Source: grahamcluley.com – Author: Graham Cluley
Hot on the heels of MacStealer and the development of a version of the notorious Lockbit ransomware for Macs comes another malware threat for Apple fans.
Security researchers at Cyble are warning that cybercriminals have developed a new malware threat which can steal highly sensitive data from the Mac computers it infects.
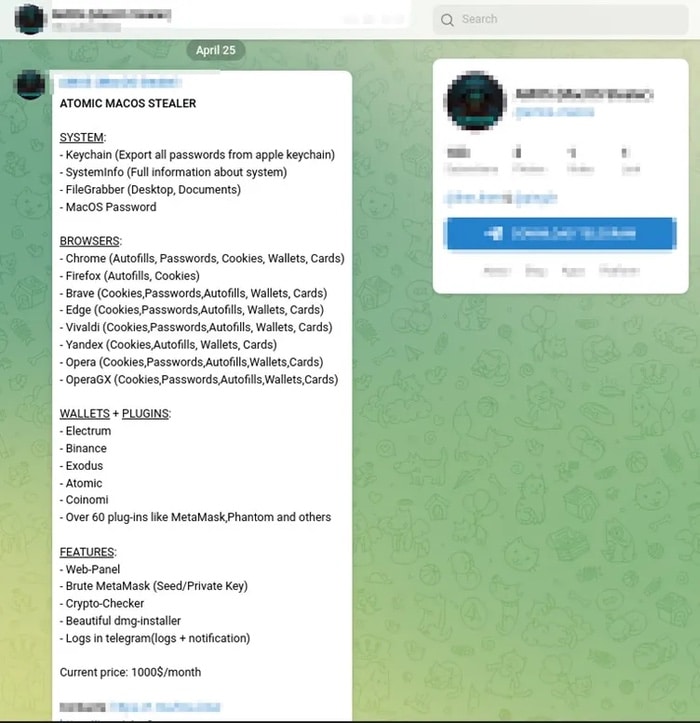
The malware, named Atomic Stealer by researchers, can a steal a wide variety of information from compromised Macs:
- keychain passwords
- system information
- files from the Desktop and Documents folders
- the computer’s password
- web browser auto-fills, passwords, cookies, and payment card information
In addition, Cyble’s team says that Atomic Stealer can “target cryptowallets such as Electrum, Binance, Exodus, Atomic, and Coinomi.”
Clearly, any information which could lead to a investor’s cryptocurrency wallet being compromised could lead to significant financial losses.
The group behind Atomic Stealer has been advertising the capabilities of the malware on a Telegram channel, and also selling for $1000-per-month access to a a suite of web-based features including a command-and-control dashboard of infected devices, and tools to brute force access to the popular MetaMask cryptocurrency wallet.
Mac users are advised to always take care about where they choose to source their software – avoiding pirated software and cracks. Downloading from a trusted software developer’s website or using the official Mac App Store is generally a much safer choice.
Atomic Stealer is one of the latest examples of malware being written using Golang (Go), which has proven increasingly popular amongst financially-motivated cybercriminals, and in particular those who wish to easily use the same code to build threats for Windows, macOS, and Linux.
For more information check out the technical blog post by Cyble.
Found this article interesting? Follow Graham Cluley on Twitter or Mastodon to read more of the exclusive content we post.
Graham Cluley is a veteran of the anti-virus industry having worked for a number of security companies since the early 1990s when he wrote the first ever version of Dr Solomon’s Anti-Virus Toolkit for Windows. Now an independent security analyst, he regularly makes media appearances and is an international public speaker on the topic of computer security, hackers, and online privacy.
Follow him on Twitter at @gcluley, on Mastodon at @[email protected], or drop him an email.
Original Post URL: https://grahamcluley.com/atomic-malware-steals-mac-passwords-crypto-wallets-and-more/
Category & Tags: Apple,macOS,Malware,MetaMask,wallet – Apple,macOS,Malware,MetaMask,wallet
Views: 0