The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Author: Constanza Rodriguez
Cybersecurity Program Template A resource to help individual licensees and individually owned businesses develop a cybersecurity program as required by New York State’s Cybersecurity Regulation 23 NYCRR Part 500
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity_Political_Organisations_Election_Candidates
Political organisations and election candidates have become targets for threat actors that wish to disrupt and interfere in the democratic process. This can be part of...
Cyber Technology Practice Playbook Part I: Common Adversary Attacks – A practical guide for executives to navigate best practices in cyber risk management
Standardized guidelines & best practices THE NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY (NIST) CREATED A VOLUNTARY FRAMEWORK consisting of standard guidelines and best practices to address...
Cyber Security on Azure An IT Professional’s Guide to Microsoft Azure Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security Monitoring and Logging Guide
This Guide presents details about how to monitor and log cyber security events, some of which are potential indicatorsof compromise (IOC) that can lead to cyber...
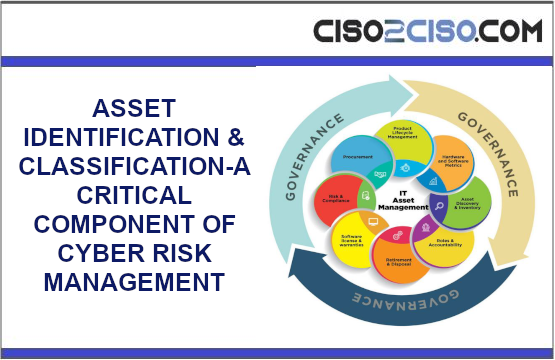
ASSET IDENTIFICATION & CLASSIFICATION-A CRITICAL COMPONENT OF CYBER RISK MANAGEMENT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CybercrimeTrends 2024 The latest threats and security best practices
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Threat Intelligence Guide – What Is Cyber Threat Intelligence and How Is It Used?
This guide provides an introduction to Cyber Threat Intelligence — CTI. It provides accessible advice on the theory and practice of CTI products and services. It...
Cyber Security Politics Socio-Technological Transformations and Political Fragmentation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Surviving a Massive cyber-attack by Cigref
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Common Windows, Linux and Web Server SystemsHacking Techniques
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Sync Scheduler Stealer
At CYFIRMA, we are dedicated to providing current insights into prevalent threats and strategies utilized by malicious entities, targeting both organizations and individuals. This in-depth examination...
SPLUNK® AND THE CIS CRITICALSECURITY CONTROLS Mapping Splunk Software to the CIS 20 CSC Version 6.0
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SSH Penetration Testing Port_22
The SSH protocol, also known as Secure Shell, is a technique for secure and reliable remote login from one computer to another. It offers several options...
Source Code Analysis Scenarios
The “Source Code Analysis Scenarios” document provides an in-depth examination of various vulnerabilities within software applications, emphasizing the importance of addressing even lower-severity vulnerabilities due to...
SOC SIEM Use Cases
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SOC -Security Operations Centre Framework Project
The SOC Framework document provides an extensive guide on structuring and operating a Security Operations Center (SOC), detailing different strategies such as centralized, distributed, in-house, constituency,...
Six Pillars of DevSecOps- Collaboration and Integration
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SOC a Business Perspective
The information security landscape has shifted tremendously over the past decade. Information security threats have been increasing exponentially both in numbers as well as complexity. To...
WatchTower I ntelligence-Driven Threat Hunting
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SEGURIDAD DE LA INFORMACION
¿Qué es la Seguridad de la Información? La seguridad de la información es un concepto que se involucra cada vez más en muchos aspectos de nuestra...
Security of Personal Data
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Configuration Management (SCM)
Security Configuration Management (SCM) is a critical aspect of cybersecurity that involves the systematic management and control of an organization’s information system configurations to ensure their...
Securing ICS SCADA updates OT Environments
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Secure Coding Cheatsheets
In today’s interconnected digital landscape, security is paramount for developers across various platforms and programming languages. With cyber threats evolving rapidly, ensuring the security of software...
Secrets Management Maturity Model
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Smart Cities & Critical Infrastructure Framework
The Internet of Things Security Institute is a Not for Profit academic and industry body dedicated to providing security frameworks and supporting educational services within an...
Sample Penetration Test Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Safeguarding Brain Data: Assessing the Privacy Practices of Consumer Neurotechnology Companies
For decades, scientists and healthcare professionals have employed neurotechnologies to understand the complexities of the human brain and pioneer cutting edge medical treatments. Neurotechnologies, which are...