Source: www.techrepublic.com – Author: Karl Greenberg Image: Timon/Adobe Stock In its 2023 Mid-Year Cyber Security Report, Check Point Software spotlighted numerous exploits so far this year,...
Author:
Microsoft, Apple versus China, spyware actors – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: 2ragon/Adobe Stock Revelations this week from Microsoft and Apple speak to the COVID-like persistence of cyber threats and the...
Cisco: Booming identity market driven by leadership awareness – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: leowolfert 85% of IT decision-makers are prioritizing identity and access management investments more highly than other security solutions. This...
Patch ‘Em or Weep: Study Reveals Most Vulnerable IoT, Connected Assets – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on September 7, 2023, 2:36 PM EDT Patch ‘Em or Weep: Study Reveals Most Vulnerable IoT, Connected Assets Phones, tablets...
FBI-Led Global Effort Takes Down Massive Qakbot Botnet – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Whatawin/Adobe Stock A multinational action called Operation “Duck Hunt” — led by the FBI, the Department of Justice, the...
Google Applies Generative AI Tools to Cloud Security – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Bilal Ulker At its Google Next ’23 event this week, Google revealed how — with the use of its...
Abnormal Security: Microsoft Tops List of Most-Impersonated Brands in Phishing Exploits – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Timon/Adobe Stock A significant portion of social engineering attacks, such as phishing, involve cloaking a metaphorical wolf in sheep’s...
Google AI in Workspace Adds New Zero-Trust and Digital Sovereignty Controls – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Urupong/Adobe Stock At a Google Cloud press event on Tuesday, the company announced Google Cloud’s rollout over the course...
Critical Insight Reports Fewer Cybersecurity Breaches in Health Care, Yet Victim Numbers Are Up in 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on August 24, 2023, 9:12 AM EDT Critical Insight Reports Fewer Cybersecurity Breaches in Health Care, Yet Victim Numbers Are...
Generative AI: Cybersecurity Weapon, But Not Without Adaptable, Creative (Human) Thinkers – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: PB Studio Photo/Adobe Stock Generative AI was — not surprisingly — the conversational coin of the realm at Black...
Akamai Report: LockBit, Cl0P Expand Ransomware Efforts – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Adobe Stock/Jimon Akamai’s ransomware report released at Black Hat 2023 revealed that exploitation of zero-day and one-day vulnerabilities has...
At Black Hat, Splunk, AWS, IBM Security and Others Launch Open Source Cybersecurity Framework – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Adobe Stock/Scanrail At a restaurant where the waiters, chefs and cooks speak the same language but use different words...
Black Hat USA 2023 Panel: Used Correctly, Generative AI is a Boon for Cybersecurity – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Adobe stock, by Busra At the Black Hat kickoff keynote on Wednesday, Jeff Moss (AKA Dark Tangent), the founder of...
CrowdStrike at BlackHat: Speed, Interaction, Sophistication of Threat Actors Rising in 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on August 10, 2023, 6:57 PM EDT CrowdStrike at BlackHat: Speed, Interaction, Sophistication of Threat Actors Rising in 2023 As...
Research Eyes Misconfiguration Issues At Google, Amazon and Microsoft Cloud – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on August 7, 2023, 2:43 PM EDT Research Eyes Misconfiguration Issues At Google, Amazon and Microsoft Cloud Qualys report looks...
Cisco Announces General Availability of XDR Platform – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg In alliance with Cohesity and others, Cisco is fueling near-zero latency between ransomware detection and remediation with its Extended Detection...
Hardware-bound passkeys are still ultimate in security: Yubico VP – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg YubiKey 5 Series multi-protocol hardware authentication device. (Image: Yubico) Derek Hanson, an expert on hardware-bound and syncable passkeys, works very...
Akamai Survey: API-Specific Controls are Lacking – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Phishing, misconfigurations and missing patches are top concerns among security leaders, but they also say their organizations are letting observability...
Armis, Honeywell Uncover Vulnerabilities in Honeywell Systems – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Newly discovered vulnerabilities in distributed control systems could allow attackers access to systems supporting industrial, energy, chemical and other operations....
White House Launches Cybersecurity Implementation Plan – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Maksym Yemelyanov/Adobe Stock U.S. President Biden’s administration this week released the first iteration of the National Cybersecurity Strategy Implementation...
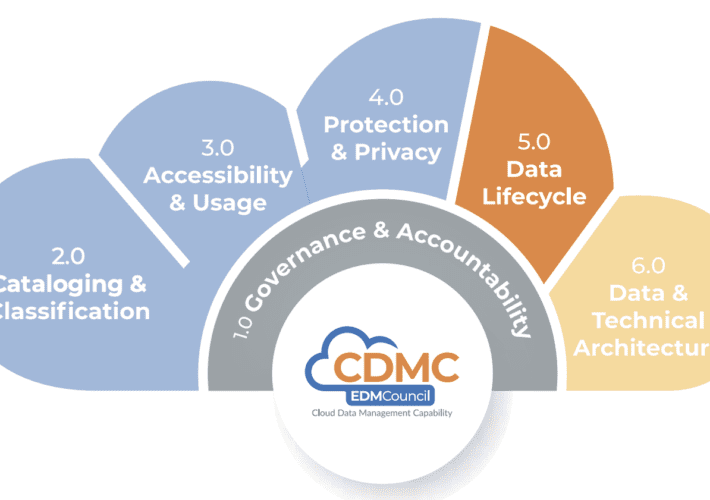
EDM Council Survey: Management of Cloud Data Deployment is Lacking – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on July 7, 2023, 2:50 PM EDT EDM Council Survey: Management of Cloud Data Deployment is Lacking The Council’s first...
Thales: For Data Breaches, Cloud Assets are Biggest Cybersecurity Headache – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on July 5, 2023, 5:29 PM EDT Thales: For Data Breaches, Cloud Assets are Biggest Cybersecurity Headache Thales cloud security...
Gigamon’s Cloud Security Report Shares Insights on Undetected Breaches & Deep Observability – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: UnderhilStudio/Shutterstock Findings in network intelligence firm Gigamon’s Hybrid Cloud Security Survey report suggest there’s a disconnect between perception and...
Aqua Security Study Finds 1,400% Increase in Memory Attacks – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on June 30, 2023, 12:29 PM EDT Aqua Security Study Finds 1,400% Increase in Memory Attacks Analysis of 700,000 real-world...
How FIDO2 Powers Up Passkeys Across Devices – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: tete_escape/Adobe Stock When the FIDO Alliance (Fast Identity Online) holds its virtual Authenticate Virtual Summit on passkeys event this...
Anonymous Sudan’s Attack of European Investment Bank: Money, Politics and PR – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Adobe Stock/Sandsun Last week, Anonymous Sudan, identified by Flashpoint and others as a Russia-aligned threat actor spoofing an Islamicist...
Okta moves passkeys to cloud, allowing multi-device authentication – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Okta’s formula for multi-device identity authentication for a hybrid workforce: extract passwords, add ease of passkeys across devices. Amid an...
AI vs AI: Next front in phishing wars – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Business email compromises, which supplanted ransomware last year to become the top financially motivated attack vector-threatening organizations, are likely to...
Akamai’s new study: Bots, phishing and server attacks making commerce a cybersecurity hotspot – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg The study shows attackers are using more bots and doing more sophisticated phishing exploits and server attacks, especially targeting retail....
CISA advisory on LockBit: $91 million extorted from 1,700 attacks since 2020 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: darkfoxelixir/Adobe Stock A new advisory from a consortium of international organizations, including the Cybersecurity and Infrastructure Security Agency, the...