Source: www.csoonline.com – Author:

News Analysis
10 Oct 20245 mins
CyberattacksEmail SecurityHacking
New phishing campaigns attempt to evade detection by constructing rogue QR codes with special ASCII characters and load phishing pages locally using the local blob URL feature in browsers.
Attackers are always looking for new ways to bypass email security filters and get their malicious URLs in front of victims. One increasingly popular method involves sending emails that include QR codes that direct users to rogue sites when scanned — and now researchers have found a variation in which those QR codes are built using ASCII and Unicode characters arranged in HTML in place of static images.
This technique (sometimes called quishing) aims to bypass security filters that have optical character recognition (OCR) capabilities to detect QR code inside images and then inspect the URLs to which they point. The ASCII method makes OCR-based detection useless because a string of special characters in emails will be meaningless to an OCR engine and indistinguishable from a QR code to a human.
Attackers are also increasingly using so-called blob (binary large object) URLs that only open in the local browser to render phishing pages instead of using URLs that point to external pages that could be blacklisted by security software.
Spoofing a QR code with ASCII makes it hard to detect
“A year ago, the volume of QR code-based phishing attacks suddenly increased,” researchers from Barracuda Networks said in a report. “Barracuda data shows that around one in 20 mailboxes were targeted with QR code attacks in the last quarter of 2023.”
These phishing emails usually masquerade as automatic notifications from legitimate services and include a QR code for the user to scan with their mobile device to access a resource, such as an invoice, document, or shipment tracking page.
QR codes were appealing to attackers as a phishing vector in the past because many spam and security tools were not equipped to detect them, since QR codes are just images inside HTML-based email messages.
However, tools have adapted and now use OCR engines to analyze static images in emails and decode QR codes if detected to extract the URL. So, it’s not surprising to see attackers adapt their strategy too.
According to Barracuda, some recent QR-based phishing campaigns have used ASCII full-block and half-block characters, which show as a 49×49 black square and a half-black square respectively in order to visually construct functional QR codes by arranging these characters in HTML code and using other techniques.
“Wherever white patches are needed in the QR code, cascading style sheet (CSS) is used to make the text color of the block characters fully transparent, rendering them invisible,” the researchers said.
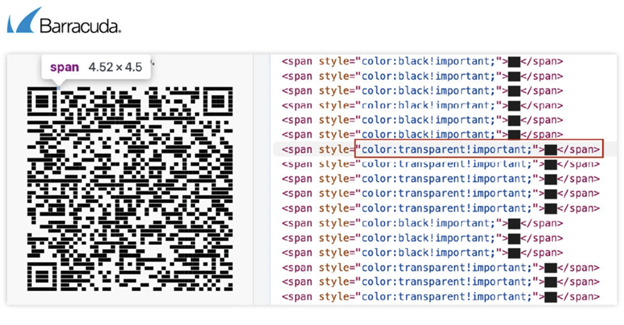
An example of a QR code built using ASCII
Barracuda Networks
Attackers are impersonating legitimate services
In one phishing example demonstrated by Barracuda, attackers impersonated a service that supposedly sent a payroll and benefits enrolment file that could be accessed by scanning the QR code. In another case, the attackers impersonated global shipping company DHL and asked recipients to fill out a form by scanning the QR code to complete an order because the shipping address was supposedly missing.
One might think it would be easy to build a detection rule for this by just looking for blocks and half-blocks, but it’s not that simple. According to the researchers, there are 32 distinct ‘block’ characters that include full blocks, partial blocks and quadrants and they can further be encoded inside emails using HTML Entity, UTF-8 Encoding, or UTF-16 Encoding, creating 96 possible combinations. And many of them have legitimate use cases, increasing the likelihood of false positive detection.
“Additionally, in the case of HTML Entities, each ‘block’ can have multiple representations, and attackers can use single blocks or block combinations to generate their ASCII/Unicode-based QR codes,” the researchers said. “This all increases the total number of possible combinations and makes ASCII-based QR codes challenging to detect.”
Abusing blob URLs
Blob functionality is part of a browser’s File API and provides a way for websites to store and access file-like objects that contain raw data in the browser’s memory. This can be used to work with images and videos locally inside the browser during the same session without requesting those resources from an external server every time they are referenced in the code.
The browser will create Uniform Resource Identifiers (URI) of the form blob://http://domain.com/[unique_blob_identifier] to reference these objects in memory and attackers are taking advantage of this because not all security tools apply their detection mechanisms on blob:// URIs, since they are temporary and local to the user’s browser. This doesn’t mean they can hold phishing pages through.
The Barracuda researchers recently encountered a phishing campaign that impersonates find credit card provider Capital One and asks users to click on a button to review their account, which has allegedly been restricted due to suspicious activity.
If clicked, the button leads to an intermediary page that triggers the blob functionality to store a binary object then quickly redirects the browser to the local blob:// URL to load it. In this case, the binary object is used to store a fake Capital One login page.
“Threat analysts have also noticed the Blob URI technique being used in phishing attacks impersonating Chase and Air Canada,” the researchers said.
SUBSCRIBE TO OUR NEWSLETTER
From our editors straight to your inbox
Get started by entering your email address below.
Original Post url: https://www.csoonline.com/article/3557585/attackers-are-using-qr-codes-sneakily-crafted-in-ascii-and-blob-urls-in-phishing-emails.html
Category & Tags: Cyberattacks, Email Security, Hacking, Phishing, Security – Cyberattacks, Email Security, Hacking, Phishing, Security
Views: 1



















































