10 popular blogs that every CISO should start readingEXECUTIVE SUMMARY: An organization’s CISO contends with a myriad of complex and unique job functions; from fighting for...
Why a robust data corruption policy is vital for your organization
Why a robust data corruption policy is vital for your organizationThis article was written by Milica Vojnic of Wisetek, who specializes in advising businesses in avoiding cyber...
New ‘Robin Banks’ phishing service targets major financial institutions
New ‘Robin Banks’ phishing service targets major financial institutionsEXECUTIVE SUMMARY: This new Phishing-as-a-Service scheme targets employees of major financial institutions; from Bank of America to Santander....
Phishing Bonanza: Social-Engineering Savvy Skyrockets as Malicious Actors Cash In
Phishing Bonanza: Social-Engineering Savvy Skyrockets as Malicious Actors Cash InContenido de la entradaLeer másProofpoint News Feed
Doenerium – Fully Undetected Grabber (Grabs Wallets, Passwords, Cookies, Modifies Discord Client Etc.)
Doenerium – Fully Undetected Grabber (Grabs Wallets, Passwords, Cookies, Modifies Discord Client Etc.)Fully Undetected Grabber (Grabs Wallets, Passwords, Cookies, Modifies Discord Client Etc.) Features Stealer Discord...
ropr: blazing fast multithreaded ROP Gadget finder
ropr: blazing fast multithreaded ROP Gadget finderropr ropr is a blazing fast multithreaded ROP Gadget finder What is an ROP Gadget? ROP (Return Oriented Programming) Gadgets......
Bpflock – eBPF Driven Security For Locking And Auditing Linux Machines
Bpflock – eBPF Driven Security For Locking And Auditing Linux Machinesbpflock – eBPF driven security for locking and auditing Linux machines. Note: bpflock is currently in...
Sports Direct Employee Convicted of Soliciting Murder
Sports Direct Employee Convicted of Soliciting MurderAfter deliberating for four hours at Reading Crown Court, a jury convicted a 26-year-old of soliciting murder via the darkweb.......
hoaxshell: unconventional Windows reverse shell
hoaxshell: unconventional Windows reverse shellhoaxshell hoaxshell is an unconventional Windows reverse shell, currently undetected by Microsoft Defender and other AV solutions as it is... The post...
packj: detect malicious/risky open-source software packages
packj: detect malicious/risky open-source software packagesPackj flags malicious/risky open-source packages Packj (pronounced package) is a command-line (CLI) tool to vet open-source software packages for “risky”... The...
Chicago Police and USPS Seized $2.4 Million Worth of Drugs
Chicago Police and USPS Seized $2.4 Million Worth of DrugsA collaboration between Chicago police and the United States Postal Service (USPS) resulted in the seizure of...
Laurel – Transform Linux Audit Logs For SIEM Usage
Laurel – Transform Linux Audit Logs For SIEM UsageLAUREL is an event post-processing plugin for auditd(8) to improve its usability in modern security monitoring setups. Why?...
What is Cloud Based Access Control and Why Is It Important?
What is Cloud Based Access Control and Why Is It Important?Access Control refers to allowing individuals access to a site, building or office space under certain...
CrackQL: GraphQL password brute-force and fuzzing utility
CrackQL: GraphQL password brute-force and fuzzing utilityCrackQL CrackQL is a GraphQL password brute-force and fuzzing utility. CrackQL is a versatile GraphQL penetration testing tool that exploits......
Facebook Business accounts hacked, customers may find this shocking
Facebook Business accounts hacked, customers may find this shockingEXECUTIVE SUMMARY: As businesses learn to dodge ransomware attacks, cyber criminals are shifting their attention towards other attack...
django-defender: blocks people from brute forcing login attempts
django-defender: blocks people from brute forcing login attemptsdjango-defender A simple Django reusable app that blocks people from brute forcing login attempts. The goal is to make...
Pretender – Your MitM Sidekick For Relaying Attacks Featuring DHCPv6 DNS Takeover As Well As mDNS, LLMNR And NetBIOS-NS Spoofing
Pretender – Your MitM Sidekick For Relaying Attacks Featuring DHCPv6 DNS Takeover As Well As mDNS, LLMNR And NetBIOS-NS SpoofingYour MitM sidekick for relaying attacks featuring...
fuzzuli: find critical backup files
fuzzuli: find critical backup filesfuzzuli fuzzuli is a url fuzzing tool that aims to find critical backup files by creating a dynamic wordlist based on... The post...
GUEST ESSAY: How amplified DDoS attacks on Ukraine leverage Apple’s Remote Desktop protocol
GUEST ESSAY: How amplified DDoS attacks on Ukraine leverage Apple’s Remote Desktop protocolCyber-attacks continue to make headlines, and wreak havoc for organizations, with no sign of...
I’ll update my smartphone tomorrow: The impact of Zero-Day attacks on mobile devices
I’ll update my smartphone tomorrow: The impact of Zero-Day attacks on mobile devicesBy Peter Elmer, Principle Security Expert – EMEA, Member of the Office of the...
Understanding a particular Zero Trust journey from the lens of a CISO at an American healthcare payer
Understanding a particular Zero Trust journey from the lens of a CISO at an American healthcare payerEXECUTIVE SUMMARY: In this interview, the CISO of a healthcare...
AI-based social engineering is the next-generation of hacking humans
AI-based social engineering is the next-generation of hacking humansKeely Wilkins has been in the technology industry for nearly thirty years. She has worked in corporate, higher...
7 key considerations: Zero Trust Network Architecture
7 key considerations: Zero Trust Network ArchitectureEXECUTIVE SUMMARY: Explore seven key considerations for when you and your team evaluate a Zero Trust Network Access (ZTNA) solution...
The end of DDoS attacks is near, with these mitigation measures
The end of DDoS attacks is near, with these mitigation measuresDavid Hobbs currently serves in the Office of the CTO at Check Point while also managing...
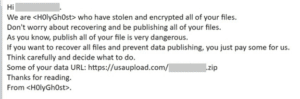
How to prevent Holy Ghost ransomware attacks on small businesses
How to prevent Holy Ghost ransomware attacks on small businessesEXECUTIVE SUMMARY: Holy Ghost ransomware operators have styled themselves as a legitimate corporate entity that tries to...
8 highly effective insider fraud prevention tips for 2022
8 highly effective insider fraud prevention tips for 2022EXECUTIVE SUMMARY: While some threat actors sequester themselves in their parents’ basements or operate out of unmarked buildings...
Security considerations for telehealth businesses
Security considerations for telehealth businessesDevin Partida writes about cyber security and technology. She is also the Editor-in-Chief of ReHack.com. During the pandemic, telehealth garnered extensive attention due...
Darkweb Vendor "Dragoncove” Indicted in New York
Darkweb Vendor "Dragoncove” Indicted in New YorkA three-count indictment accuses a man living in New York of selling heroin and cocaine through vendor accounts on darkweb......
CVE-2022-35741: Apache CloudStack SAML Single Sign-On XXE Vulnerability
CVE-2022-35741: Apache CloudStack SAML Single Sign-On XXE VulnerabilityRecently, A vulnerability that allows attackers to execute XML external entity (XXE) injection has been patched in Apache CloudStack....
Woman Allegedly Tried to Hire a Hitman to Kill Her Coworker
Woman Allegedly Tried to Hire a Hitman to Kill Her CoworkerA 26-year-old allegedly tried to hire a hitman on the darkweb to kill a colleague “when...