Source: www.techrepublic.com – Author: Drew Robb
We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not the content of our reviews. See our Terms of Use for details.
Looking for the best SIEM tool? Check out our list and find the security information and event management solution that fits your business needs.
- Best for log aggregation: SolarWinds
- Best for remediation: CrowdStrike Falcon LogScale
- Best for cloud-native environment: Splunk Enterprise Security
- Best for customization: Datadog Security Monitoring
- Best for on-premises: LogRhythm SIEM
- Best for large enterprises: RSA NetWitness
- Best for small businesses: ManageEngine Log360
- Best for IBM shops: IBM Security QRadar SIEM
- Best for Windows shops: Trellix Security Operations and Analytics
- Best for asset discovery: AT&T USM Anywhere
Software Spotlight: CrowdStrike
CrowdStrike Falcon® Next-Gen SIEM is a cloud-native platform that combines first- and third-party security and IT data, threat intelligence, AI, and automation to help organizations detect, investigate, and respond to threats with unprecedented speed and efficiency.
- Unified Insights: Integrates endpoint, identity, and cloud telemetry with third-party data for comprehensive visibility.
- Efficient Scalability: Manages petabyte-scale data with an index-free architecture for seamless storage and retrieval.
- Unmatched Search Speed: Delivers search performance up to 150x faster than legacy SIEMs, enabling rapid investigations and response.
Learn more about Falcon Next-Gen SIEM.
Security information and event management (SIEM) is a device and environmental analysis strategy intended to help secure and protect company operations, data, and personnel. By providing a comprehensive analysis of security-related details and related recommendations, SIEM tools assist in ensuring compliance and remediating potential or active threats.
A recent report published by the IMARC Group found that the global SIEM market reached almost $5.8 billion in 2023. The same report says the market is expected to climb to around $14 billion, especially with more companies investing more resources in protecting against potential threats and resolving vulnerabilities.
With that in mind, we take a look at the best SIEM tools and SIEM software solutions available today.
Top SIEM software comparison
Those wishing to adopt SIEM or planning to upgrade a legacy SIEM tool to a modern platform should carefully evaluate the available tools. Features such as cloud and on-prem functionality, remediation capabilities, and the platforms supported should be among the top areas to be considered.
| Cloud | Hosted on-prem | Remediation | Platforms | Pricing | |
|---|---|---|---|---|---|
| SolarWinds SEM | Yes | Yes | Includes some automated remediation features. | Windows, Linux, and Mac. | Starts at $2,992 |
| CrowdStrike Falcon LogScale | Yes | No | Full range of remediation capabilities. | Windows, Linux, Mac, and Chrome. | Contact for quote |
| Splunk Enterprise Security | Yes | No | Some remediation capabilities. | Windows, Linux, and Mac. | Reportedly $173 per month up to $1,800 per GB |
| Datadog Security Monitoring | Yes | No | Limited remediation capabilities. | Windows, Linux, and Mac. | Starts at $15 per host, per month |
| LogRhythm SIEM | Yes | Yes | Limited remediation capabilities. | Windows, Linux, and Mac. | Contact for quote |
| RSA NetWitness SIEM | Yes | Yes | Limited remediation capabilities. | Windows, Linux, and Mac. | Contact for quote |
| ManageEngine Log360 | Yes | Yes | Limited remediation capabilities | Windows, Linux, and Mac. | Personalized quote via online form |
| IBM Security QRadar SIEM | Yes | Yes | Full remediation capabilities. | Windows, Linux, and Mac. | Personalized quote via online price estimator |
| Trellix Enterprise Security Manager | Yes | Yes | Remediation capabilities only available with purchase of additional Trellix modules. | Windows, Linux, and Mac. | Contact for quote |
| AT&T USM Anywhere | Yes | No | Remediation included | Windows, Linux, and Mac. | Starts at $1,075 per month |
SolarWinds: Best for log aggregation

SolarWinds Security Event Manager (SEM) is focused on log aggregation and threat detection. It can easily process and forward raw event log data to external applications for further analysis using syslog protocols, which is an area where it stands out from the competition.
Why I picked SolarWinds
I picked SolarWinds for its extensive log aggregation and log analysis functionality. This allows businesses to know the exact state of their devices, find the root-cause of each log, and consequently implement strategies to improve the same. SolarWinds’ ability to share massive amounts of log data with other applications is a significant plus as well.
Pricing
- SolarWinds annual SEM subscriptions start at $2,992.
- Perpetual licensing is available for around $6,168.
Features
- Automation to remediate some incidents.
- Export log data and share it with other teams or vendors.
- Dashboards indicate the state of security, and reports address compliance requirements.
- Pre-built connectors pull data from numerous sources.
- A file integrity checker tracks access and changes made to files and folders to detect unauthorized or malicious activity.
Integrations
- Amazon Web Services.
- Azure.
- Heroku.
- Apache.
- Oracle.
SolarWinds pros and cons
| Pros | Cons |
|---|---|
| Good for network-related events and analyzing per-host activities, such as logons, privilege usage, and registry alterations. | Dashboards can become cluttered and hard to understand when processing large amounts of data. |
| Security features include data encryption, single sign-on, and smart card authorization. | Can struggle with the complexity of very large enterprise environments. |
| Ability to restrict access from IPs, block applications, and deny access to removable media. | Automated does not provide a full range of remediation capabilities. |
Features
- Collect logs at petabyte scale.
- Rapidly access live data with sub-second latency.
- Fast search, real-time alerting, and customizable dashboards.
- Retain data as long as you need for compliance, threat hunting, and historical investigations.
Integrations
- AWS.
- Google Cloud.
- Azure.
- Red Hat.
- Other CrowStrike products.
CrowdStrike pros and cons
| Pros | Cons |
|---|---|
| Index-free architecture and compression technology minimize the computing and storage resources required to ingest and manage data. | Evolved from the XDR side, so is more of a log management tool with SIEM-like features than a full-featured SIEM suite. |
| Said to cut log management costs by up to 80% compared to alternative solutions. | |
| Strong remediation capabilities, courtesy of integration with the CrowdStrike Falcon platform. |
Splunk Enterprise Security: Best for cloud-native environment

Splunk Enterprise Security offers cloud-based security-related event notifications and log monitoring. It can identify resource bottlenecks, failing hardware, capacity issues, and other potential issues. As it evolved in the era of the cloud, it is particularly well suited to cloud-native environments.
Why I picked Splunk Enterprise Security
Splunk Enterprise Security got on this list for being specially equipped to protect cloud environments. It enables cloud-native organizations to easily establish security monitoring and unified visibility in the cloud. Its comprehensive visibility capabilities are coupled with 1,500+ detections, thousands of integrations, and risk-based alerting. Splunk’s unified threat detection, investigation, and response service is a security tool that many cloud-native companies should consider.
Pricing
- Splunk’s complex pricing structure is split into entity, activity, workload, and ingest categories.
- Splunk does not publish exact prices, but user reports place them anywhere from $173 per month up to $1,800 per GB.
Features
- Threat detection with machine learning, including 1,400 detections for frameworks such as MITRE and others.
- Ingest and monitor tens of terabytes of data per day from any source, structured or unstructured.
- Attribute risk to users and systems, map alerts to cybersecurity frameworks, and trigger alerts when risk exceeds thresholds.
- Investigate security events or suspicious activity rapidly.
Integrations
- AWS.
- Azure.
- Google Cloud Platform.
- Kubernetes.
- OpenShift.
- Kafka.
Splunk pros and cons
| Pros | Cons |
|---|---|
| Triggers that respond to logged situations with customized response patterns. | Some users consider Splunk to be expensive when monitoring large amounts of data in major enterprise environments. |
| Analytics capabilities are built in, which can produce long-term graphs. | The company’s recently announced acquisition by Cisco may lead to long integration delays and lack of progress on its innovation roadmap. |
| View a wide range of logs and drill down into specific times or data sources. | |
| Ability to solve problems across multiple platforms. |
Datadog Security Monitoring: Best for customization

Datadog has designed its platform to be highly customizable to user needs. Datadog Security Monitoring makes it relatively easy to see at a glance what’s happening with all sources being analyzed. It offers security monitoring for dynamic environments, real-time security monitoring tools, and root cause analysis functionality. There’s also a free trial that lets organization’s test drive Datadog to see if it fits their needs and requirements.
Why I picked Datadog Security Monitoring
I chose Datadog Security Monitoring for its strong emphasis on user-configuration and customizability. In particular, organizations can utilize Datadog’s configurable rules to track down common attacker behavior and techniques. You can also customize which logs you want to index as you continue to ingest and process data. This is on top of having a customizable dashboard and user interface.
Pricing
- The pro version costs $15 per host per month, and the enterprise version is $23 per host per month.
Features
- Over 350 detection rules and more than 500 integrations with log sources provide full visibility into security operations.
- Ability to see inside any stack or application at any scale and anywhere.
- Infrastructure monitoring, APM, log management, device monitoring, cloud workload monitoring, server monitoring, and database monitoring, all included.
- Assemble data from logs and other metrics to provide context and minimize incident response time.
Integrations
- Slack.
- SSH.
- AWS.
- Google Cloud Platform.
- Oracle.
- IBM Cloud.
Datadog pros and cons
| Pros | Cons |
|---|---|
| Datadog takes a monitoring approach geared toward analytics and is favored by DevOps and IT to address cloud and infrastructure performance. | Datadog stops short of calling itself a complete SIEM platform, as it is more focused on cloud monitoring and security but has been expanding its cloud SIEM capabilities. |
| Datadog installation is straightforward, courtesy of agent deployment. | Datadog lacks some of the log monitoring capabilities of full-featured SIEM platforms. |
| Dashboards and interfaces are easy to customize. |
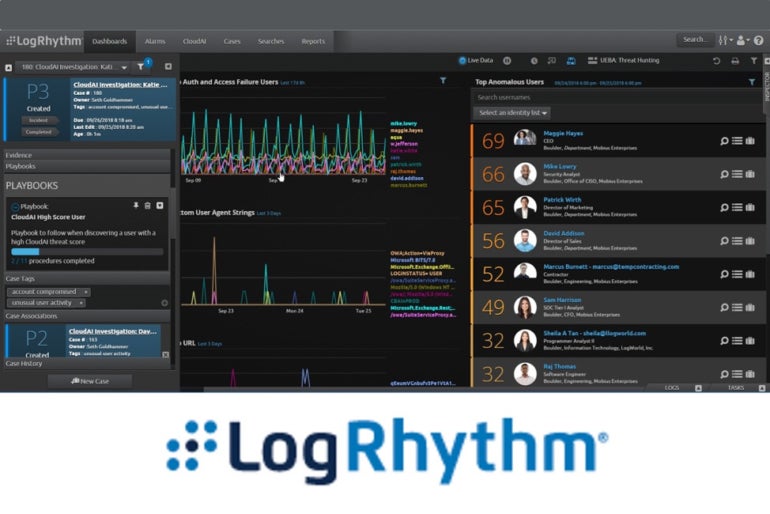
LogRhythm SIEM: Best for on-premises

LogRhythm’s SIEM software is designed to be hosted on-premises. It has built AI and automation features into its platform. Reporting based on queries is easy to configure. The system integrates well with an array of security and technological solutions.
SEE: The SIEM Buyer’s Guide (TechRepublic)
Why I picked LogRhythm SIEM
For organizations requiring an on-prem solution, I recommend LogRhythm. You get a holistic security approach, getting features such as embedded modules, threat monitoring, and automated detection and response. It also provides streamlined incident investigation and analysis capabilities for organizations looking for a bird’s-eye-view of their IT infrastructure. For on-premises deployments, LogRhythm also emphasizes providing highly-usable content for compliance and regulatory requirements.
Pricing
- Contact for curated pricing.
- A variety of pricing options are available, such as perpetual or subscription software licenses, an unlimited data plan and a high-performance plan.
Features
- Heightens the detection of security and potential threats.
- LogRhythm provides an integrated user experience.
- Combines enterprise log management, security analytics, user entity and behavioral analytics (UEBA), network traffic and behavioral analytics (NTBA), and security automation and orchestration.
- As well as an on-prem version, it also offers a cloud-based SIEM.
Integrations
- Kibana.
- Trend Micro.
- Rapid7.
- Acronis.
- CimTrak.
- CloudSEK.
LogRythm pros and cons
| Pros | Cons |
|---|---|
| Built on a machine analytics/data lake technology foundation that’s designed to scale easily. | Large upfront investment often needed for the on-prem version. |
| Open platform allows for integration with enterprise security and IT infrastructure. | |
| Embedded modules, dashboards, and rules deliver threat monitoring, threat hunting, threat investigation, and incident response. | |
| Integration with many third-party platforms. | |
| User comments are favorable about the speed and responsiveness of the support team. |
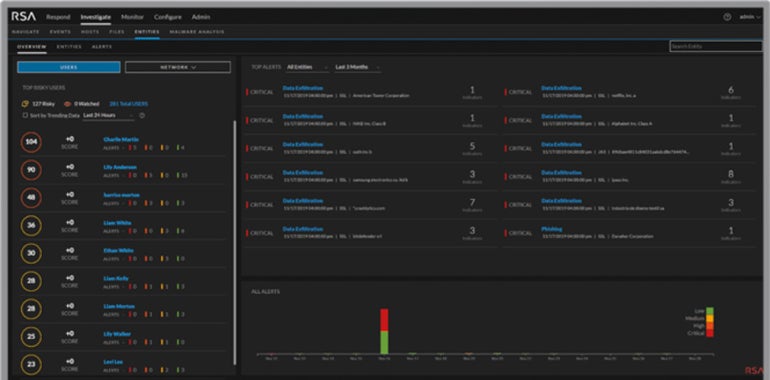
RSA NetWitness: Best for large enterprises

RSA, well known for its multifactor soft and hard token authentication products, has a strong footprint in the overall security community. Its NetWitness SIEM is geared more toward large businesses, with versions that work both on-premises and via cloud.
SEE: Top 8 Advanced Threat Protection Tools and Software Options for 2024 (TechRepublic)
Why I picked RSA NetWitness
RSA NetWitness carved its name on this list for being an all-around security solution built for bigger organizations. It provides visibility across a wide range of capture points, as well as having smart analytics and automation capabilities for both known and unknown attacks. I find that large businesses, in particular, will benefit from NetWitness’ fast-performing threat detection — which is able to reveal the full attack scope in a timely manner.
Pricing
- Contact for curated pricing.
Features
- NetWitness monitors for actionable events.
- Behavior analytics observe hacker activity and recreate full sessions to observe the precise anatomy of an attack.
- Intelligence feeds based on customizable information track and remain key operations.
- Visibility into log data spread across the IT environment.
Integrations
- Azure.
- AWS.
- Cisco.
- Google Cloud Platform.
- Symantec Endpoint Protection.
- Kaspersky CyberTrace.
RSA NetWitness pros and cons
| Pros | Cons |
|---|---|
| Simplifies threat detection, reduces dwell time, and supports compliance. | The learning curve and implementation efforts can be steep. |
| Centralized log management and log monitoring for logs generated by public clouds and SaaS applications. | Some users require a large amount of rack space. |
| Identification of suspicious activity that evades signature-based security tools. |
ManageEngine Log360: Best for small businesses

ManageEngine Log360 is a SIEM that serves businesses of all sizes but is especially suited to small business (SMBs) deployments. It also integrates well with a series of other security and monitoring products that the company offers.
Why I picked ManageEngine Log360
ManageEngine Log 360 is on this list for being especially useful to SMBs. It has all the SIEM features SMBs will benefit from, such as event log analysis and cloud infrastructure monitoring, as well as threat detection and automated responses. I particularly like how ManageEngine makes it very accessible for businesses to try Log360’s premium features for free — via a generous 30-day free trial.
Pricing
- Answer ManageEngine’s online form to get a personalized quote.
Features
- Detect internal threats, such as data exfiltration and user account compromise, by recognizing subtle changes in user activity.
- Identify suspicious or blacklisted IPs, URLs, and domains intruding into your network by correlating your log data with reputed threat feeds.
- Automate responses to events with configurable workflows.
- Monitor active VPN connections and receive alerts on unusual VPN activities and VPN access from malicious sources.

Integrations
- AWS.
- Azure.
- Salesforce.
- Google Cloud.
- ESET Antivirus.
- Cisco.
ManageEngine Log360 pros and cons
| Pros | Cons |
|---|---|
| Migrate SharePoint environments to Microsoft 365 by selecting the required SharePoint site users, groups, and permission levels. | Some users complain of poor support. |
| Audit changes in Active Directory infrastructure and Azure AD in real-time. | May struggle to scale well enough in large, complex environments. |
| Discover and classify sensitive files, audit users’ file activities, and analyze file permissions. | |
| Detect, disrupt, and prevent sensitive data leaks via endpoints, like USBs and printers, email, and web applications with real-time security monitoring. |
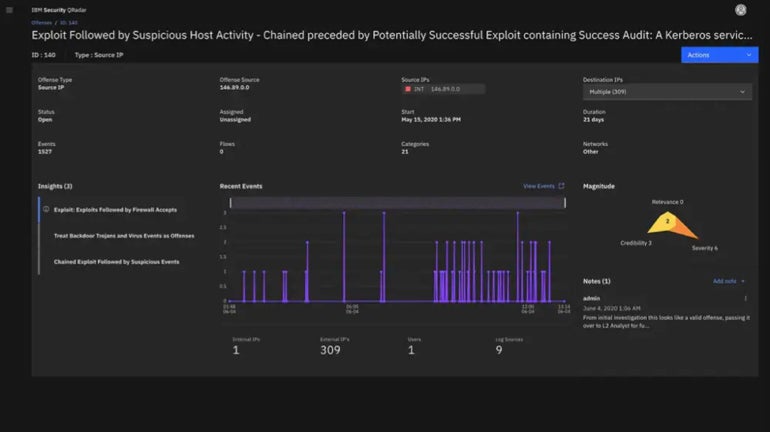
IBM Security QRadar SIEM: Best for IBM shops

IBM QRadar is a threat detection and response solution that includes a SIEM module. As such, IBM Security QRadar SIEM is especially suited to enterprises that are heavily invested in IBM tools and systems, as well as large enterprise deployments.
Why I picked IBM Security QRadar SIEM
I picked IBM’s QRadar SIEM as a smart choice for companies that have already heavily integrated IBM products and tools into their workflow. Fortunately, Security QRadar also offers a good number of integrations with other third-party services — making it a viable SIEM option even for companies that don’t have an IBM ecosystem.
Pricing
- Visit IBM’s official online price estimator to get a personalized quote.
Features
- Accelerated threat response by dashboards that highlight alerts that matter.
- Uses near real-time analytics to intelligently investigate and prioritize high-fidelity alerts based on severity of risk.
- Identifies insider threats and risky user behavior.
- Part of IBM Cloud Pak for Security which uses AI to provide risk assessments as well as analytics.
Integrations
- AWS.
- Check Point.
- Google Cloud.
- Palo Alto Networks.
- Trend Micro.
- Carbon Black (VMware).
IBM Security QRadar pros and cons
| Pros | Cons |
|---|---|
| Machine learning-based analytics to identify anomalies as potential threat actors. | Lack of integration with other SIEM tools. |
| QRadar SIEM augments traditional log data by monitoring key network flow data. | Those not using IBM platforms may find it difficult to deploy. |
Trellix Security Operations and Analytics: Best for Windows shops

Trellix Security Operations (SecOps) and Analytics contains the bones of the old McAfee Enterprise Security Manager SIEM platform and is now a module known as Trellix Enterprise Security Manager. That SIEM offering was Active Directory-based and well-suited to Windows environments. But Trellix has expanded it to offer strong cloud support.
Why I picked Trellix Security Operations and Analytics
I have Trellix Security Operations and Analytics on this list for its strong compatibility with Windows machines, making it a good choice for businesses that primarily run a Windows-centric environment. Aside from that, it provides powerful automation capabilities for fast detection and remediation. Ideally, this would lead to lower risk exposure and faster response times when dealing with threats.
Pricing
- Contact Trellix for curated pricing.
Features
- The Trellix Helix SecOps platform is part of a suite that includes SIEM to help IT take control from incident to detection to response.
- Trellix Insights provides threat intelligence to predict and prioritize threats and prescribe countermeasures.
- Trellix ePO security management platform helps IT control and administer all endpoints from a single console.
Integrations
- Trellix Endpoint Detection and Response.
- Trelix Helix.
- Trelix Insights.
- Cisco.
Trellix Security Operations and Analytics pros and cons
| Pros | Cons |
|---|---|
| A central view of potential threats with built-in workflows removes complexity. | The full Trellix suite is needed to provide complete remediation capabilities. |
| Get greater transparency monitoring users, applications, networks, and devices. | Some users complain that it can be slow to respond. |
| Real-time threat identification and response reduces lead time to protect against threats. | |
| Can integrate products from 650+ third-party vendors. |
AT&T USM Anywhere: Best for asset discovery

AlienVault Unified Security Management platform (USM) is now AT&T USM Anywhere. It discovers assets and gathers data about running services, users, operating systems, and hardware information. This asset focus means it can pick up any devices in the environment that it protects.
Why I picked AT&T USM Anywhere
USM Anywhere got its place on this list as a solid tool for businesses that prioritize threat detection and asset discovery above all else. It can detect vulnerabilities and threats on the cloud, the network, or on-prem — making it a virtual detection solution for all types of IT infrastructures.
Pricing
- Essentials – $1,075 per month; tailored for small IT teams as a security and compliance tool.
- Standard – $1,695 per month; catered towards IT security teams that require automation and deep security analysis.
- Premium – $2,595 per month; geared towards IT security teams whose goal is to meet PCI DSS audit requirements.
- You may also answer USM Anywhere’s online form to get a personalized quotation.
Features
- Automatically collects and analyzes data across the attack surface.
- Threat intelligence provided by AT&T Alien Labs.
- Supports an ecosystem of AlienApps to orchestrate and automate actions towards other security technologies and respond to incidents.

Integrations
- AWS.
- Azure.
- Cisco.
- GCP.
Trellix Security Operations and Analytics pros and cons
| Pros | Cons |
|---|---|
| Good for those who want their cybersecurity and SIEM services managed by someone else. | Not suitable for organizations that need to maintain tight control over their own assets for sensitivity or compliance reasons. |
Key features of SIEM software
All SIEM software tools take care of log monitoring and management. Further important features include whether the tool is cloud-based, whether it can be hosted on-prem, whether it includes remediation capabilities, and what platforms it runs on.
Cloud
These days, most SIEM software is based in the cloud. Cloud-based products are easier to deploy, easier to manage, and simpler to run. And with so many enterprises operating in one or more clouds, SIEM tools in the cloud are a must-have. Some vendors provide SIEM on a Software-as-a-Service (SaaS) basis, and others offer it as a fully managed service.
Hosted On-prem
Some enterprises are averse to operating in the cloud due to privacy, security, or compliance reasons. They need to load SIEM on their own internal servers. Some vendors offer this option, while others don’t.
Remediation
SIEM originated as a way to simplify the compilation and analysis of security logs. It provided enterprises with a way to evaluate huge numbers of log entries and alerts and detect potential issues or intrusions. More recently, however, SIEM platforms have begun to add remediation capabilities. Some offer ways to automate a limited number of remediation actions. But a few tools provide access to a wide range of security remediations, either within the SIEM itself or via integrated or associated tools provided by the same vendor.
SEE: Everything You Need to Know about the Malvertising Cybersecurity Threat (TechRepublic Premium)
Platforms
The SIEM market is highly competitive. Most vendors have to provide tools that operate on all major operating systems and cloud environments. But there can be a few holes. Those with an extensive Google Chrome presence, for example, may find their SIEM options limited. It is vital, therefore, to verify that your potential vendor of choice is fully set up to run their systems in your environment.
How do I choose the best SIEM software for my business?
Every one of the products outlined here offers quality security protection and would be of value to any organization — and every organization needs some level of log-based real-time security analysis to help prevent and detect threats.
Making the right choice when selecting SIEM software is going to depend on company priorities, requirements, budget, level of IT expertise, and level of IT availability to assess and handle threats. If money is no object and tech staff isn’t able or willing to roll up its sleeves and tackle security risks, a managed SIEM like USM Anywhere may be the way to go. If company budgets are less robust and in-house talent and time are copious, SolarWinds SEM, Datadog, or AlienVault would be among the candidates. Otherwise, options such as LogRhythm, CrowdSrike, Splunk, RSA, IBM QRadar and ManageEngine should be high on the list of those to consider.
Methodology
The SIEM tools I covered here were selected based on an extensive evaluation of official security feature inclusions, prominence in analysis reports, and real-world user reviews. Each SIEM solution was analyzed based on its pros and cons, security features, and price offerings.
In addition, a heavy emphasis was placed on how each SIEM tool could be of use to certain use cases and businesses. This takes into account specializations per product and what types of organizations can best maximize their feature set.
Finally, the variety and number of integrations with third-party security services were also considered for this shortlist. This is to ensure the smooth adoption of the SIEM solution within a business’ existing architecture and the seamless monitoring of data points across the organization’s IT infrastructure for the SIEM itself.
Also Read
- Midnight Blizzard Escalates Spear-Phishing Attacks On Over 100 Organizations
- What is a Passkey? Definition, How It Works and More
- Operation Magnus: Joint Law Enforcement Operation Targets Major Infostealer Networks
- Best Antivirus Software for Small Businesses in 2024
- Cybersecurity: More must-read coverage

Drew Robb
Originally from Scotland, Drew Robb has been a full-time freelance writer for 25 years. He lives in Florida and specializes in IT, engineering, and business. As well as TechRepublic, he writes for a wide range of magazines including Gas Turbine World, SDxCentral, HR Magazine, and eWeek.
Original Post URL: https://www.techrepublic.com/article/siem-tools/
Category & Tags: Cloud Security,Security,Top Products,best siem tools,crowdstrike,SIEM tools – Cloud Security,Security,Top Products,best siem tools,crowdstrike,SIEM tools
Views: 16




















































