New Money Message ransomware demands million dollar ransomsA new ransomware gang named 'Money Message' has appeared, targeting victims worldwide and demanding million-dollar ransoms not to leak...
Author:
Is ChatGPT A Silver Bullet For Cybercriminals?
Is ChatGPT A Silver Bullet For Cybercriminals?Post ContentRead MoreProofpoint News Feed
New IcedID variants shift from bank fraud to malware delivery
New IcedID variants shift from bank fraud to malware deliveryPost ContentRead MoreProofpoint News Feed
Pro-Russian hackers target elected US officials supporting Ukraine
Pro-Russian hackers target elected US officials supporting UkrainePost ContentRead MoreProofpoint News Feed
Think ransomware gangs won’t thrive this year? Think again, experts say
Think ransomware gangs won't thrive this year? Think again, experts sayPost ContentRead MoreProofpoint News Feed
Cisco Secure Network Analytics Remote Code Execution Vulnerability
Cisco Secure Network Analytics Remote Code Execution VulnerabilityA vulnerability in the web-based management interface of Cisco Secure Network Analytics, formerly Cisco Stealthwatch Enterprise, could allow an...
Cisco Application Policy Infrastructure Controller and Cisco Cloud Network Controller Cross-Site Request Forgery Vulnerability
Cisco Application Policy Infrastructure Controller and Cisco Cloud Network Controller Cross-Site Request Forgery VulnerabilityA vulnerability in the web-based management interface of Cisco Application Policy Infrastructure Controller...
Embedded vSphere Harbor default enablement results in an insecure configuration
Embedded vSphere Harbor default enablement results in an insecure configurationThis post is relevant to administrators that have enabled the embedded Harbor version in vSphere 7.0 or...
Investigating 3CX Desktop Application Attacks: What You Need to Know
Investigating 3CX Desktop Application Attacks: What You Need to KnowThis is a developing situation and this blog post will be updated as needed. Reports of malicious...
New IcedID variants shift from bank fraud to malware delivery
New IcedID variants shift from bank fraud to malware deliveryPost ContentRead MoreProofpoint News Feed
North Korean Lazarus Group Linked to 3CX Supply Chain Hack
North Korean Lazarus Group Linked to 3CX Supply Chain HackTools, Code Used to Hack 3CX Desktop Confirm Cyberespionage Group's InvolvementSecurity researchers have uncovered more evidence that...
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major AppsMicrosoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access...
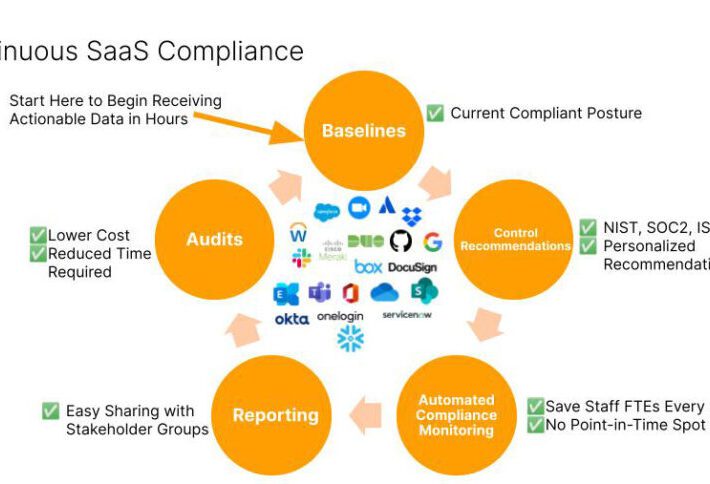
Reducing Risks and Threats with Continuous SaaS Compliance
Reducing Risks and Threats with Continuous SaaS ComplianceCISOs and GRC officers are quickly recognizing the growing threats posed by misconfigured SaaS applications and integrations between SaaS...
3CX Supply Chain Attack Campaign
3CX Supply Chain Attack CampaignOn March 29th 2023, CrowdStrike published a blog outlining a supply chain attack leveraging the 3CXDesktopApp - a softphone application from 3CX....
What is the impact of AI on cyber security awareness?
What is the impact of AI on cyber security awareness?The post What is the impact of AI on cyber security awareness? appeared first on Click Armor....
Ukrainian cops nab suspects accused of stealing $4.3m from victims across Europe
Ukrainian cops nab suspects accused of stealing $4.3m from victims across EuropeIf the price looks too good to be true, it probably is Ukrainian cops have...
Avoiding data backup failures – Week in security with Tony Anscombe
Avoiding data backup failures – Week in security with Tony AnscombeToday is World Backup Day, but maybe we also need a "did you test your backups"...
DISH slapped with multiple lawsuits after ransomware cyber attack
DISH slapped with multiple lawsuits after ransomware cyber attackDish Network has been slapped with multiple class action lawsuits after it suffered a ransomware incident that was behind...
Fake ransomware gang targets U.S. orgs with empty data leak threats
Fake ransomware gang targets U.S. orgs with empty data leak threatsFake extortionists are piggybacking on data breaches and ransomware incidents, threatening U.S. companies with publishing or...
3CX Supply Chain Attack — Here’s What We Know So Far
3CX Supply Chain Attack — Here's What We Know So FarEnterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for...
Deep Dive Into 6 Key Steps to Accelerate Your Incident Response
Deep Dive Into 6 Key Steps to Accelerate Your Incident ResponseOrganizations rely on Incident response to ensure they are immediately aware of security incidents, allowing for quick action...
Cyber Police of Ukraine Busted Phishing Gang Responsible for $4.33 Million Scam
Cyber Police of Ukraine Busted Phishing Gang Responsible for $4.33 Million ScamThe Cyber Police of Ukraine, in collaboration with law enforcement officials from Czechia, has arrested...
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerability
Winter Vivern APT Targets European Government Entities with Zimbra VulnerabilityThe advanced persistent threat (APT) actor known as Winter Vivern is now targeting officials in Europe and...
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website...
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active ExploitationCritical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors...
World Backup Day is here again – 5 tips to keep your precious data safe
World Backup Day is here again – 5 tips to keep your precious data safeThe only backup you will ever regret is the one you didn't...
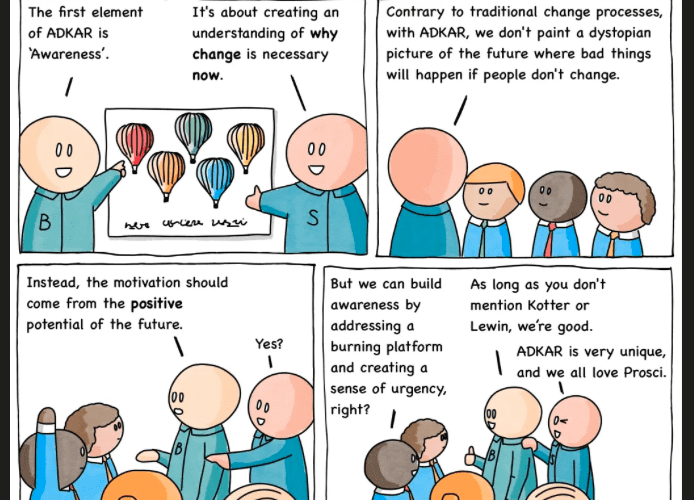
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #233 — Burning Platform
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #233 — Burning Platform via the respected Software Engineering expertise of Mikkel Noe-Nygaard as well as the lauded...
Post-Conference Tech Spec: Why Building Your Ship (Application) with Raw Materials is a Bad Idea
Post-Conference Tech Spec: Why Building Your Ship (Application) with Raw Materials is a Bad Idea The post Post-Conference Tech Spec: Why Building Your Ship (Application)...
Challenges of Securing the Modern Workforce
Challenges of Securing the Modern WorkforceAs the world continues to evolve and adopt new technologies, the modern workforce has changed significantly, and so have the opportunities...
German Police Raid DDoS-Friendly Host ‘FlyHosting’
German Police Raid DDoS-Friendly Host ‘FlyHosting’Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web service that catered to cybercriminals operating DDoS-for-hire...