Source: www.infosecurity-magazine.com – Author:

ClickFix social engineering attacks have surged by 517% in the past six months, becoming the second most common vector behind only phishing, according to new ESET data.
The report, published on June 26, found that this technique accounted for nearly 8% of all blocked attacks in H1 2025.
ClickFix is a social engineering that uses a fake error or verification message to manipulate victims into copying and pasting a malicious script and then running it.
The tactic preys on users’ desire to fix problems themselves rather than alerting their IT team or anyone else. Therefore, it is effective at bypassing security protections as the victim infects themselves.
The technique was first observed by Proofpoint in March 2024, before exploding in popularity by the end of the year.
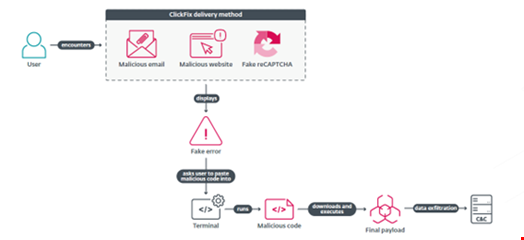
The attack vector affects all major operating systems, including Windows, Linux and macOS.
The report noted that the effectiveness of the ClickFix approach has resulted in threat actors selling builders that provide other attackers with ClickFix weaponized landing pages.
As the number of ClickFix variants has grown, so to have a variety of threats being delivered using this technique.
Jiří Kropáč, Director of Threat Prevention Labs at ESET, commented: “The list of threats that ClickFix attacks lead to is growing by the day, including infostealers, ransomware, remote access trojans, cryptominers, post-exploitation tools, and even custom malware from nation-state-aligned threat actors.”
A separate report published in June by ReliaQuest found that ClickFix was key in increasing detected drive-by-comprises by 10% during the period from March-May 2025.
Major Shifts in Infostealer Landscape
The ESET study also highlighted major shifts in the infostealer landscape in H1 2025, in particular the emergence of SnakeStealer.
This infostealer was the most commonly detected in the period, accounting for a fifth of all infections, according to ESET telemetry data.
It has been in use since 2019, and has a range of capabilities, including logging keystrokes, stealing saved credentials, capturing screenshots and collecting clipboard data.
This infostealer’s rise appears to have coincided with decline of Agent Tesla, which fell by 57% in H1 2025 compared to the previous six month period.
The reason behind the fall in Agent Tesla detections is because the operators have lost access to the servers with the infostealer’s source code, the researchers said.
“It is not completely gone; new versions are just not being developed,” they noted.
May 2025 saw two major law enforcement operations targeting prominent infostealer infrastrcutre, which are likely to heavily impact the landscape further going forward.
This includes the disruption of Lumma Stealer infrastructure, resulting in the seizure of 2300 domains.
Shortly after, US agencies in conjunction with Operation Endgame disrupted a large part of the infrastructure of Danabot.
Before the disruption, Lumma Stealer activity in H1 2025 was higher than in H2 2024, by 21% and Danabot was up even more, by 52%.
Original Post URL: https://www.infosecurity-magazine.com/news/clickfix-attacks-surge-2025/
Category & Tags: –
Views: 2