Source: socprime.com – Author: Steven Edwards
In modern cyberattacks, attackers rely not only on payloads but also on clever evasion techniques. One of the most subtle methods? Whitespace padding in command-line arguments—a tactic often used to obscure malicious behavior and throw off static detection.
A recent VMware Carbon Black Cloud Query leverages this concept to detect suspicious .lnk file execution chains. However, understanding the query logic—especially when it includes hex-encoded characters and newline pattern matching—is no small task.
That’s where Uncoder AI’s Short Summary steps in.
Detection Logic Breakdown
The rule triggers when:
- A process has:
- A parent process of
explorer.exe, suggesting user interaction. - Or a command line containing
.lnk, indicating shortcut-based execution.
- A parent process of
- AND the command line contains:
- Excessive whitespace characters: space
(x20), tab(x09), or Unicode whitespace likeu0009,u000B,u000C, etc. - Newline padding: specifically matching patterns like
nnnnn.
- Excessive whitespace characters: space
The presence of these characters implies that the attacker may be using command-line padding to evade signature-based detection or confuse logging mechanisms.
Input we used (click to show the text)
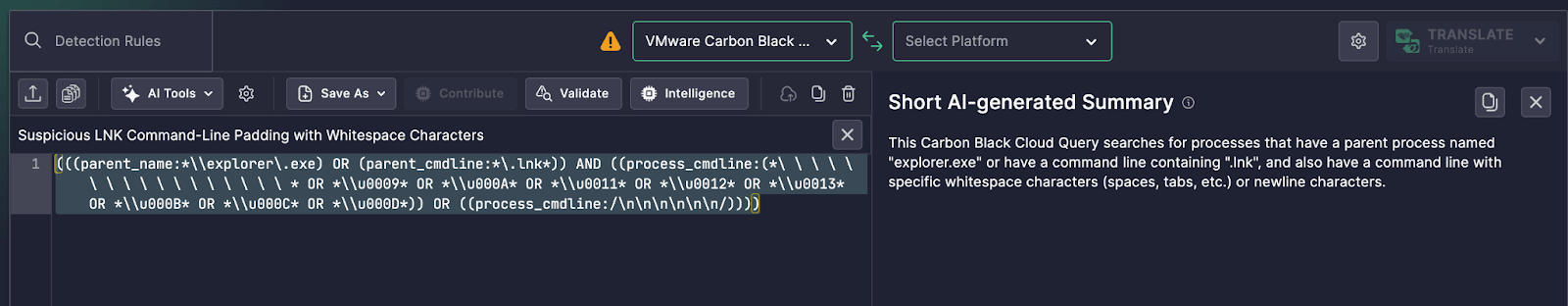
(((parent_name:*\explorer.exe) OR (parent_cmdline:*.lnk*)) AND ((process_cmdline:(* * OR *\u0009* OR *\u000A* OR *\u0011* OR *\u0012* OR *\u0013* OR *\u000B* OR *\u000C* OR *\u000D*)) OR ((process_cmdline:/nnnnnn/))))
What Uncoder AI’s Summary Delivered
Rather than combing through encoded characters and boolean logic, Uncoder AI provided a crisp summary:
“This Carbon Black Cloud Query searches for processes that have a parent process named ‘explorer.exe’ or have a command line containing ‘.lnk’, and also have a command line with specific whitespace characters (spaces, tabs, etc.) or newline characters.”
Just like that, analysts are armed with an understanding of the what, why, and how—without touching the regex.
AI Output (click to show the text)
This Carbon Black Cloud Query searches for processes that have a parent process named "explorer.exe" or have a command line containing ".lnk", and also have a command line with specific whitespace characters (spaces, tabs, etc.) or newline characters.
SOC Advantage with Uncoder AI
Even subtle tactics like whitespace padding shouldn’t go unnoticed. With Uncoder AI’s Short Summary, Carbon Black queries become more accessible, accelerating detection without sacrificing depth.
This is how AI turns complex behavioral rules into everyday SOC understanding.
Original Post URL: https://socprime.com/blog/detecting-suspicious-lnk-whitespace-obfuscation-in-carbon-black-with-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,Carbon Black Detection,Short Summary,Uncoder AI – Blog,SOC Prime Platform,Carbon Black Detection,Short Summary,Uncoder AI
Views: 6



















































