Source: socprime.com – Author: Steven Edwards
How It Works
The showcased feature translates a Linux-based Sigma rule — specifically targeting the sysinfo system call — into Microsoft Sentinel KQL. This system call provides an attacker with system metadata like uptime, memory usage, and load averages — commonly abused during reconnaissance.
Left Panel – Sigma Rule:
- Targets Linux auditd telemetry for syscall
sysinfo. - Includes specific
auditdrule configuration (-a always,exit ... -S sysinfo) for rule applicability. - Applies filtering to exclude benign admin processes like
splunkd.
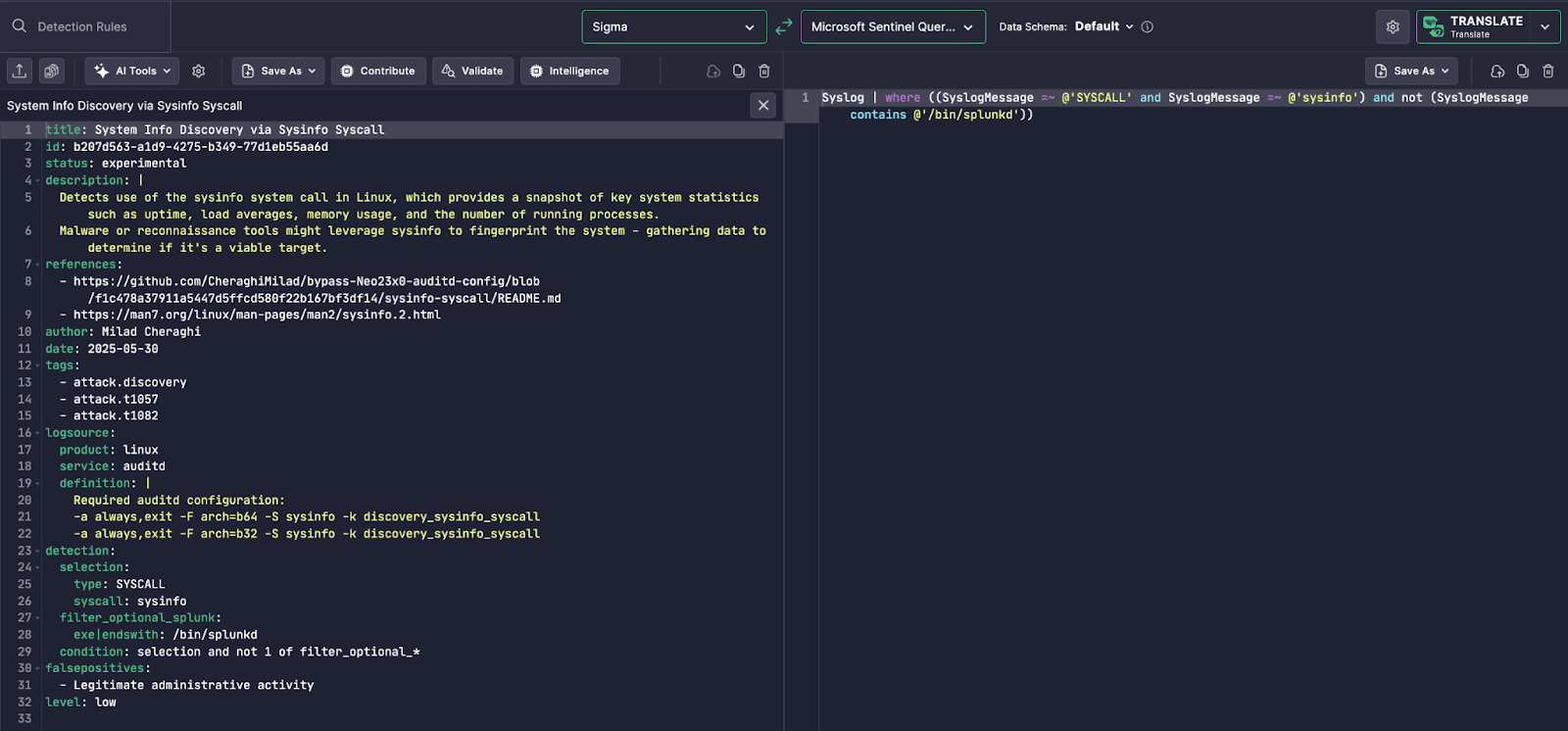
Right Panel – Microsoft Sentinel Query:
Uncoder AI converts the Sigma logic into Microsoft Sentinel’s Syslog-based KQL:
Syslog
|where ((SyslogMessage =~ 'SYSCALL' and SyslogMessage =~ 'sysinfo') and not (SyslogMessage contains '/bin/splunkd'))
This query mirrors the Sigma rule’s logic:
- Filters for syscall events containing
sysinfo - Excludes known benign noise (
/bin/splunkd) - Uses exact and case-insensitive string comparisons for precision
Why It’s Innovative
Mapping Linux-specific syscall detection from Sigma to Microsoft Sentinel requires:
- Translating Sigma’s
auditdabstraction into raw syslog patterns - Understanding platform logging nuances (e.g., KQL field structures)
- Preserving semantic filters (e.g., excluding Splunk agent activity)
Uncoder AI handles this automatically through:
- LLM-powered parsing of Sigma logic
- Schema-aware mapping to Sentinel Syslog fields
- Operator fidelity and filter preservation
This level of cross-platform detection logic normalization is typically time-intensive when done manually.
Operational Value
Security teams gain:
- Broader threat coverage across hybrid cloud + Linux infrastructure monitored via Sentinel
- No need for manual KQL scripting, reducing errors and delays
- Tactical reconnaissance detection with real-world utility against early-stage attacks
- Cleaner signals by preserving custom filters from Sigma into KQL
Uncoder AI empowers detection engineers to operationalize Linux audit rules in cloud-native SIEMs like Microsoft Sentinel — all in seconds.
Original Post URL: https://socprime.com/blog/detect-linux-reconnaissance-in-microsoft-sentinel-with-sigma-to-kql-conversion/
Category & Tags: Blog,SOC Prime Platform,Sigma translation,sysinfo syscall,Uncoder AI – Blog,SOC Prime Platform,Sigma translation,sysinfo syscall,Uncoder AI
Views: 5



















































