Source: socprime.com – Author: Steven Edwards
One of the more advanced tactics in attacker playbooks is tampering with event log configurations to erase traces of compromise. Detecting such attempts via Windows Registry modifications is complex—often involving detailed Splunk queries that filter by registry keys and permissions.
To quickly make sense of these queries, analysts are turning to Uncoder AI’s AI-generated Decision Tree feature. It doesn’t just summarize queries—it visually maps them into logical branches, helping security teams understand intent, scope, and execution paths in seconds.
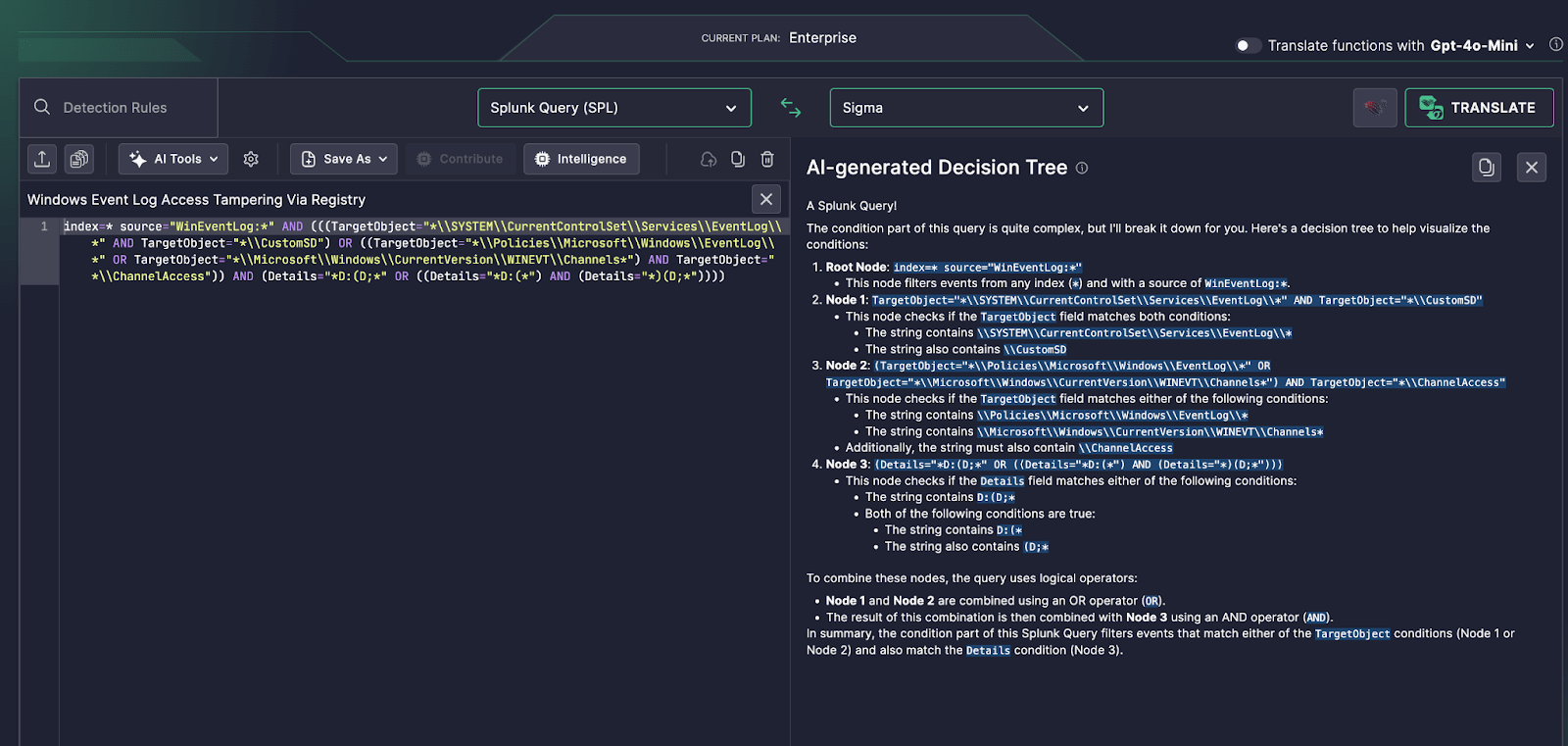
Use Case: Detecting Registry-Based Event Log Manipulation
In this example, a Splunk SPL query tracks changes to registry paths related to:
SYSTEMCurrentControlSetServicesEventLogPoliciesMicrosoftWindowsEventLogMicrosoftWindowsCurrentVersionWINEVTChannels
These keys are often targeted to disable or reroute log retention, particularly via permission edits to CustomSD or ChannelAccess.
The rule also checks for Security Descriptor Definition Language (SDDL) patterns in the Details field—like D:(…—which signify direct permission modifications, a red flag in log tampering scenarios.
Was this article helpful?
Like and share it with your peers.
Original Post URL: https://socprime.com/blog/exposing-event-log-tampering-with-uncoder-ais-ai-decision-tree-for-splunk-queries/
Category & Tags: Blog,SOC Prime Platform,AI Decision Tree,Splunk SPL,Uncoder AI – Blog,SOC Prime Platform,AI Decision Tree,Splunk SPL,Uncoder AI
Views: 2



















































