Source: securityboulevard.com – Author: SafeBreach As the pioneer in breach and attack simulation (BAS), SafeBreach launched the industry’s first continuous security validation platform in 2014. Since...
Author: SafeBreach
Discovering Unknown Problems in the Alert Pipeline – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Financial services institutions (FSIs) have become an increasingly common target for malicious actors. According to Boston Consulting Group, FSIs are 300...
Do we really need another cybersecurity tool? – Source: securityboulevard.com
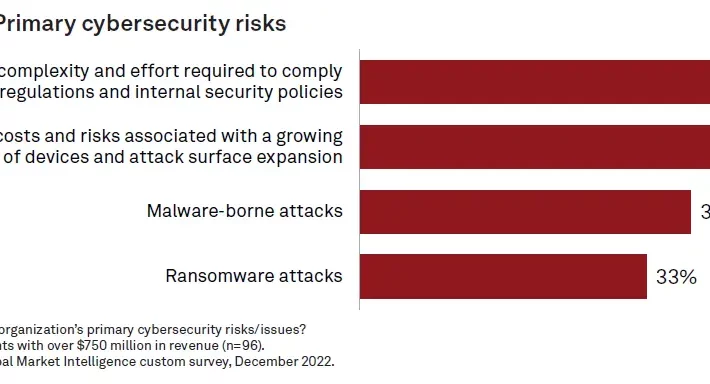
Source: securityboulevard.com – Author: SafeBreach Research shows many companies now own and operate more than 60 disparate security tools, yet breaches continue to make headlines. Throwing...
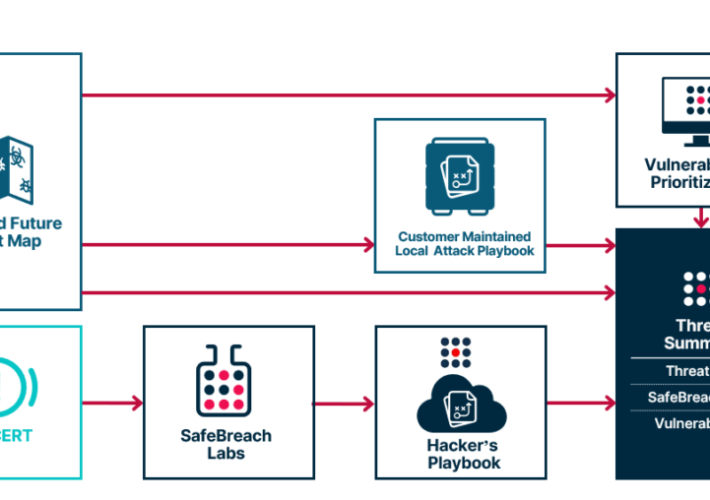
SafeBreach and Recorded Future: Operationalizing Threat Intelligence with Breach and Attack Simulation – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Modern enterprises have adopted more offensive measures to protect their organizations from evolving cyber threats. As a result, many security teams...
MITRE ATT&CK® and BAS: Getting Started with the MITRE ATT&CK® Framework and SafeBreach – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Cybersecurity programs have shifted from building impenetrable fortresses to protect networks to a proactive, threat-informed strategy. This approach is not only...
Demystifying Security Validation Technologies: What You Need to Know About Automated Pen Testing – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach You can’t predict the future, but you can prepare for it. When it comes to IT (and OT), security validation is...