Source: news.sophos.com – Author: Matt Wixey
Content warning: Because of the nature of some of the activities we discovered, this series of articles contains content that some readers may find upsetting. This includes profanity and references to drugs, drug addiction, gambling, pornography, violence, arson, and sex work. These references are textual only and do not include images or videos.
Following on from Part One in our series on threat actors investing in business interests outside cybercrime, we take a look at so-called ‘white’ activities (a term used by some cybercrime forum users, referring to purportedly legitimate businesses). While not necessarily illegal themselves, these activities are often connected to, and tainted by, criminal activity.
We acknowledge that legality can vary depending on jurisdiction. However, the breadth and depth of these activities are such that we have to categorize them somehow, and using the threat actors’ own categories is a logical if imperfect choice.
Key findings of Part 2
- On criminal forums, threat actors are discussing a wide range of ‘legitimate’ business interests (known as ‘white’ on the forums), spanning multiple sectors and industries – including gold, diamonds, real estate, construction, stocks and shares, restaurants, education, and many more
- While some of these activities may relate to money laundering, some threat actors may also be seeking to invest and diversify
- Many threat actors sought, and received, advice from peers on where and how to invest money
- Some of the business interests we report on here could have significant ramifications for the security industry – including investment in cyber security companies; attempting to evade export and import restrictions; and operating proxy, hosting, and VPN services
- In some cases, forum discussions revealed information and images that could potentially be used to track, geolocate, and/or identify threat actors
Shell companies
While shell companies are often created for money laundering purposes (see Part One), we found a few interesting variations on the forums.
Shell-companies-as-a-Service
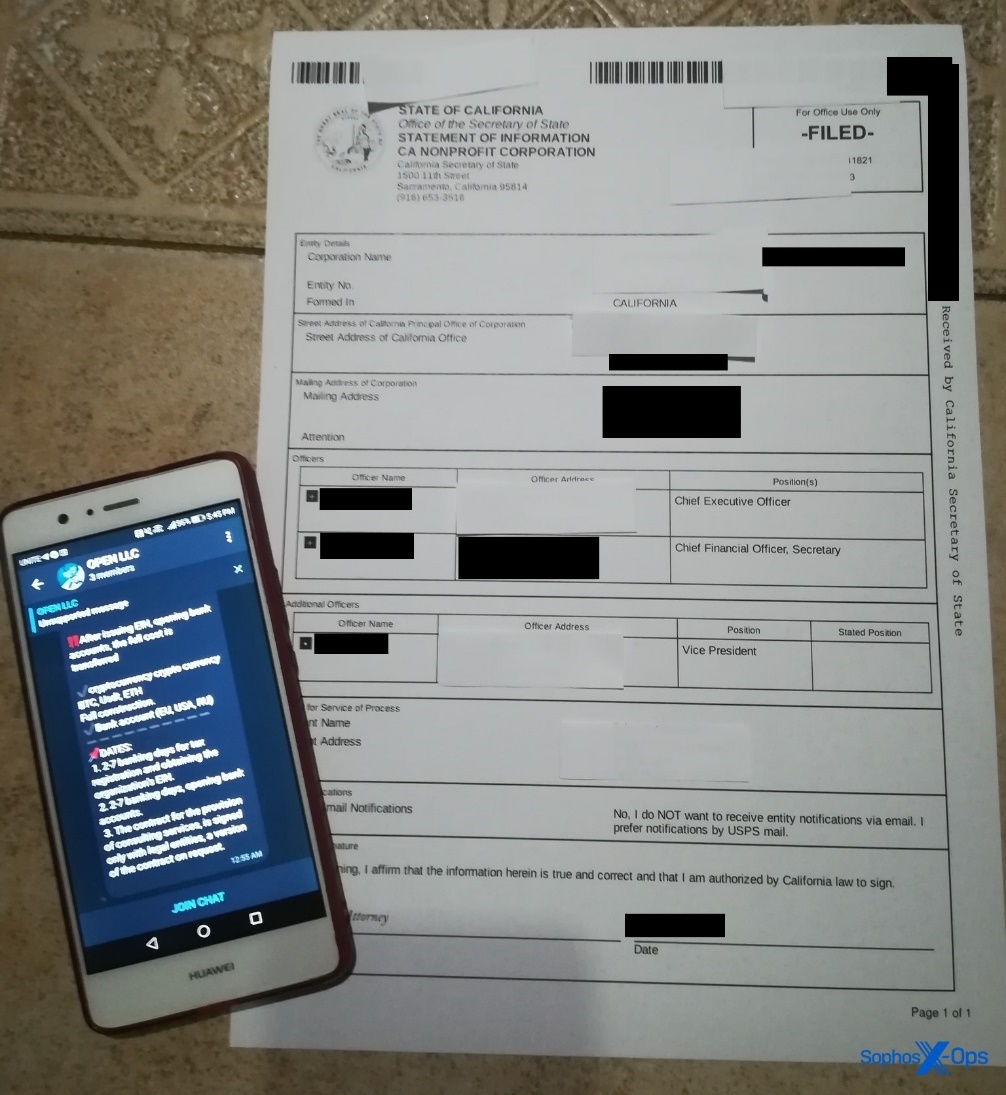
One threat actor posted an advert offering to sell three US-based ‘turnkey’ companies and bank accounts ($3900), or register a new US company and three bank accounts under a buyer’s representative ($4990) or their own representative ($3500). This post was accompanied by a photograph of a State of California Statement of Information for a Non-Profit Corporation. The threat actor obscured some details, but some names, addresses, and a document reference number were still visible.
Figure 1: A threat actor posts an advert for creating shell companies
Figure 2: The same threat actor posts an example statement of information. Note that while the threat actor redacted some of this themselves (with slips of white paper), other potentially useful information (which we have redacted in black) was still visible
We also observed a service offering to open companies in the UK, Gibraltar, and Panama ($1900) to facilitate a technique called “cuckoo smurfing,” which involves insiders in money services intercepting legitimate transactions and mixing them with illicit ones.
This threat actor provided an example of a company which they claimed to have registered, including the name and company number. According to the user, the service includes a virtual office, a UK address, articles of association, certificate of incorporation, and a UK phone number.
We looked into the example company and found that it had been active for over a year before being compulsorily struck off. Via Companies House (an agency that holds the public register of UK companies), we were able to identify the director, and the name and address of the agency that registered the company (and which has acted as an agent for multiple other UK companies, some of which are still active – although some or all of these may be legitimate).
Figure 3: A threat actor posts an advert for registering companies and outlines a technique they call ‘cuckoo smurfing’
Figure 4: The same threat actor provides an example of their “latest work,” which we checked on Companies House
Evading restrictions
One threat actor sought advice on how to register companies for software with “corporate verification…no, it is not Cobalt Strike.”
Another user said that they could create a US-based company to order “sensitive technologies.” The user stated that “chips/software/engines/other will be sent to Latin America, from there to any other place we agree.”
Figure 5: A threat actor offers to create companies “to order sensitive technologies”
Cybersecurity
Hash decryption
We found a proposal to set up a hash decryption service, using Google Cloud, AWS, or Azure. While it is not necessarily illegal to operate or use a hash decryption service, cybercriminals can use them to ‘break’ hashes (e.g., from data breaches) and recover plaintext passwords.
Investment
We also saw a recommendation to invest in a prominent cybersecurity vendor (along with details of a rumor that it was going to acquire another company). Irony aside, this raises the concerning possibility that threat actors could become shareholders (and therefore able to vote on corporate actions, receive dividends, etc.) of a company that tracks and disrupts threat actors.
Figure 6: A threat actor recommends investing in a very well-known cybersecurity vendor
Start-ups
We observed two proposals to create security start-ups. The first was “to develop exploits and analyze software and hardware vulnerabilities.” The other focused on “legal ways to sell already found vulnerabilities to those who didn’t ask for it.” In both cases, users suggested that this would be better suited to the US or Europe than Russia.
One user also took the opportunity to criticize the cybersecurity industry (“threat intel…is nothing, just snake oil…apparently it’s profitable and they buy it, but the costs are 3 forum parsers and a blog on Twitter”).
Figure 7: A threat actor promotes their cybersecurity start-up on a criminal forum, and notes that they are seeking “people with relevant knowledge” in vulnerability research, debugging, coding, and fuzzing
IT and internet services
Online services
Threads on this topic included:
- An existing domain trading business
- An API marketplace
- A call for business partners “to sell our services…we are 14 years old [sic] agency dealing in IT solutions.” Said solutions included website and software development, social media, and email marketing.
Figure 8: A threat actor seeks a business partner for a pre-existing “IT solutions” company
Mobile apps
Various threat actors are seeking investment in mobile apps, including a mobile fitness app startup, and an investment opportunity for a pre-existing suite of mobile applications developed in Kazan, Russia.
This suite, distributed as a franchise, included apps for:
- Loyalty points and affiliate programs
- Offers
- Facilitating customer feedback
- Collection of client data, and more
Some users suggested that this was a form of multilevel marketing (MLM), akin to a pyramid scheme – more on which later in this series.
Figure 9: A threat actor seeks a partner to work on a new mobile fitness app; the work includes “communicat[ing] with clients and maintain[ing] Instagram…the payment is a third of the project, this is a startup”
Social networking
Threads in this vein included an investment opportunity for an “Instagram killer unicorn” and a business plan to set up a social network hosted in the UAE.
Physical services
One threat actor recommended that their peers “create your own service for repairing Apple devices,” including bypassing iCloud activation, installing jailbreaks, removing Apple IDs, etc.
Figure 10: A threat actor invites their peers to consider creating their own service “for repairing Apple devices…it’s relevant now, investments are minimal [and] the work is white”
Interestingly, we also observed a business plan for digitizing VHS tapes.
Cryptocurrency/currency exchanges
We noted several business proposals and investment adverts relating to this topic, including:
- Exchanges using Tor/I2P and a mixer, without KYC (Know Your Customer), and therefore ideal for money laundering
- NFT marketplaces (including a ready-made service, available to buyers for 1 million rubles)
- An investment opportunity for cloud mining (“where you got the money from doesn’t matter to me…the approximate return on your funds…with an investment of 200-300k green [i.e., USD]…[is] millions of dollars”)
- An investment opportunity for the development of GPU farms in Ukraine
- A proposal to develop a new cryptocurrency hardware wallet.
Figure 11: A threat actor looks for investment for the development of GPU farms in Ukraine (posted prior to the Russian invasion of Ukraine in 2022)
One user stated that they had come into ownership of a “small office space (80sqm) on the outskirts of London…inside of which there are a dozen servers [and] a wonderful 10 GBPS internet channel that has been supplied and already paid for two years.”
The user said: “I am legally in England, I have my own business (another one)…how can I use this entire system to squeeze out maximum profits?” Ideas from other users included: game servers, hosting, and becoming an ISP (this last from a user who claimed to have operated an ISP for 13 years). In the end, the user decided to create an Ether mining farm.
Figure 12: A thread in which a threat actor sought business ideas and possible partnerships for office space “on the outskirts of London,” complete with a “10 GBPS Internet channel”
Hosting and proxy services
We saw several proposals and existing businesses relating to hosting and proxy services (“I bought all equipment, invested around $10k”; “I own several…SaaS, IoT, e-commerce and brokerage, 4 in USA, 1 in UK”).
This latter threat actor claimed that their SaaS and hosting services were “grey,” that they had made 80k via PayPal on their e-commerce business, and that for brokerage “I just do exchanges under my own CPA licence.”
Figure 13: A threat actor seeks advice relating to their proxy service
We also saw a thread referring to a pre-existing, five-year-old hosting company with its own data center, “located in a bomb shelter of a former military plant at a depth of 5 meters underground…everything is equipped and working, but there are few clients.”
Figure 14: A threat actor seeks advice on how to obtain more clients for their pre-existing hosting company “located in a bomb shelter of a former military plant”
Threat actors operating hosting or proxy services (or any other ‘legitimate’ IT or online service) raises the possibility of users’ data and activities being illicitly inspected, stolen, sold, or otherwise misused – as well as threat actors being able to use their own infrastructure for attacks.
Fronts
There were several suggestions for IT/internet-related ‘fronts’ for money laundering and legitimizing income, including a “No Audit Logs VPN Service”, a “Shitcoin & NFT Meme project”, and an “Online Casino Project” which would allow a threat actor to “coincidentally win…a huge six figure jackpot.”
Figure 15: A threat actor posts several suggestions for “legitimate business[es] which I can mix my dirty finances in”
Gold and diamonds
Investment
We found a detailed guide on investing in gold, which the author had apparently done since 2010. The poster provided detailed options:
- Buying bullion (easy but requires an 18% tax)
- Buying investment coins (no tax, accessible and profitable, but more expensive)
- Opening a gold bank deposit (suitable for short-term investors)
- Buying shares in gold mining companies (higher risk, but potentially higher profits).
The threat actor noted that the optimal solution for most investors is to open a gold deposit in a bank, and shared several (Russian) links.
Figure 16: A threat actor posts a guide on investing in gold, detailing several methods
Cryptocurrency for coins and gold
A user shared information on how to exchange Monero for coins and gold bars anonymously: using certified suppliers on a P2P offshore marketplace (“Liberland Shield”) to purchase US Mint gold coins, and bars from PAMP Suisse, which the buyer took delivery of at a “stealthy address that I usually use to receive cash by mail when I exchange XMR for cash on LocalMonero.” The buyer purportedly took some of the bars to California, and exchanged them for cash.
Figure 17: A threat actor (the same user who previously admitted to bribing homeless people with money or drugs to get them to open bank accounts, in Part One) describes a method for exchanging Monero for coins and gold bars
Diamonds
One threat actor noted that diamonds can be changed to cash, can be hidden in a safety deposit box in a relative’s name, and are untraceable (“unless your [sic] stupid.”).
This user also outlined a scheme to launder using diamonds:
- Learn the diamond trade and get a dealer’s license
- Go to “countries in Africa,” buy diamonds for $10,000 and ask for a receipt for $300,000
- Give the diamonds to another dealer, along with $350,000 in ‘dirty money’
- Ask that dealer to send the $350,000 to your bank account, and provide a receipt.
This user also argued that diamonds are better than gold because it’s “easier to pass through customs…[and] everyone in the industry is dirty and tight-lipped.”
Figure 18: A threat actor outlines the advantages of trading diamonds when it comes to money laundering, describing it as “a money launderes [sic] wet dream”
Stocks, shares, and investments
Threads on this topic included:
- Users seeking advice on how to buy stocks and shares, how to select a broker, and whether they should invest in American or Russian companies, or in in countries (“mainly China”) that “want to occupy a certain business niche in our country”
- A user interested in long-term investment ($50,000-$100,000) in the economies of foreign countries (“the priority is not profitability, but the safety of the deposit…and free access to funds”)
- A user seeking “contacts of American entrepreneurs” for investing in a startup
- A user planning to invest their coins in “trading features”, with a request for partners “who can register the company and open the accounts on the global exchanges.”
Figure 19: A threat actor seeks advice on investing in China
We also observed advice and proposals, such as:
- A recommendation to invest in Index Funds “like the S&P 500, it provides a decent rate of return of 11% year over year”
- A proposal to co-invest (“we determine the capital you trade, I tell you when to enter and exit the position and for how much. Profit sharing: 60% for you, 40% for me”)
- An individual based in London “looking for a business partner for a profitable financial investment”
- Advice on selecting a reliable broker (including the note that “in light of recent events [presumably the invasion of Ukraine in 2022], they [American brokers] hardly work with the Russian Federation, but there are always workarounds”)
- Detailed guides on launching startups, including advice on securing investors, making presentations, pitching, and applying to business accelerators
- A post by a user claiming to be an investor and looking for areas to invest in.
Figure 20: A threat actor who claims to be “living in London” posts on a criminal forum “looking for a business partner…for a profitable financial investment…priority is given to people from the UK”
We also noted numerous threads where users said they had a specific amount of money (usually tens or hundreds of thousands of dollars) and wanted investment ideas. For example, we observed a thread in which a user who “earned a small capital on topics that I regrettably tempered” wanted advice on how and where to invest “in white at 20-30% per annum.” They proposed several ideas, including car resale, a product from China, and citizenship for Russia, Romania, and Moldova.
A user replied with in-depth advice, before commenting: “I will also give the traditional recommendation: return to those topics where you made money.” (This latter point was a common theme, and we’ll cover reinvesting in cybercrime later in this series.)
Figure 21: A threat actor asks their peers where to invest “a small capital [that I acquired from] topics that I regrettably tempered”
Other threads of this nature included:
Someone who said they were about to start a two-year sentence in a US federal prison (for trafficking firearms) and wanted to invest $2500 in something, so that they would have funds when they were released
- Where to invest $100,000 in a “grey” business (suggestions included real estate, stocks, crypto, buying a bar, renting cars, and gold)
- Where to invest 100-300k rubles (suggestions included shares, trading, real estate, construction, and vehicles)
- Where to invest $700,000 (suggestions included game development, buying shares in prominent tech companies, and hotels)
- A user who was looking for investment recommendations “in the hot new trends due to the war [presumably the Russian invasion of Ukraine], especially in oil and gas”
- Where to invest $80,000-$100,000 (this thread included the user providing several biographical details about themselves and their acquaintances)
- What business to open in Russia with $500,000.
This latter thread also included some biographical information, along with a comment that likely resonated with a lot of users: “There is no pension in our profession, brother.”
Figure 22: A (purportedly) US-based threat actor, about to go to prison, seeks investment advice on a criminal forum
Figure 23: A threat actor claiming to be an investor asks their peers to submit investment proposals, but states that they are not interested in scams, construction, real estate, drugs, or restaurants
An interesting sidenote: on this latter thread, a user also shared a Vocaroo clip containing a Russian rap song themed around cybercrime. (Excerpt: “It used to be that you could get banned for working on RU / Now it’s practically a fucking matter of routine / Buying all the traffic to their fucking lockers / Killing bots for pennies like beggars.”)
Real estate
Investment
We observed several threads by threat actors seeking to invest in real estate, including:
- A user asking about purchasing real estate in the UAE and whether authorities there require information about the source of funds
- A user, after having “never officially worked”, asked about investing in real estate and how to “appear white and fluffy before the state (Russia)”
- A question about how to buy real estate in Europe if you’re based in the Russian Federation (answers included: looking into legalizing funds, saying the money was a gift from a relative, and using NFTs).
Figure 24: A threat actor asks their peers whether authorities in the UAE require information about the source of funds when purchasing real estate there
Advice
We also saw threads by threat actors already involved in real estate. These included a method of using plots of land to launder money: “I found dirt cheap plots of land in the middle of the deserts and mountains. The sellers don’t check backgrounds or credit…I literally enquired about one last night and signed the contract this morning.”
Figure 25: A threat actor shares details of a scheme for money laundering via plots of lands
We also found a guide on real estate projects in rural areas, including prices, construction costs, ROI, and services (LLCs, cash bank transfers, experienced contractors) based in St Petersburg and Moscow. The author (who has apparently “been building for many years”) mentioned specific projects they had worked on, and uploaded two photographs, possibly relating to those projects.
Figure 26: A threat actor shares a photograph that may be related to a real estate project they worked on. The original source is unclear
Lastly, we noted a thread by a user who claims to know an acquaintance with a real estate company: “If you are looking for ways to launder your money I can arrange a deal, because he accepts crypto. 2 room apartments (64sqm) are 54,000 EUR.”
Industry discussions
One user wondered why “there seems to be a growing trend for…turning to property…what happened to sunbed salons, tattoo parlors, car washes, dog breeding, or hospitality?…I’m strictly speaking from a British perspective and have no idea what the situation/trends are in USA/Europe.” Users commented that “real estate is so popular…because not only is it quite easy to do but you can clean a lot in a much shorter amount of time.”
Figure 27: Threat actors discuss the “growing trend for drug dealers turning to property for money laundering”
Construction
We saw a detailed scheme for profiting from the reselling of construction materials (wood, metals cement, concrete, mortar, etc.). The scheme involved finding suppliers (several Russian suppliers were named), offering to sell their goods for a small percentage, and seeking buyers on Avito (a Russian classified ads marketplace) and VKontakte. The thread included multiple screenshots from a WhatsApp conversation, featuring a photo of a construction site and a screenshot of a bank transfer confirmation.
Figure 28: One of several WhatsApp screenshots in a thread on “making money from building materials.” Note the photograph of a location, and an attached bank transfer confirmation (the user also posted a separate screenshot of this). While some of the information in the bank transfer confirmation was redacted, it still featured some potentially useful information, including the amount and the date and time
Moreover, we observed several construction investment opportunities and schemes, including:
A user who solicited advice on the best scheme to make money upfront before selling houses/apartments (“I found that collective investment scheme is ok, any alternatives?”)
An investment opportunity ($500,000+) for a construction project in Russia, with an ROI of 20% per annum (2-5 years)
An investment opportunity ($500,000; ROI: double in two years) in an apartment complex project. Apparently the user could not get a loan from the bank, so they turned to a cybercrime forum (“I don’t care about color [i.e., if the money is from ‘white’, ‘grey’, or ‘black’ activities], I can start it up and get it out beautifully”).
Figure 29: A threat actor seeks investment of $500,000 for “the construction of an apartment complex”
Restaurants and catering
Restaurants
We saw several proposals and pre-existing businesses relating to restaurants, including a proposal to start a food delivery business during the COVID-19 pandemic. One user (somewhat ironically, given their membership of a criminal forum), noted that “it is a question of internal ethics whether to make money from an epidemic.”
Figure 30: A threat actor proposes starting a food delivery business during the COVID-19 pandemic, and seeks business advice from their peers
We also observed an investment opportunity in a pre-existing catering/pizza delivery business with an annual revenue of 5,000,000 rubles. The investment sought was between 300,000 – 2,000,000 rubles, to open a second store.
Figure 31: A threat actor seeks “an investor or business partner” in a pre-existing and “completely white” pizza delivery company
Alcohol
A threat actor was interested in purchasing someone else’s alcohol business. They mentioned a price, noted that the business had a license and the relevant documentation, and asked for advice on acquisitions from other users.
Figure 32: A threat actor asks their peers to describe the potential “pitfalls” of acquiring an alcohol business
On another thread, we saw a user suggest investing in a barrel of whisky and then selling it for profit.
Ice cream wars
Of all things, we noted a threat actor who wanted to launch an ice cream business. They asked others whether it would be feasible to open a stall with 200,000 rubles.
Figure 33: A threat actor proposes opening an ice cream stall
In the same thread, another user, apparently an ice cream business owner themselves (“the master of the ice cream business”) confessed to having committed arson against a competitor’s ice cream kiosk in the early 2000s (now that “the statute of limitations…has already passed”). They provided detailed information about what happened and how they did it (“a crowbar, a plastic bottle with gasoline, a wick on an extension cord, matches… I noticed a vertical hollow pipe sticking out on the roof [of the kiosk]… I poured the whole bottle into it, stuffed a wick soaked in gasoline, and set it on fire… at about ten o’clock the merchant himself arrived with a crane. They loaded the stall onto a truck and I never saw that business or that stall again”).
Education
Coding school
A threat actor who “worked on logs for a long time, accumulated capital” (i.e., they profited from infostealers) had an idea to open “a programmer school in the direction of web development,” aimed at 16-year-olds. The user noted that there is little competition and “no in-person schools in my million-plus population”, and proposed charging students 400 rubles per academic hour.
Figure 34: A threat actor proposes setting up a “programmer school” aimed at “schoolchildren 16+ years old,” with capital they acquired from “work[ing] on logs for a long time”
Online courses
A user asked for advice on how to sell video courses, information products, webinars, seminars, coaching, training, anything, and asks for investment of “no more than 1000 rubles.” This is possibly related to some form of traffic generation activity (see Part Three of this series).
Tobacco and vaping
Tobacco products
One threat actor was interested in selling tobacco products. Users commented that the market is dominated by suppliers in Ukraine and Belarus, and suggested vapes (“purchasing them in China from a supplier costs 45-100 rubles”). Another user mentioned that they have a vendor for counterfeit cigarettes, but only for delivery within Russia.
E-liquid (and an argument)
A threat actor noted that for the last two years they have been selling e-liquid to schoolchildren, making 100-200 Euros per month. Another user (and remember that this is on a criminal forum) expressed outrage: “I’m reading this as a parent…don’t you fucking have children?”).
Entertainingly, the two threat actors began to argue (“In the stores there is alcohol, cigarettes…maybe you should go to the mommies’ forum?”; “LEAVE YOUR ADDRESS…WE’LL COME NOW, WHEREVER YOU ARE”; “I don’t give a fuck about other people’s children”, etc.).
Another threat actor noted: “I’m laughing…[they] came up with a business that is a hundred years old and which brings in as much as 200 euros a month!”
Figure 35: A threat actor describes a scheme for selling e-liquid to schoolchildren, which sparked an argument
Buying and selling debt
A threat actor decided to get involved in bankruptcy auctions, to buy land plots, houses, machinery, and equipment.
Figure 36: A threat actor decides to get involved in bankruptcy auctions, and asks their peers for “links to bidding aggregators or maybe someone might have some useful video courses”
Another opened a discussion on buying and selling debt, noting that “Tinkov Bank [a Russian commercial bank] accepts debts as authorized capital when opening an LLC through them.”
Films
We observed a proposal to invest cash in a movie with a “legit ROI with reasonable terms.”
Figure 37: A threat actor seeks investment in a movie
Charities and NGOs
Setting up an LLC
A user asked for OPSEC assistance in creating an LLC. They proposed a scheme:
- Open an account using a deceased or elderly person’s details
- File a church under a different name in New Mexico
- File the LLC under the name of the church
- Make weekly deposits in the bank account
- Conduct their “operation”
- Use “slot apps” to wash the profits, or send themselves the money to the church as tithes.
Other users provided specific suggestions, including filing the LLC’s articles of formation with the proper agency in New Mexico, checking how to file an LLC for a church, and filing for 501(c)(3) status to obtain tax exemption. They also recommended “staying legally compliant.”
Figure 38: A threat actor seeks OPSEC advice for creating an LLC under the name of a church in New Mexico. Note that while setting up an LLC is of course not illegal in itself, the proposed scheme here appears to be explicitly criminal (note the stated aim to “wash the money”)
Figure 39: In the same thread, another user provides specific technical feedback on the proposed scheme
‘Big anonymous contributions’
We noted an enquiry from a user (presumably a launderer) on jurisdictions that allow non-profits, charities, or NGOs to “accept big anonymous contributions…I need to set up a charity, NGO or non-profit for a client whose cash businesses are at their limit.” Responses included advice to “stick to US entities…if you live in California and you collect a cheque from a non-profit in Guinea-Bissau, that is a major red flag…you can easily open LLCs, S-Corps, even 501(c)(3) non-profits without your name or office ever touching the registry; there are hundreds of law firms happy to help you with this.”
Further specific advice on privacy, other red flags, non-profit executive salaries, donation caps, and promotional activity followed.
Figure 40: A user provides technical advice on setting up a non-profit for money laundering
Other schemes
We also noted a wide array of other pre-existing businesses, investment proposals, and ideas for start-ups, including, but not limited to:
- A taxi service
- A dating site
- Growing microgreens
- Motocross
- Food trucks
- Money laundering using Steam, TikTok, and Fiverr
- Selling luxury watches
- A beauty salon
- A tattoo parlor
- Reselling protective masks and hand sanitizer (during the COVID-19 pandemic)
- A prepper/survivalist store
- SEO for plumbers, contractors, etc.
- Wholesale and retail of honey
- Manufacturing gazebos and furniture
- Drive-through coffee shops
- Photo booths
- Thermal inspection of houses
- A slingshot shooting range
- Interior design
- Aerial photography
- Laundry services
- Growing crickets for pet stores
- Reselling shoes
- An escrow service
- A casino
- An Arabic restaurant in Moscow
- Bizarrely, selling Soviet-era gas masks on eBay and Amazon
Figure 41: Multiple users contribute to a discussion on ideas for businesses as fronts for money laundering
Figure 42: A threat actor suggests reselling protective masks and hand sanitizer at the height of the COVID-19 pandemic
Figure 43: A threat actor sketches out multiple ‘legitimate’ business ideas, including “a slingshot shooting range,” “interior design,” “drones (aerial photography),” “cleaning and painting of alloy wheels,” and “growing crickets for pet stores”
We also saw a suggestion that a group of users should ‘club together’ to start a “white business” such as e-commerce, or acquire an existing business.
All in all, threat actors are discussing, investing in, and operating a bewildering array of so-called ‘legitimate’ businesses on criminal forums. This has some concerning implications generally, but also specifically for the security industry. For example, threat actors holding shares in a cybersecurity vendor, or operating hosting and proxy services, could adversely impact trust, privacy, and attempts to track and disrupt cybercrime.
However, as we’ll discuss later in this series, these challenges are also accompanied by opportunities. In many discussions, for example, threat actors reveal something about themselves – whether that’s specific, identifiable, biographical information, or locations, or other information that could be useful to investigators.
Before that, in Part Three of this series, we’ll explore some of the more dubious business interests we found during our investigation.
Original Post URL: https://news.sophos.com/en-us/2025/05/15/beyond-the-kill-chain-what-cybercriminals-do-with-their-money-part-2/
Category & Tags: Threat Research,beyond the kill chain,cybercrime forums,Finance,Money Laundering,Ransomware,Sophos X-Ops – Threat Research,beyond the kill chain,cybercrime forums,Finance,Money Laundering,Ransomware,Sophos X-Ops
Views: 2