Source: socprime.com – Author: Steven Edwards
How It Works
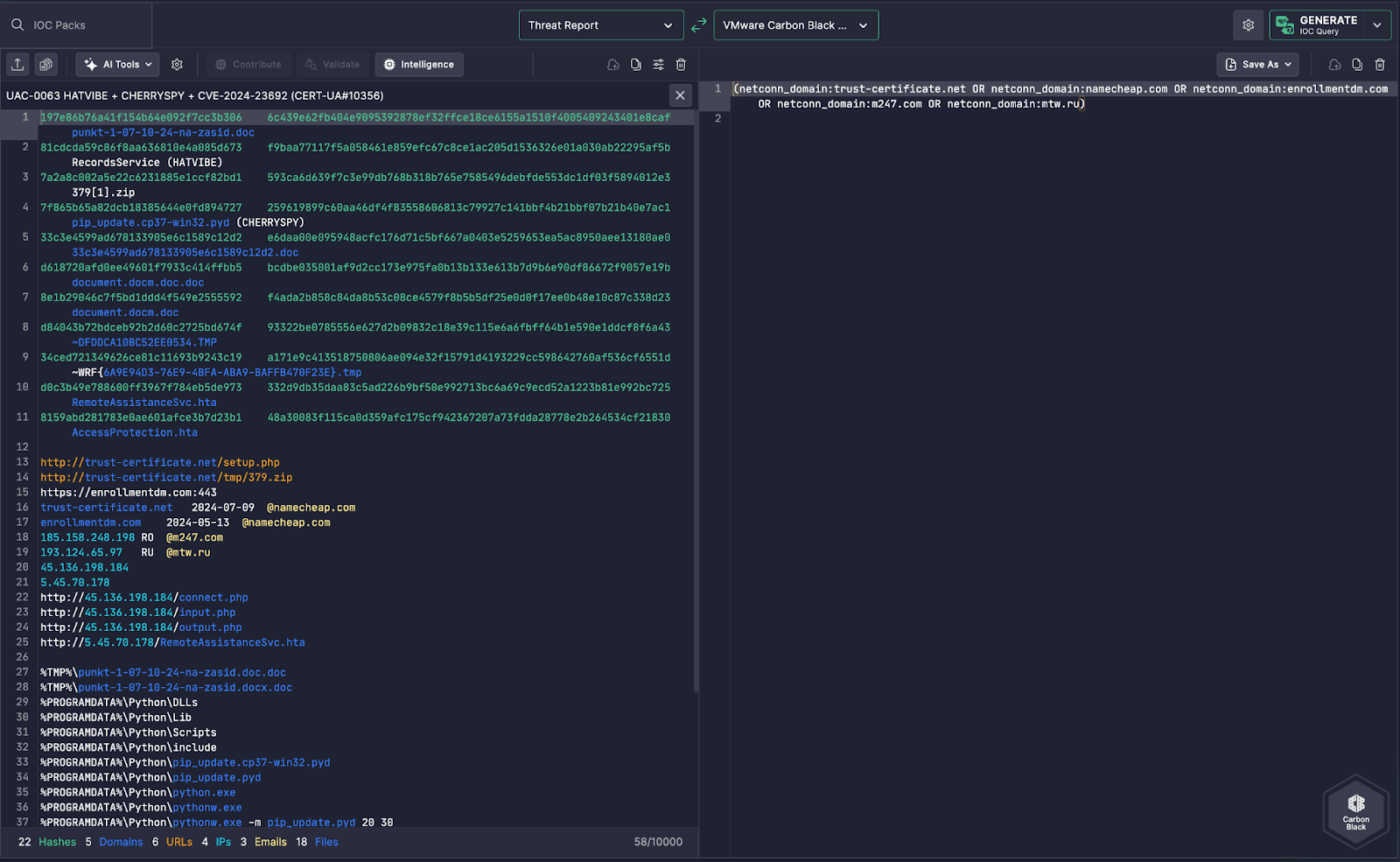
1. IOC Extraction
Uncoder AI scans the threat report (left panel) and identifies malicious network infrastructure associated with:
- HATVIBE and CHERRYSYSPY loaders
- Suspicious communication and command-and-control domains like:
trust-certificate.netnamecheap.comenrollmenttdm.comn247.commtw.ru
These domains are associated with:
- Fake certificate lures
- Python-based loaders
- Malicious HTA stagers
- Credential theft via phishing or post-exploitation scripts
2. Carbon Black Query Generation
On the right, Uncoder AI generates a Carbon Black threat hunting query using the netconn_domain field:
(netconn_domain:trust-certificate.net OR
netconn_domain:namecheap.com OR
netconn_domain:enrollmenttdm.com OR
netconn_domain:n247.com OR
netconn_domain:mtw.ru)
This logic searches for outbound connections from any process to the listed domains — allowing defenders to trace C2 activity or staged malware delivery.
Why It’s Effective
- Field-specific formatting: Automatically uses
netconn_domain— the correct field for Carbon Black network telemetry. - Scalable IOC inclusion: Easily supports multiple domain entries in a single line for batch-hunting.
- Immediate usability: Output is plug-and-play for Carbon Black consoles, with no syntax editing needed.
Operational Value
Security teams using VMware Carbon Black can leverage this feature to:
- Proactively hunt for infections tied to the HATVIBE and CHERRYSYSPY malware families
- Detect suspicious domain beacons linked to post-compromise activity
- Accelerate incident response by pivoting directly from threat intel to platform-native detection queries
Original Post URL: https://socprime.com/blog/domain-based-ioc-detection-for-carbon-black-in-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,Carbon Black,netconn_domain,Uncoder AI – Blog,SOC Prime Platform,Carbon Black,netconn_domain,Uncoder AI
Views: 4




















































