Source: www.bleepingcomputer.com – Author: Bill Toulas LastPass is warning that a fake copy of its app is being distributed on the Apple App Store, likely used...
Author: CISO2CISO Editor 2
Data breaches at Viamedis and Almerys impact 33 million in France – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Data breaches at two French healthcare payment service providers, Viamedis and Almerys, have now been determined to impact over 33...
Google teases a new modern look for sign-in pages, including Gmail – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google is on the brink of refreshing its sign-in pages, including Gmail, with a sleek, modern makeover. BleepingComputer spotted a ...
Fortinet warns of new FortiSIEM RCE bugs in confusing disclosure – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Fortinet is warning of two new unpatched patch bypasses for a critical remote code execution vulnerability in FortiSIEM, Fortinet’s SIEM...
Facebook ads push new Ov3r_Stealer password-stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new password-stealing malware named Ov3r_Stealer is spreading through fake job advertisements on Facebook, aiming to steal account credentials and...
Denmark orders schools to stop sending student data to Google – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Danish data protection authority (Datatilsynet) has issued an injunction regarding student data being funneled to Google through the use...
Coyote: A multi-stage banking Trojan abusing the Squirrel installer – Source: securelist.com
Source: securelist.com – Author: GReAT The developers of banking Trojan malware are constantly looking for inventive ways to distribute theirs implants and infect victims. In a...
Chinese Hackers Operate Undetected in U.S. Critical Infrastructure for Half a Decade – Source:thehackernews.com
Source: thehackernews.com – Author: . The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical...
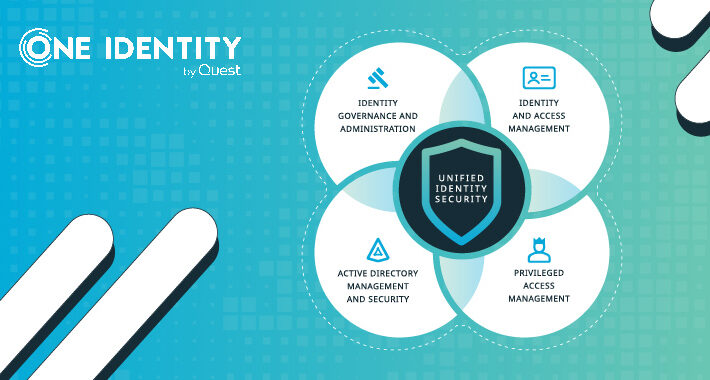
Unified Identity – look for the meaning behind the hype! – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 08, 2024The Hacker NewsUnified Identity / Cyber Security If you’ve listened to software vendors in the identity space lately, you...
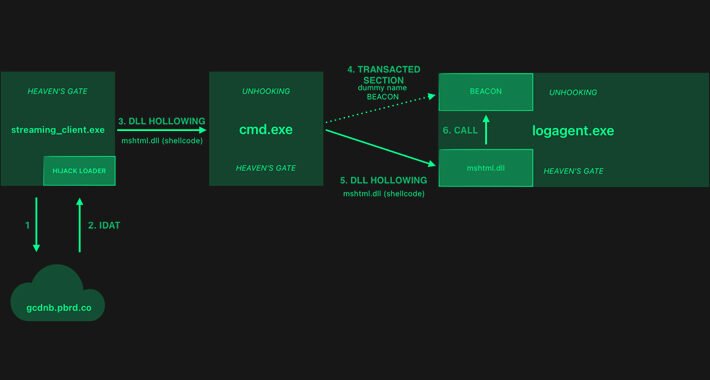
HijackLoader Evolves: Researchers Decode the Latest Evasion Methods – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 08, 2024NewsroomEndpoint Security / Cyber Threat The threat actors behind a loader malware called HijackLoader have added new techniques for...
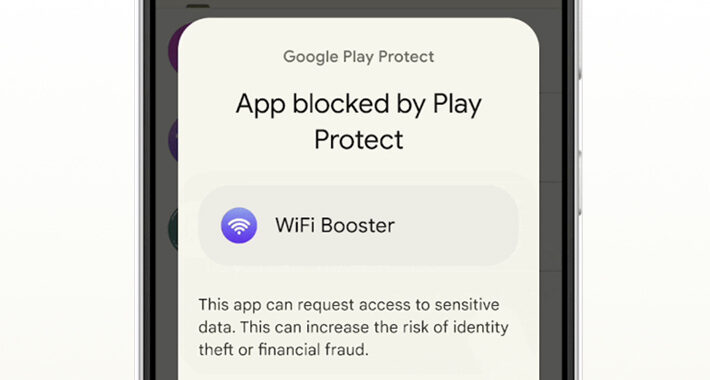
Google Starts Blocking Sideloading of Potentially Dangerous Android Apps in Singapore – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 08, 2024NewsroomData Protection / Mobile Securit Google has unveiled a new pilot program in Singapore that aims to prevent users...
Kimsuky’s New Golang Stealer ‘Troll’ and ‘GoBear’ Backdoor Target South Korea – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 08, 2024NewsroomCyber Espionage / Malware The North Korea-linked nation-state actor known as Kimsuky is suspected of using a previously undocumented...
Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 08, 2024NewsroomCyber Threat / Network Security Cisco, Fortinet, and VMware have released security fixes for multiple security vulnerabilities, including critical...
After FBI Takedown, KV-Botnet Operators Shift Tactics in Attempt to Bounce Back – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actors behind the KV-botnet made “behavioral changes” to the malicious network as U.S. law enforcement began issuing commands to...
Critical Boot Loader Vulnerability in Shim Impacts Nearly All Linux Distros – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024NewsroomDevice Security / Vulnerability The maintainers of shim have released version 15.8 to address six security flaws, including a...
New Webinar: 5 Steps to vCISO Success for MSPs and MSSPs – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024The Hacker NewsRisk Management / Cybersecurity 2024 will be the year of the vCISO. An incredible 45% of MSPs...
Global Coalition and Tech Giants Unite Against Commercial Spyware Abuse – Source:thehackernews.com
Source: thehackernews.com – Author: . A coalition of dozens of countries, including France, the U.K., and the U.S., along with tech companies such as Google, MDSec,...
Chinese Hackers Exploited FortiGate Flaw to Breach Dutch Military Network – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024NewsroomCyber Espionage / Network Security Chinese state-backed hackers broke into a computer network that’s used by the Dutch armed...
Critical JetBrains TeamCity On-Premises Flaw Exposes Servers to Takeover – Patch Now – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024NewsroomCybersecurity / Software Security JetBrains is alerting customers of a critical security flaw in its TeamCity On-Premises continuous integration...
Experts Detail New Flaws in Azure HDInsight Spark, Kafka, and Hadoop Services – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomVulnerability / Cloud Security Three new security vulnerabilities have been discovered in Azure HDInsight’s Apache Hadoop, Kafka, and Spark...
How a $10B Enterprise Customer Drastically Increased their SaaS Security Posture with 201% ROI by Using SSPM – Source:thehackernews.com
Source: thehackernews.com – Author: . SaaS applications are the darlings of the software world. They enable work from anywhere, facilitate collaboration, and offer a cost-effective alternative...
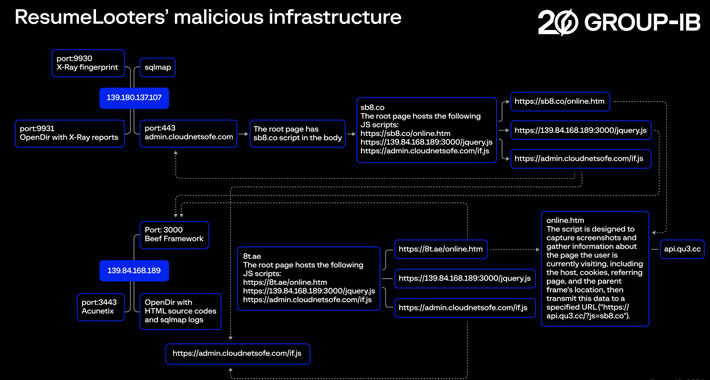
Hackers Exploit Job Boards, Stealing Millions of Resumes and Personal Data – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomDark Web / Cybercrime Employment agencies and retail companies chiefly located in the Asia-Pacific (APAC) region have been targeted...
Free & Downloadable Cybersecurity Incident Response Plan Templates – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal An effective cybersecurity incident response plan (IRP) can be the difference between a minor disruption and a major crisis. This...
Free & Downloadable Cybersecurity Risk Assessment Templates – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal Securing digital assets has never been more critical. This guide offers direct access to indispensable cybersecurity risk assessment templates in...
CISA adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 07, 2024 U.S....
Fortinet addressed two critical FortiSIEM vulnerabilities – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Fortinet addressed two critical FortiSIEM vulnerabilities Pierluigi Paganini February 07, 2024 Fortinet warns of two critical OS command injection vulnerabilities...
Experts warn of a critical bug in JetBrains TeamCity On-Premises – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of a critical bug in JetBrains TeamCity On-Premises Pierluigi Paganini February 07, 2024 A new vulnerability in JetBrains...
Critical shim bug impacts every Linux boot loader signed in the past decade – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Critical shim bug impacts every Linux boot loader signed in the past decade Pierluigi Paganini February 07, 2024 The maintainers...
China-linked APT deployed malware in a network of the Dutch Ministry of Defence – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini China-linked APT deployed malware in a network of the Dutch Ministry of Defence Pierluigi Paganini February 07, 2024 China-linked APT group breached the Dutch...
Commercial spyware vendors are behind most zero-day exploits discovered by Google TAG – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Commercial spyware vendors are behind most zero-day exploits discovered by Google TAG Pierluigi Paganini February 06, 2024 Google’s TAG revealed...