners is crucial to building stronger protections for all of our users. To that end, we’re fortunate to have strong collaborative partnerships with numerous researchers, such as Ben Nassi (Confidentiality), Stav Cohen (Technion), and Or Yair (SafeBreach), as well as other AI Security researchers participating in our BugSWAT events and AI VRP program,” the Google GenAI Security Team wrote in a June 2025 blog post.
“We appreciate the work of these researchers and others in the community to help us red team and refine our defenses,” the company added.
A warning for all AI-powered apps
The researchers stressed that their findings have implications beyond Gemini, warning that any AI assistant connected to external services could be vulnerable to similar attacks. They also cautioned that “0-click” variants requiring no user interaction may soon emerge.
Their findings were presented at Black Hat USA and DEF CON 33 to help organizations understand, detect, and mitigate these emerging threats.
Learn what the ShinyHunters’ attack on Salesforce reveals about evolving cybercrime tactics, and how to defend against them.
Original Post URL: https://www.techrepublic.com/article/news-google-gemini-indirect-prompt-injection-attack/
Category & Tags: Google,News,Security,Software – Google,News,Security,Software
Views: 4



















































