Source: www.infosecurity-magazine.com – Author:
The US top cybersecurity agency has confirmed that the critical vulnerability in file transfer solution provider CrushFTP’s product is being exploited in the wild.
The authentication bypass vulnerability, CVE-2025-31161, was added to the Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog on April 7.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” said the security advisory.
CISA strongly urged all federal departments and other organizations to prioritize remediating the vulnerability as part of their vulnerability management practice.
Vulnerability Disclosure Mix-Up
The vulnerability is a critical authentication bypass (CVSS base score of 9.8) that could allow an unauthenticated actor to take over devices running unpatched versions of CrushFTP v10 or v11.
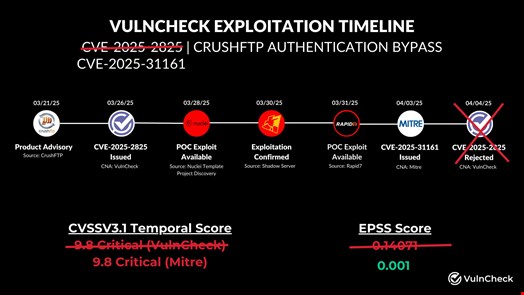
It was identified by Outpost24 and disclosed by CrushFTP on March 21 and has been fixed in versions 10.8.4 and 11.3.1.
However, the vulnerability experienced a disclosure mix-up with two separate vulnerability identifiers published by two CVE Numbering Authorities (CNAs) relating to the same issue.
Outpost24 worked with MITRE, a CNA, to secure CVE identifier CVE-2025-31161.
Outpost24 and MITRE then coordinated with CrushFTP to agree on a 90-day non-disclosure period to ensure users had sufficient time to patch before details became public.
Meanwhile, another CNA, VulnCheck, published a separate identifier, CVE-2025-2825, on March 26, allegedly without consulting Outpost24 or CrushFTP.
Two days later, the Shadowserver Foundation said on X that it was observing exploitation attempts of CVE-2025-2825 based on a publicly available proof-of-concept (PoC) exploit code. The non-profit also identified at least 1512 unpatched instances vulnerable to CVE-2025-2825.
— The Shadowserver Foundation (@Shadowserver) March 31, 2025
MITRE published the CVE-2025-31161 entry on April 3. The CVE-2025-2825 now appears as ‘Rejected’ on MITRE’s website and the US National Vulnerability Database (NVD).
Outpost24 argued in an April 2 security update that the VulnCheck disclosure led to the vulnerability becoming widely known before users could update their systems, resulting in active exploitation.
On the other hand, VulnCheck criticized MITRE for rejecting CVE-2024-2825.
“CrushFTP […] deliberately requested that a CVE not be issued for 90 days, effectively trying to hide the vulnerability from the security community and defenders,” Patrick Garrity, Security Researcher at VulnCheck, said on LinkedIn.
“What’s worse is that MITRE appears to have prioritized their involvement in the write-up over the timely disclosure of a vulnerability actively exploited in the wild… This sets a dangerous precedent,” he added.
Original Post URL: https://www.infosecurity-magazine.com/news/crushftp-vulnerability-cisa-kev/
Category & Tags: –
Views: 4



















































