Source: socprime.com – Author: Steven Edwards
CrushFTP is a popular file transfer application, but in the wrong hands, it can become a stealthy foothold for lateral movement. A process like crushftpservice.exe spawning common Windows binaries such as cmd.exe , powershell.exe , or wscript.exe often signals that something deeper is at play.
This is exactly the scenario where detection rules written in CrowdStrike Falcon’s language are used to monitor post-exploitation activity. But like many EDR queries, these rules quickly grow complex with layers of logic, wildcard paths, and regex filters.
To accelerate interpretation and response, analysts now turn to Uncoder AI’s Short Summary feature.
What the Rule Detects
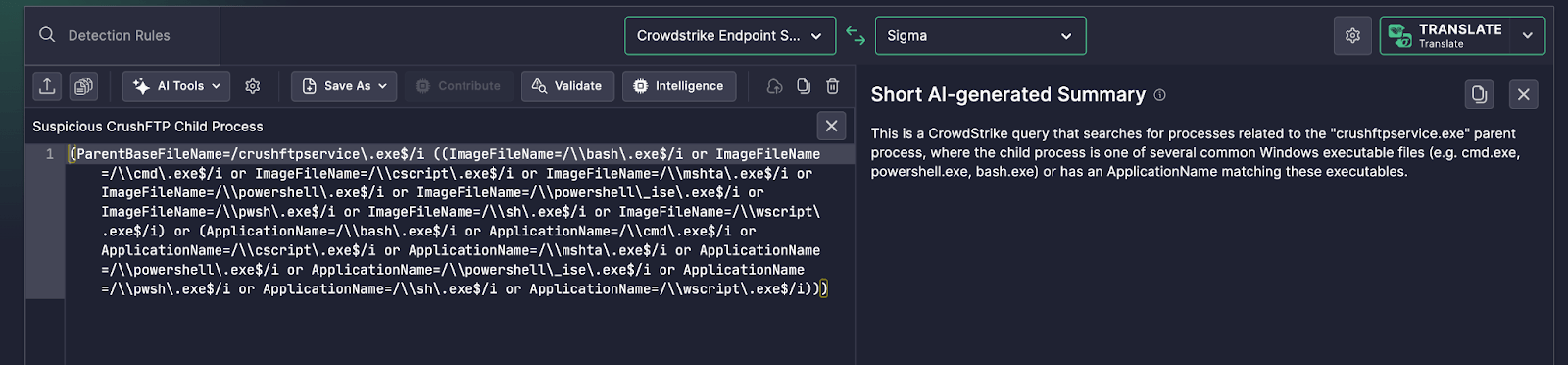
This CrowdStrike query identifies when the crushftpservice.exe process launches child processes that match a known list of scripting engines or command-line utilities. It looks at both the ImageFileName and ApplicationName fields to catch execution regardless of how the process is launched.
Flagged child processes include:
- Command-line interpreters:
cmd.exe,bash.exe,sh.exe - Windows scripting engines:
powershell.exe,powershell_ise.exe,cscript.exe,wscript.exe,mshta.exe - Modern shell variants:
pwsh.exe
Input we used (click to show the text)
DeviceProcessEvents | where (InitiatingProcessFolderPath endswith @'crushftpservice.exe' and (FolderPath endswith @'bash.exe' or FolderPath endswith @'cmd.exe' or FolderPath endswith @'cscript.exe' or FolderPath endswith @'mshta.exe' or FolderPath endswith @'powershell.exe' or FolderPath endswith @'powershell_ise.exe' or FolderPath endswith @'pwsh.exe' or FolderPath endswith @'sh.exe' or FolderPath endswith @'wscript.exe'))
What Uncoder AI’s Summary Delivered
Rather than requiring a line-by-line breakdown of the regex-heavy logic, Uncoder AI summarized the detection in seconds.
This clarity is essential for threat hunters and SOC analysts working in high-pressure situations. It provides a fast understanding of what behavior is being monitored—without diving into syntax.
AI Output (click to show the text)
This is a CrowdStrike query that searches for processes related to the "crushftpservice.exe" parent process, where the child process is one of several common Windows executable files (e.g. cmd.exe, powershell.exe, bash.exe) or has an ApplicationName matching these executables.
Operational Relevance
Lateral movement and hands-on-keyboard activity often begin with one trusted service spawning another process. In this case:
crushftpservice.exemay be used as a launchpad for further commands.- Processes like
powershell.exeorwscript.exeindicate script-based activity—whether to download tools, establish persistence, or exfiltrate data. - Catching these actions early can prevent privilege escalation or deeper compromise.
The Uncoder AI Advantage
When working with CrowdStrike detections at scale, it’s easy to get lost in condition trees and regex patterns. Uncoder AI’s Short Summary makes these rules human-readable, transforming complicated technical logic into operational insight.
Whether you’re briefing a team, conducting retro hunts, or triaging alerts, this feature helps analysts move from query to understanding—instantly.
Original Post URL: https://socprime.com/blog/crowdstrike-child-process-detection-enhanced-by-uncoder-ais-short-summary/
Category & Tags: Blog,SOC Prime Platform,CrowdStrike detection,Short Summary,Uncoder AI – Blog,SOC Prime Platform,CrowdStrike detection,Short Summary,Uncoder AI
Views: 4




















































